What is Role-Based Access Control (RBAC)?

Quick Answer: Role-based access control restricts resource access based on a user's role in an organization. It improves security and limits access to only required resources.
In the IT security industry, there is something known as the C-I-A Triad. It’s the cornerstone of IT security, as well as a key knowledge objective in many security and networking certification exams, such as CompTIA Security+ and Network+.
This article will focus on a concept specific to one component of the C-I-A Triad: Confidentiality. Role-based access control, or RBAC, is a method used to control access to sensitive resources such as data and servers, ensuring resources are accessed and modified only by those who should have the capability to do so.
This article will introduce you to role-based access control as a concept, as well as teach you how to implement RBAC. Additionally, you’ll learn about some best practices when implementing and maintaining RBAC to help ensure your resources are properly secured.
What is Role-Based Access Control?
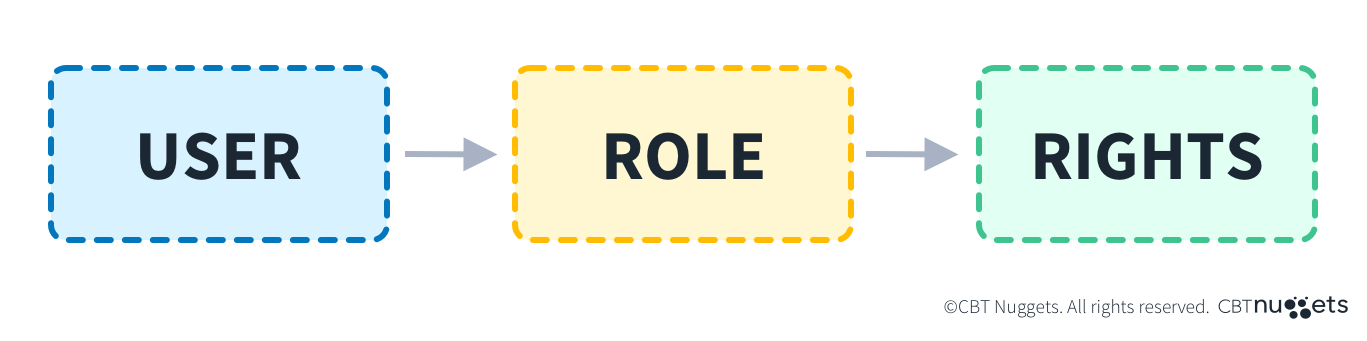
Role-based access control is a security model used to restrict resource access by a user’s role within the organization, making overall access controls easier to maintain compared to modifying access permissions on a per-user basis. RBAC works by assigning permissions to roles, and then assigning users to roles as needed.
For example, permissions to access a company’s financial data might be assigned to the finance role, and members of the accounting department would be assigned to the finance role, thus being granted access to the company’s financial data.
There are three components to role-based access control:
Roles
Roles are used to define users as sets of permissions. Examples of roles might include Finance, Guest, and Admin. These roles would have permissions granted to them, and users assigned to them.
Users
Users are individuals assigned to various roles. Their role(s) determine the resources they can access.
Permissions
Permissions are the levels of access granted to specific roles. Some of these permissions may include “read-only,” “write,” and “execute.”
How RBAC Differs from Other Access Control Models
RBAC is a great middle-ground compared to other methods of access control. Two other access control models include Discretionary Access Control (DAC) and Mandatory Access Control (MAC).
DAC offers more flexibility than RBAC, but only to the point that it risks granting access to the wrong people. Discretionary access control allows resource owners to grant permissions to other users, which complicates User Access Reviews (UAR).
MAC, on the other hand, is too restrictive compared to RBAC. Mandatory access control grants permissions based on security policies and labels, which can leave some users without permissions when they need them.
What are the Advantages of Role-Based Access Control?
RBAC provides several advantages over other access control methods like DAC and MAC by being easier to scale, easier to manage, and easier to audit. RBAC is incredibly easy to scale because as users come and go, they can be added to and removed from roles as needed, and since the roles are what grant permissions, it’s as simple as adding and removing users.
