What is an Industrial Control System?

Quick Definition: Industrial Control Systems (ICS) manage the instrumentation and controls that automate industrial processes such as oil refineries and pipelines, water treatment plants, manufacturing robots, and assembly lines.
Today’s network admins must manage and secure complex topologies that encompass many technologies and can span multiple, widely dispersed locations. One technology that network admins may encounter is the Industrial Control System (ICS).
Historically, ICS were separate from general information systems and networks, but they are now increasingly integrated with the main corporate network. As a result, they are also increasingly at risk from cyberattacks, as reflected in the exams for certifications such as CompTIA’s Network+.
What are Industrial Control Systems (ICS)?
Industrial control systems (ICS) manage the operation of plant equipment used in manufacturing and process control, such as automated manufacturing lines, flow control in the production of petrochemicals, power generation, and water treatment plant management.
And it’s not just in manufacturing—you’ll find examples of industrial control systems in almost every sector, from education to transportation to real estate and hospitality.
Fundamentals of Industrial Control Systems
ICSs monitor and manage the operations and machinery used in manufacturing, process control, and other sectors. The functions that were historically handled by human operators – such as stopping and starting machines, loading and unloading metal presses, monitoring mixer speeds in pharmaceutical or food production, etc. – have been largely automated.
These systems allow remote operators to monitor operations, control industrial processes, and collect and analyze data from those processes.
Components of Industrial Control Systems
While different platforms may offer different components, most ICS feature these main components:
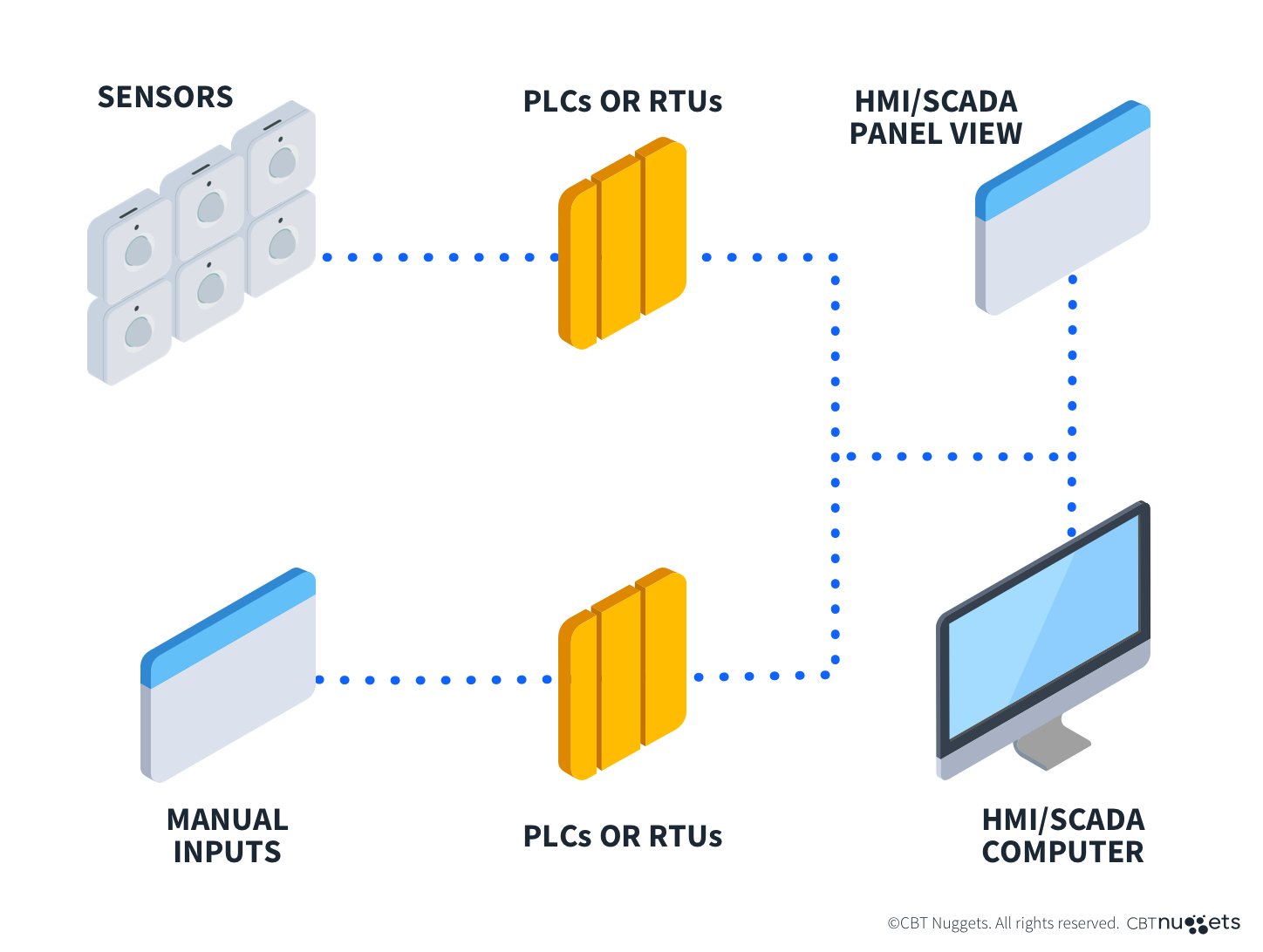
Networked ICS Devices
ICS interacts with sensors, relays, valves, and actuators on the plant equipment. These local devices are connected via Remote Terminal Units (RTU) to hardware called Programmable Logic Controllers (PLCs). Based on programs or operator-issued commands, PLCs collect operational data and/or activate devices.
