What are Encryption Standards? WPA & WPA2

Quick Answer: Wi-Fi Protected Access (WPA) is a security protocol designed to safeguard wireless networks by encrypting data during transmission. It prevents unauthorized access, ensures data confidentiality, and maintains integrity, evolving through WPA2 and WPA3 for enhanced security.
Nothing is worth doing if it is not done securely. No one would build a bank without security cameras, and no one should use WiFi without encryption. Unfortunately, WiFi is especially vulnerable since it's transmitted through the air. Due to this inherent vulnerability, encryption standards have been developed around it.
The most common WiFi security standard is WPA (Wireless Protection Access). WPA and its variants are crucial knowledge for the Network+ and CCNA exams. So, let's discuss what WPA is, how it works, and some best practices.
What is WiFi Protected Access (WPA)?
WPA is a security protocol designed to protect wireless data during transmission. It's focused on achieving four goals:
Prevent unauthorized access: Encryption ensures hackers cannot access unauthorized resources.
Protect data confidentiality: WPA encryption verifies intruders cannot peek into the data.
Maintain data integrity: WPA verifies the data has not been tampered with once it gets to its destination.
Support regulatory compliance: WPA encryption provides regulatory compliance in industries with high standards.
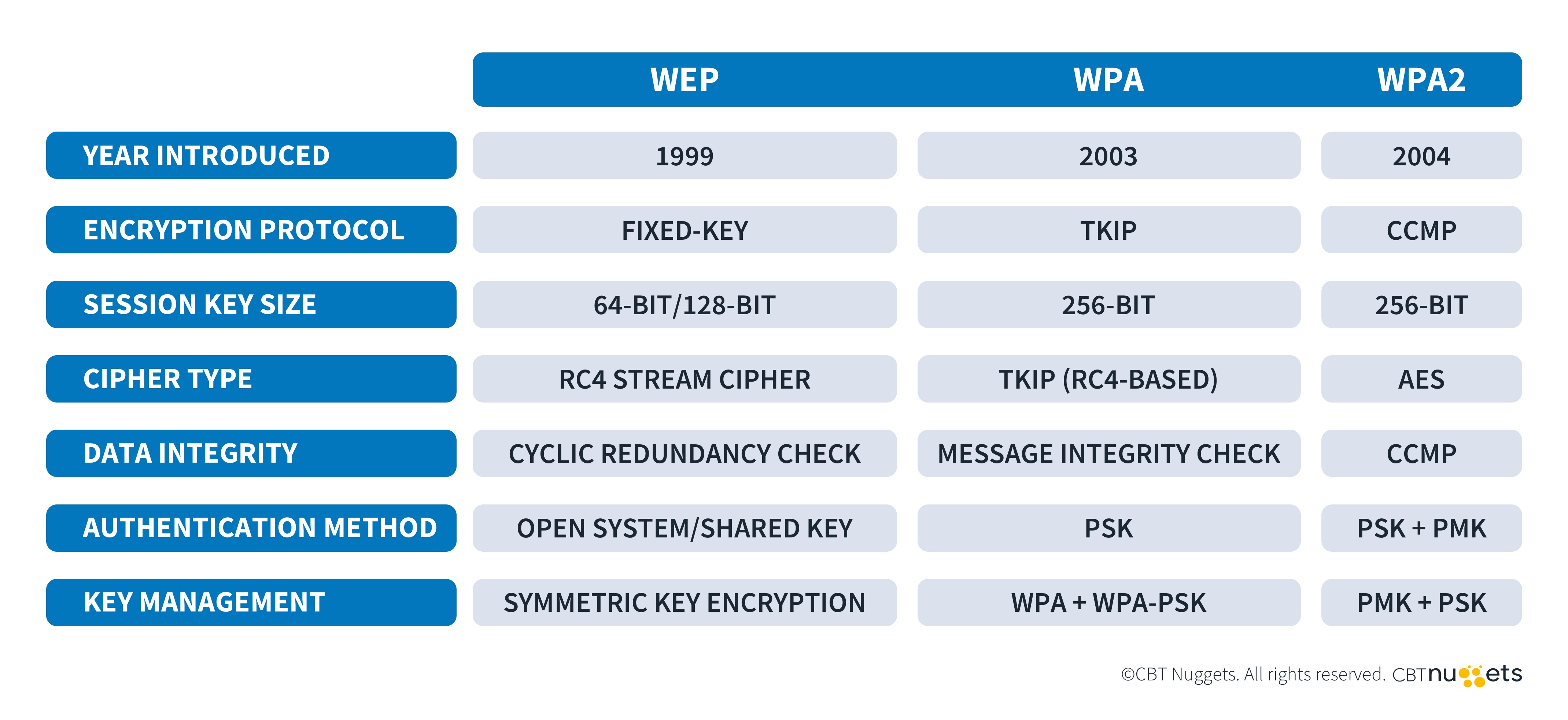
WPA has also made great strides in fulfilling each of these goals. However, prior versions had become vulnerable and have been replaced. The initial version of WPA used a key protocol called TKIP (Temporal Key Integrity Protocol). WPA version 2 replaced TKIP with AES due to TKIP's weak encryption algorithm (RC4).
