What is a Zero-Day Vulnerability?

Quick Definition: A zero-day vulnerability is a security flaw in software that is unknown to the vendor and is actively exploited before a patch is available.
Imagine waking up to the news that a new security exploit has been unleashed, allowing hackers access to countless systems worldwide. No one saw it coming, and there's no patch available.
This is the reality of zero-day vulnerabilities, security flaws that are discovered and exploited before anyone knows they exist. They pose a serious threat when used by cybercriminals and state-sponsored attackers alike.
Today, we'll explore zero-day vulnerabilities to better understand how they are discovered and exploited—and how to prepare to defend your organization.
What are Zero-Day Vulnerabilities?
The term "zero-day" refers to the fact that we're dealing with vulnerabilities that vendors or open-source maintainers have had zero days to fix before being actively exploited in the wild. Like any other vulnerability, they can come from coding errors, misconfigurations, overlooked security bypasses, misimplementation of libraries, or any number of other software mishaps.
They can remain hidden for years, installed in unknown numbers of internet-connected systems across the world. Once discovered, the race is on between hackers and the good guys to mitigate the risk.
Zero-days can take the form of any kind of vulnerability that you can think of. Remember, these are not specific types of vulnerabilities; the term just describes any previously unknown flaw. So types of vulnerabilities like SQL injections, buffer overflows, remote code executions, bypassing encryption, and more can all be zero-days.
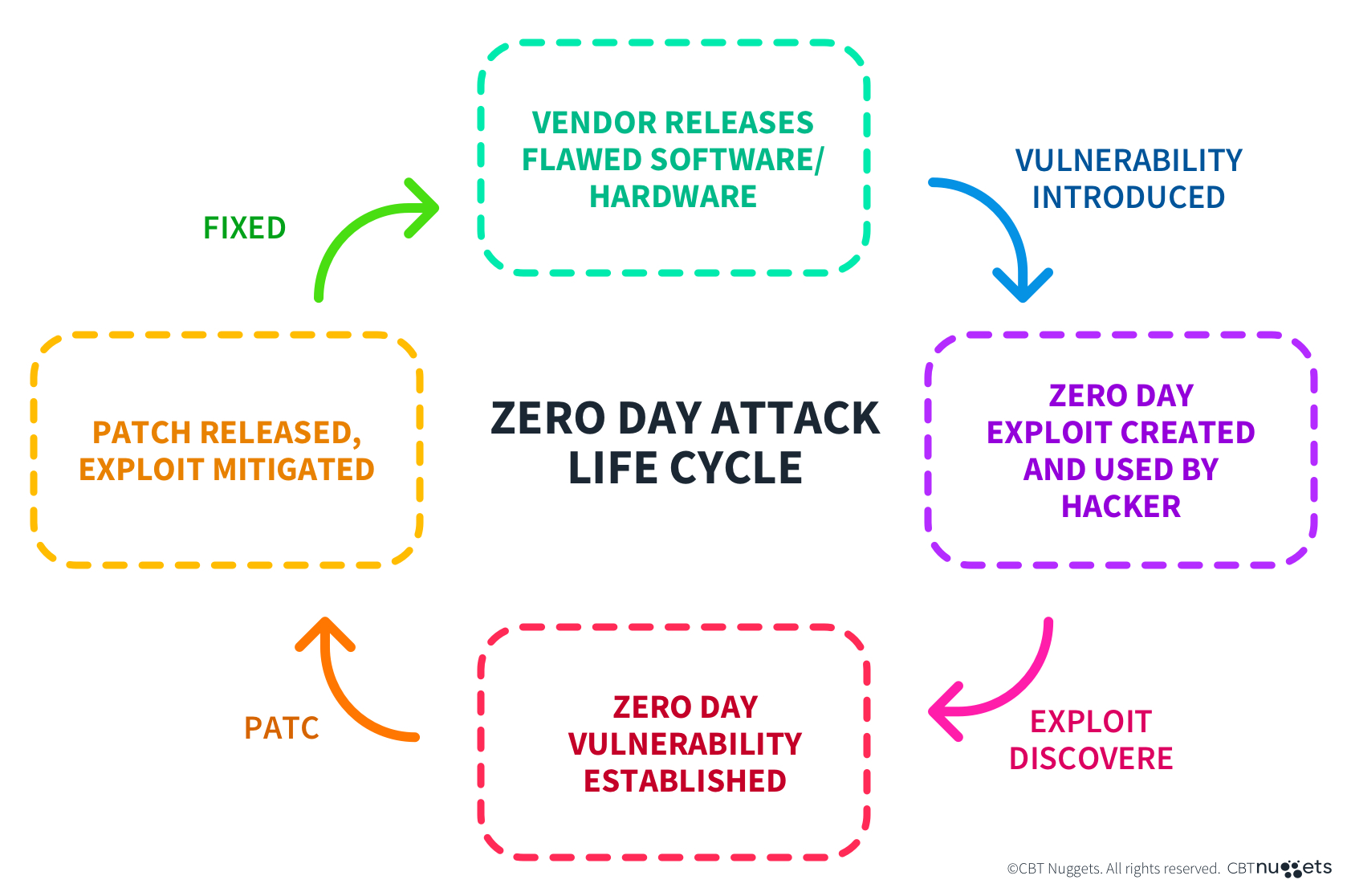
Lifecycle of a Zero-Day
Once discovered, the lifecycle of a zero-day moves quickly, as the vulnerability is often already being exploited in the wild—leading to data theft, unauthorized shell access, ransomware infections, or a range of other attacks depending on its nature. The longer vulnerable systems remain online and unpatched, the more likely they are to be exploited.
