The 3 Most Common Security Issues in Cloud Environments

Securing the cloud is increasingly complex. After all, there is much to think about — databases, virtual machines, CI/CD pipelines, and more are all potential vectors of attack.
That said, security is not just the responsibility of the end user. The Cloud Service Provider (CSP) shares some of the security burdens in what is called the Shared Responsibility Model. In this article, we’ll review the three most common security issues and offer strategies to prevent them.
But first, let’s talk a little bit about the Shared Responsibility Model and how you can use it to wrap your mind around cloud security.
Level Up Your Security Skills Today
Cyberthreats are increasing not only in frequency but complexity. So the demand for professionals who can keep networks and data protected and safe continues to increase. You’ll find the training you need to develop and hone in-demand security skills at CBT Nuggets.
Whether you are new to cybersecurity or a seasoned network security pro, our courses can get you up to speed on the latest security technologies and best practices. Much of our online cybersecurity training maps to highly valued certifications — and covers skills that many organizations desperately need. Not a CBT Nuggets subscriber? Sign up for a 7-day free trial to get a feel of what it’s like to learn IT with us. Explore all of our cybersecurity training and start learning skills that can help you keep networks and data safe!
What is the Shared Responsibility Model?
Every CSP has a Shared Responsibility Model that divides the onus of security between the end user and the provider. For a better understanding, let’s take a look at the following illustration. While it is specifically for AWS, this basic principle applies to all CSPs.
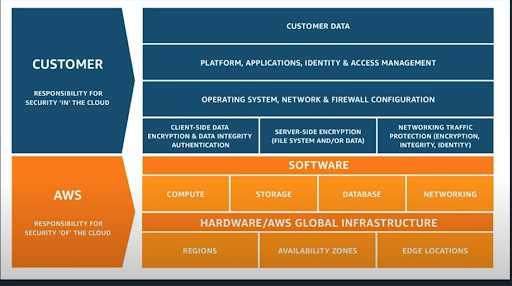
Source: AWS Shared Responsibility Model
As you can see, the CSP is responsible for all the “low-level” operations, such as hardware and networking. The customer is responsible for Identity Access and Management, customer data, OSs and so on. A good way to think about it is this—the customer is responsible for anything that is created within the cloud, but not the cloud itself. So for instance, the customer is not responsible for patching a VM, but they are responsible for who can access it.
Now that we have some context about the broader responsibilities of the customer, let’s talk about the common cloud security issues customers will face.
Related: 5 Best Ways to Evaluate an Organization's Security Posture.
1. Misconfiguration
Hands down, the biggest issue with the cloud is the misconfiguration of resources. That falls in layer three of the customer end of the Shared Responsibility Model.
For example, one common misconfiguration is data storage. CSP’s data storage is often defaulted to private, meaning only authorized users can access it. However, you can make it public accidentally. For example, in 2017, the Pentagon made their storage information public through misconfiguration. If it can happen to the Pentagon, it can happen to you.
Another great example is developers will often expose APIs without the proper configuration. Meaning any Average Joe on the internet can execute a GET request on a URL to retrieve valuable information.
What can you do to prevent cloud misconfiguration?
In order to prevent these mishaps, make sure all resources have the appropriate privileges and access controls. Also, verify the access you are giving a resource. It is also a good idea to have multiple people verify the configuration.
Additionally, CSPs have services that will scan your resources to ensure they are configured to best practices. AWS Config is the service run by Amazon, but Google, Azure, and Oracle have their versions as well.
Lastly, developers tend to use default credentials on resources for ease of development. Never use default credentials in production environments! It is the first thing hackers will try.
2. Account Hijacking
Account hijacking is a bigger problem now that many IT professionals are working remotely. After all, no one actually sees the employees at work—the system is only guarded by a VPN and a password. Cybercriminals do not need to be on-premises to steal accounts and pretend to be an employee, so they are taking advantage of the anonymity of remote work.
Often threat actors will use tried-and-true methods, such as phishing, to steal cloud credentials. They purchase the credentials on the Dark Web. Or they use misconfigured resources to obtain protected information.
What can you do to prevent account hijacking?
The most important way to prevent account hijacking is to implement Multi-Factor Authentication (MFA), which relies on the user knowing something and having something. For example, the user knows their password and they have a phone to receive push notifications.
Another good idea is to implement Zero Trust, a security framework that requires all users inside and outside the organization to be continuously authenticated and validated.
3. Identity and Access Management Inconsistencies
The last major security issue has to do with provisioning users. One of the drawbacks to cloud development is that when resources are scaled, problems scale too. So, when a user is created in the cloud with overly permissive access, it can potentially give the user access to hundreds of resources.
Most cloud Identity and Access Management (IAM) is accomplished through Role-Based Access Control (RBAC). When a user is created, he or she is assigned a role based on their profession. So for example, a developer is given the developer role, but that means role misconfiguration could grant every developer overly permissive access, leaving the organization exposed to internal cyberattackers.
What can you do to prevent IAM inconsistencies?
It is important to consistently review RBAC roles. The needs of the organization constantly evolve — and access evolves right along with it. For example, if a database’s responsibility transfers from one team to another, the access rights must transfer correctly too. You cannot just add another team without also removing the first team.
Additionally, make sure all IAM roles are version controlled. That way errors can easily be rolled back and effectively audited.
Interested in earning security certifications or beefing up your cybersecurity knowledge? We offer a wide range of courses to support your development.
See what we’ve got (and even take a course) for FREE by signing up for a one-week no-strings-attached trial.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.