WPA2 is far more secure than WPA1 and remains widely used today. WPA2 introduced 802.1x authentication protocol for enterprise networks, which improves user verification.
Finally, WPA3 was introduced in 2018. It provided numerous security enhancements, particularly against brute-force attacks. With this evolution in mind, let's explore some of the finer points of the most widely used iteration, WPA2.
What is WPA2 Personal (AES/TKIP)?
WPA2 personal is a widely used variant of WPA2 for homes and small businesses. It yields several benefits, such as ease of setup, shared passphrase, and high-security standards. While entering a password to access a Wi-Fi network is common for WPA2, it doesn’t guarantee that WPA2 is being used. Other protocols, like WPA or WPA3, can also require a password.
AES is a highly secure encryption algorithm that serves as the backbone of WPA2. It works by encrypting data into unreadable ciphertext. It uses a symmetric key to encrypt and decrypt the text. If you use WireShark to sniff data encrypted by AES, it will be completely unreadable unless you have the encryption key.
Installation and Configuration Steps
Setting up WPA2 in your environment is a fairly easy process, but it can still be involved. Let's go over what you'll need and how to set it all up, step-by-step.
To start, you'll need a WiFi access point and at least one wireless device such as a laptop or a smartphone. The WiFi access point is generally something like a Cisco WAP 100. Then, make sure you have admin access to the access point--that's crucial for setting it up.
Configure WPA/WPA2 Personal on a WAP 100
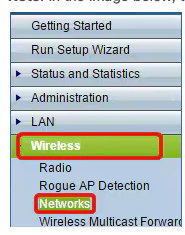
Step 1: Log in to the web-based utility of your access point and choose Wireless > Networks. Note: The image below shows the web-based utility of the WAP361. Menu options may vary depending on your device's model.
Step 2: Under the Virtual Access Points (SSIDs) area, check the checkbox of the SSID you want to configure and click Edit.
Step 3: Click WPA Personal from the Security drop-down list.
Step 4: Check the checkbox to select the WPA version (WPA-TKIP or WPA2-AES). You may choose two at once.
WPA-TKIP—Wi-Fi Protected Access-Temporal Key Integrity Tool: Some client stations on the network only support the original WPA and TKIP security protocols. Per the latest Wi-Fi Alliance requirement, choosing only WPA-TKIP for access points is not allowed.
WPA2-AES — Wi-Fi Protected Access-Advanced Encryption Standard: All client stations on the network support WPA2 and AES-CCMP cipher/security protocol. This WPA version provides the best security per IEEE 802.11i standard. As per the latest Wi-Fi Alliance requirement, the WAP has to support this mode all the time.
Step 5: Create a password consisting of 8-63 characters and enter it in the Key field.
Step 6: Click Save.
You have now configured WPA Personal on your WAP. For more information, refer to the official Cisco instructions. Note that this is how to configure WPA only on a Cisco access point. Other access points will work similarly—reference documentation for the exact steps.
What is WPA/WPA2 Enterprise (AES/TKIP)?