Increasingly modern plant machinery is being equipped with Intelligent Electronic Devices (IED), essentially making it “IoT-enabled.” The IED replaces the RTU functionality and can acquire data and communicate with SCADA, DCS, and other local devices.
PLCs are reliable and inexpensive and can be used for local control of plant equipment. When large numbers of machines are being managed in a plant, there may be multiple PLCs networked together and controlled by a Distributed Control System (DCS) and/or a Supervisory Control and Acquisition System (SCADA).
Human Machine Interfaces (HMI)
Human Machine Interfaces (HMI) are a key component of industrial control systems. The HMI provides operations staff with easy-to-understand monitoring of the processes being managed. From a graphical interface panel or workstation, the HMI communicates with PLCs and/or RTUs to acquire and present operators with process status and alarms.
Supervisory Control and Acquisition System (SCADA)
Supervisory Control and Data Acquisition (SCADA) systems allow dispersed industrial processes to be remotely monitored, analyzed, and controlled. Nowadays, SCADA systems are software packages from vendors, such as Siemens, Iconics, Inductive Automation, and Honeywell, that run on commercially available servers and workstations.
The computer that runs the SCADA software is normally called the Master Station. It communicates with the remote PLCs and RTUs to collect, process, display, and store real-time operational data. Using SCADA, operators can monitor and control industrial processes running locally or at remote plants or locations.
SCADA systems may interact directly with PLCs, RTUs, and IEDs or via a DCS in each location. Through those linkages, the system collects real-time operational data from sensors on the shop floor, processes that data, and presents it to remote operators. Thus, the operators can make informed decisions to ensure overall process efficiency and minimize unplanned downtime.
For example, the SCADA system might detect and flag errors on a particular production line. The operator can use SCADA to stop the line, while they determine the cause from logged SCADA system data. Once the problem has been isolated, the fault can be resolved, and the line restarted.
Over time, SCADA systems have evolved from self-contained systems to distributed SCADA operating on a LAN or WAN backbone and networked systems where several remote SCADA systems operate under a centralized master SCADA system. Now, ICS architects are grappling with how SCADA will further evolve with cloud computing and the Internet of Things (IoT).
Common ICS Network Protocols
The various ICS components are networked together using a variety of specialized industrial control protocols, including:
Modbus protocol was originally developed for use with Modicon PLCs
Siemens proprietary S7comm protocol that allows PLC to SCADA communication
Distributed Network Protocol 3 (DNP3) used by water and electric utilities to connect SCADA control centers to RTUs and intelligent end devices
The Inter-Control Center Communications Protocol (ICCP) or TASE.2 protocol is standard for communications between electric utility SCADA control centers
The PROFINET Ethernet-based network protocol is used extensively in ICS applications
The CIP (Common Industrial Protocol) may be used to connect to corporate IT and other ICS networks.
As we’ll discuss later, these protocols can be quite vulnerable to cyber-attack.
What are Industrial Control Systems Security Challenges?
As we discussed earlier, the earliest implementations of SCADA connected to the plant via proprietary protocols and on networks that were physically separate from the corporate backbone.