RBAC is one of the simpler access control methods to manage because permissions are assigned to roles, and users are placed within those roles. Granting permissions to new users, users transferring departments, and users who need cross-departmental access is as simple as placing a user within a role (or multiple roles), and the same works for removing a user’s permissions. This simplifies both management and user access reviews.
RBAC’s ease of use makes compliance audits simple, too. User Access Reviews are a common requirement for many compliance frameworks, and accessing user permissions is easy with RBAC. To do so, just validate which group(s) a user belongs to, and what permissions have been granted to those groups.
How to Implement Role-Based Access Control
Properly implementing RBAC requires planning and is best done in phases.
Planning and Design Phase
During the planning phase, outline your goals and ensure you have the necessary resources. This phase should include:
Identify roles and responsibilities: The first step in planning your RBAC implementation is to identify the various roles and responsibilities within your organization. This is the foundation of RBAC within the organization.
Map permissions to roles: After roles have been defined, map appropriate permissions to the correct roles. This should be done with careful consideration, as you don’t want to be overly permissive, or so restrictive as to impede work.
Create RBAC policies: Once roles and permissions have been defined, concise policies are needed to ensure RBAC is implemented and enforced appropriately.
Implementation Phase
Once you have a plan in place, it's time to move on to implementation. During this phase, you will:
Deploy RBAC mechanisms: The first step in the implementation phase is to deploy any necessary platforms or tools that will enforce your RBAC policies. Whether you are integrating RBAC into an existing environment or building something new, careful attention should be paid to this step.
Integrate RBAC with existing systems: Ideally, this will be tested before being rolled out to a production environment. However, you’ll need to integrate RBAC with the other tools within your environment.
Testing and validation: Even if you tested RBAC before full production deployment, it’s crucial to test once it’s in production to ensure it functions as expected. Ensure privilege escalation isn’t possible where it shouldn’t be, and confirm policies are being applied and enforced as intended.
Maintenance Phase
Once RBAC is put into place, you'll still need to ensure it stays up and running. Maintenance of RBAC should include:
Regular review and updates of RBAC policies: Perform regular reviews of your existing policies, and evaluate whether new policies or groups need to be added to fit your organization’s needs as roles, permissions, and resources evolve.
User provisioning and deprovisioning: Be sure to adjust access as users are onboarded and offboarded, as well as when roles change. A user’s level of access should always match their current needs based on their job function.
Auditing and monitoring access: Periodic audits help validate RBAC is being properly managed and enforced. Further, regular monitoring can help identify potentially malicious behavior.
What are the Best Practices for Role-Based Access Control?
RBAC as an access control method is only as effective as its implementation and regular maintenance allows. Here are some best practices to follow.
Principle of Least Privilege
Regardless of which access control methods or policies your organization uses, always grant the least amount of access absolutely necessary to perform that user’s job functions. This helps reduce the potential impact of insider threats and prevents users from making mistakes with resources.
Regular Reviews and Updates
Role-based access control requires regular user access reviews and updates. Ensure your organization is promptly removing users who leave the organization, and regularly confirm current assignments are appropriate.
Separation of Duties
Enforcing separation of duties is critical to reducing risk. No one user should have access so permissive as to enact too much change on their own. Without proper separation of duties, an organization opens itself up to risks of critical mistakes, fraud, and more capable insider threats.
Training and Awareness
Employees should be trained and made aware of the importance of access control policies and how they’re enforced within your organization. This helps everyone understand why they have access to specific resources, why they’re restricted from others, and how to request additional access.
Leveraging Automation and Tools
Tools and automation can help make your RBAC policies more effective, as well as help improve the efficiency of your organization’s periodic access reviews.
Conclusion
Role-based access control is a vital tool organizations can use to restrict access to resources properly. Within RBAC, permissions are granted to specific roles, then users are assigned to those roles and inherit the permissions those roles have been granted. RBAC offers more flexibility and scalability than other methods of access control, such as Discretionary Access Control and Mandatory Access Control.
Check out our online cybersecurity training to learn about other types of access control.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.