WPA2 Enterprise is similar in many respects to Personal but meant for a much larger audience. It handles authentication via a RADIUS server instead of through a username and password. WPA2 interacts with the RADIUS server using the Extensible Authentication Protocol (EAP). Basically, WPA2 provides individual access by device instead of via a username and password.
The biggest difference with WPA2 is you will need a RADIUS server for authentication. Other than that, you'll need an access point and wireless device to connect.
Configure WPA/WPA2 Enterprise on a WAP 100
To configure WPA2 Enterprise, you need to complete steps one and two, as mentioned above. So, let's start with step 3.
Step 3. Choose WPA Enterprise from the Security drop-down list.
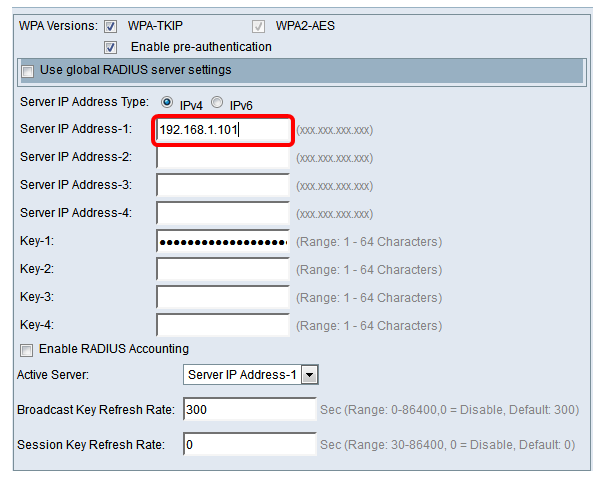
Step 4. Choose the WPA version (WPA-TKIP, WPA2-AES, and Enable pre-authentication). Generally, you'll want to choose WPA2-AES.
Step 5. Enter the IP address of the RADIUS server in the Server IP Address field.
Step 6. In the Key field, enter the password key corresponding to your RADIUS server that the WAP uses to authenticate to the RADIUS server. You can use from 1 to 64 alphanumeric and special characters.
Step 7. Click save.
And there you have it. These instructions should get you where you need to be regarding WPA2 Enterprise.
Best Practices for WPA & WPA2 Secure Deployment
A number of best practices can be implemented to ensure a smooth deployment. Let's highlight four of the best ways to ensure you're in ship shape to start accepting traffic.
Regular Updates and Patch Management
Update software, firmware, and operating systems regularly when required. When possible, edit the settings on your devices to ensure updates occur automatically. Remember to always smoke-test your system after an update. Sometimes, even the simplest update can go wrong.
Strong Password Policies
Enforce complex passwords that can't be easily guessed. When possible, set expiration dates on passwords. Lastly, implement multi-factor authentication (MFA) whenever possible.
Monitoring and Intrusion Detection Systems
If possible, install Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). It's also a good idea to review system logs regularly for anomalous activity. Splunk and Grafana are great tools for aggregating and visualizing that sort of data. Finally, set up alert monitors for suspicious activities.
Employee Training and Awareness
Regular training on security threats should be conducted with employees. Make sure they know how to spot phishing emails, ransomware, social engineering, and more. Perform incident response drills to ensure employees know exactly what to do when a large-scale event occurs.
Final Thoughts
In today’s interconnected world, securing wireless networks is not a luxury—it’s a necessity. The vulnerabilities of wireless communication require strong safeguards like WPA, which plays a crucial role in protecting data from unauthorized access and tampering.
Understanding the nuances of WPA2 Personal and WPA2 Enterprise is essential. Remember that Personal uses a shared password, while Enterprise uses a RADIUS server.
Follow best practices such as updates, strong password policies, and continuous monitoring. Shore up your employees' knowledge with regular updates. Implementing these steps can reduce the risk of breaches and increase network resiliency.
Network security is not a one-time effort but an ongoing process of vigilance, adaptation, and education. Investing in robust Wi-Fi security now can save you from costly mishaps later.
Want to learn more about becoming a Cisco Network Administrator? Consider our CCNP Training!
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.