With the evolution of SCADA architectures and corporate pressure for cost efficiencies, ICS are now commonly just one more source of traffic for the corporate backbone network. But this has increased exposure to cyberattacks! In fact, a 2023 survey estimated that over 100,000 ICS implementations have a significant threat of exposure.
The survey also shows that the danger is not solely in the manufacturing and processing sectors. Education (think access controls) and government (think voting systems) are among the top three exposed sectors.
Real-World Examples
The vulnerability of ICS became front-page news with the 2010 Stuxnet attack on Uranium enrichment centrifuges in Iran’s Atomic Energy Organization. This worm reportedly attacked via Siemens SCADA and PLC, disrupting the frequency of the centrifuges and destroying their enrichment tubes. In the West, this was seen as a victory for the “good guy hackers,” but it opened many eyes to the reciprocal danger faced by public infrastructure in the Western world.
In 2023, we saw updated versions of Stuxnet and other infamous ICS attacks. Here, courtesy of cybersecurity expert Jitu Mani Das (CISM CISSP), are the top five Industrial Control System (ICS) attacks of 2023:
CRASHOVERRIDE
This attack disrupted power grids by exploiting vulnerabilities in the IEC 61850 ICS protocol for intelligent electronic devices at electrical substations. The attack manipulated relay settings to cause cascading power failures.
The attack could have been repelled by isolating the ICS from the corporate network, regularly applying security patches to ICS devices, and using intrusion detection to identify abnormal behavior.
PIPEDREAM
PIPEDREAM attacked oil and gas facilities by exploiting third-party vendors to infiltrate SCADA and HMI software, thus gaining access to critical systems. This attack might have been avoided by rigorous control of third-party vendor security practices, requiring digitally signed software updates, and isolating the ICS network from outside connections.
Stuxnet Redux
This update of the 2007 virus has returned to attack nuclear enrichment facilities by exploiting zero-day vulnerabilities in PLC firmware. The virus is introduced to the facility and spreads via USB drives before manipulating centrifuge speeds and disrupting the production line. Mitigation approaches are first to maintain strict separation – air gaps – between critical systems and outside networks, monitoring PLCs for anomalous behavior, and limiting USB use, as well as rigorous scanning of such external devices.
BlackEnergy2
The BlackEnergy attack previously attacked energy facilities, but the 2023 edition targeted water treatment plants by exploiting weak authentication mechanisms in SCADA systems. With this access, BackEnergy2 manipulated processes in the plant, causing water quality issues.
The attack could have been blunted with strong multi-factor authentication for SCADA access, separation of the SCADA and corporate networks, and frequent security audits of SCADA configurations.
Industroyer2
This attack exploited vulnerabilities in ICS network protocols to manipulate PLC instructions and disrupt production manufacturing lines. It could have been repelled by implementing more secure ICS protocols, continuously monitoring network traffic for anomalies, and implementing and testing an effective incident response plan.
Vulnerabilities of ICS Networked Devices
As we’ve seen above in the 2023 ICS attacks, the most common vulnerabilities for networked ICS devices derive not from technical issues – although they don’t help – but from procedural issues.
These include lack of training, poor control over system access, lack of separation between ICS and corporate networks, and lack of regular monitoring for anomalies. These vulnerabilities allow hackers to slip in and exploit technical holes in protocols, operating systems, and other systems.
Best Practices for Industrial Control Systems Security
Security for industrial control systems is one of the nation’s top priorities. The U.S. Department of Homeland Security has published Seven Strategies to Effectively Defend Industrial Control Systems:
Implement application whitelisting
Ensure proper configuration/patch management
Reduce attack surface by isolating ICS networks and shutting unused ports
Build a defendable environment by segmenting the networks into logical enclaves
Manage user access, tighten control on password policies and access privileges, and implement multi-factor authentication
Implement secure remote access by authenticating users and close all hidden back doors into the network
Monitor and respond by rigorous monitoring for IP traffic anomalies, suspicious login and account/user administration activity
In addition, organizations should build a culture of security through robust employee training and awareness programs.
Conclusion
Industrial control systems are clearly part of the nation’s critical infrastructure, and a cyberattack on food and water supplies, the transportation system, energy supply, voting machines, emergency services, and much more may impact everyone's personal well-being. The security of all network devices—especially SCADA systems—is an essential part of this vigilance.
Learn about the configuration and security of network devices by taking CBT Nuggets online certification training such as CompTIA Network+ (N10-009) or CompTIA Security+ (SY0-601).
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.