A common lifecycle looks like this:
Vendor becomes aware of a zero-day impacting their product (often because of an attack or data leak.)
Emergency development work is done to write and release a patch.
The vendor communicates with customers regarding the zero-day and patch.
Follow-up support is offered to help customers monitor their environments, logs, etc.
Different vendors will respond in different time frames depending on their agility and commitment to security. Still, anything less than two or three business days for a patch is considered unacceptable for a critical issue.
Zero-Days in Action
There have been several high-profile zero-days over the years. Heartbleed, an infamous flaw in OpenSSL, allowed attackers to read decrypted information stored in memory, possibly leaking passwords, tokens, or other sensitive data. Shellshock, a flaw in Bash, allowed remote execution of arbitrary commands. Both of these were found in core Linux server components, so before patching, there were likely millions of vulnerable servers across the internet.
Others include WannaCry, which preyed on the Windows SMB service to spread ransomware to an estimated 300,000 servers worldwide. Log4Shell exploited the Log4j library to allow remote code execution. A heap buffer overflow in Google Chrome allowed for remote code execution via Javascript simply by victims visiting a malicious website. Stuxnet exploited multiple Windows zero-days and was allegedly developed by the NSA to target ICSs enriching nuclear material in Iran (a fascinating story for another day). Suffice it to say, this isn't a new or unique problem.
Use Cases
Zero-days have been used against governments, corporations, financial institutions, and basically any organization running vulnerable systems. They are used to cause outages, data breaches, or financial losses. Nation-state actors, hacker groups, or lone black hats all have exploited zero-days for their own reasons.
Exploit Marketplaces
These vulnerabilities are not just security risks; they are valuable commodities in a thriving black market. Exploits are bought and sold for big money to give cybercriminals a leg up in launching their attack campaigns.
In reaction, many big tech companies offer bug bounty programs. These programs pay for the responsible reporting of vulnerabilities in their products. They incentivize private disclosure over attacking targets or black market sales and motivate researchers to work with companies to test and improve their security.
Detecting and Mitigating Zero-Days
A good offense always starts with a good defense, and defense against zero-days is no exception. There are a number of best practices that you should already be following. The CompTIA Security+ certification will cover lots of these, but here's a primer. To start, don't expose any systems to the internet except the bare minimum needed. Do the same with ports—only open what’s required.
Proactive Defenses
Adopting specific proactive measures will go a long way. Keep OSes, software, and dependencies up to date with a well-defined patch management strategy. Perform and review regular host scans to identify vulnerabilities.
For in-house developed software, a strict code review policy is a must, along with DAST (Dynamic Application Security Testing) and SAST (Static Application Security Testing) scanning to catch issues with code or dependencies before they hit prod.
Reactive Defenses
Along with being proactive, you must be reactive to deal with threats when they come. Build up your perimeter security, including WAFs to detect and block suspicious web application traffic, and IDS/IPS systems to broadly monitor all traffic for unusual activity. Have a plan for remediation, including emergency patching when a critical issue cannot wait for a maintenance window.
Finally, if trouble does find you and none of your defenses hold, having a well-defined incident response plan is critical to respond, minimize downtime, and identify any disclosure or legal hurdles that must be addressed. It’s not the fun stuff, but planning ahead is better than scrambling during a crisis.
Final Thoughts
Zero-day vulnerabilities are among the most dangerous security threats, as they are exploited before patches are available. We can take measures to lessen the risk, but they require serious proactive planning and preparation for reactive action.
Zero-day vulnerabilities are unpredictable, maintain a high value in the black market, and are potentially very dangerous. However, with lots of work and a little luck, you can minimize their impact on your organization.
Want to learn more about cybersecurity? Check out our CompTIA Security+ online training to learn more.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.