What is Trunking in Networking?

Quick Definition: In networking, trunking is a method of segmenting and organizing a LAN into several sub-LANs to improve security, save money, and increase scalability. For example, it might be used in an office setting to separate traffic from different departments.
VLAN networking trunking segments a LAN for the purposes of security, optimization, and organization. It is commonly accomplished by creating logical network separations within switches, routers, and other network devices. One of the great advantages of network segmentation is that it separates portions of the LAN into different broadcast domains.
For example, a university LAN could be trunked into two segments: the College of Engineering and the College of Physics. Broadcasts sent only for engineers will never get sent to the College of Physics, thus reducing network load.
Now that we've explored a few benefits, let’s go over what exactly VLAN trunking is and how it can benefit your organization.
What is Trunking?
Trunking, or VLAN trunking, is a way to logically separate a LAN into smaller, more manageable segments. VLAN trunking is accomplished by logically separating switches so that network data flows to the correct subnetwork. Additionally, a single connection is provided between the multiple subnetworks, thus limiting the broadcast destination to the designated sub-LAN.
Trunking is different from regular network connections because it effectively partitions a network into subnetworks, providing only one access point between each subnet.
VLANs are commonly trunked using the IEEE 802.1Q protocol and, to a lesser extent, Inter-Switch Link (ISL). Let's review the definition of IEEE 802.1Q and some of its features.
What is IEEE 802.1Q?
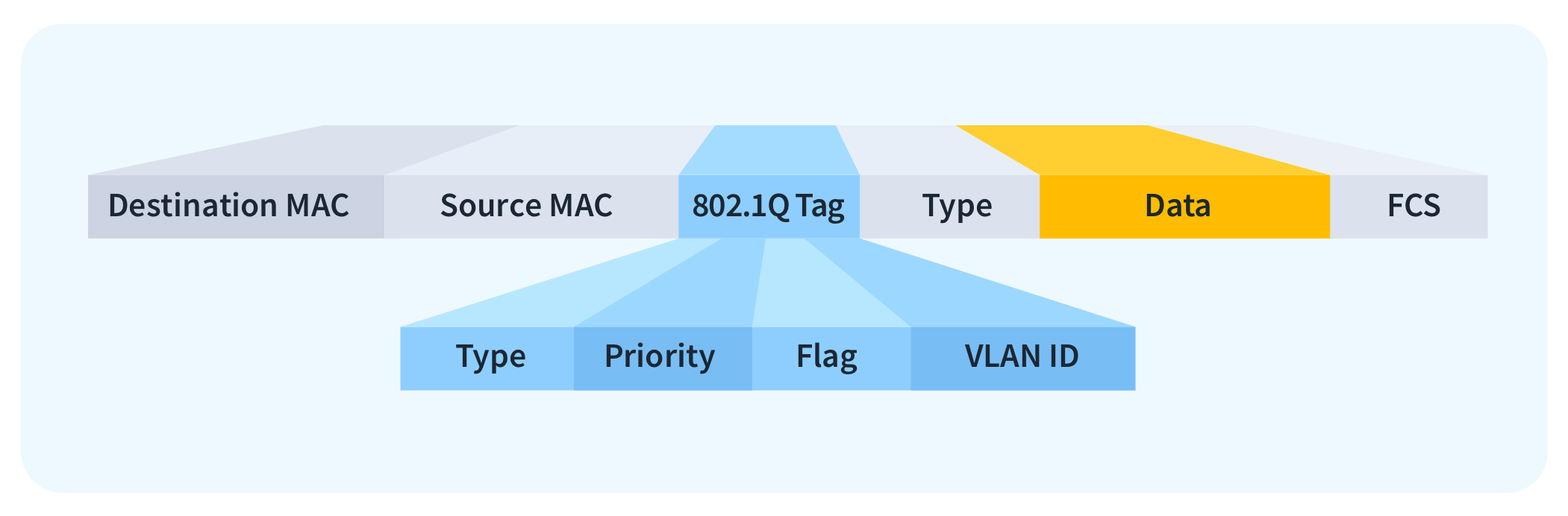
802.1Q is a widely adopted protocol to define VLAN data in an Ethernet packet. 802.1Q employs VLAN tagging, which involves appending a 32-bit header to an Ethernet packet. This header includes a VLAN ID that serves to categorize the packet and indicate the specific network it is associated with. Using this protocol increases network security by making it easier to quarantine networks.
ISL is a Cisco proprietary protocol that has been largely superseded by 802.Q, since it is platform agnostic. However, it is still worth knowing about it for the Network+ Exam.
What are the Benefits of Trunking?
Trunking provides numerous benefits that will increase your security posture, save money, increase scalability, and more. Let's explore each of the benefits in more detail.
Security Posture
Trunking reduces the attack vector by isolating different accounts and users, as only certain ones are allowed entry with the proper VLAN ID. Also, VLANs make it far easier to quarantine a particular subnet if it becomes compromised by a hacker or virus.
Network admins gain granular control over how they can log and monitor each VLAN. This customization mitigates security breaches and increases breach detection.
Cost Savings
Trunking can save money by reducing the amount of hardware and physical ports required to operate the LAN. Say you have three LANs: One for the accounting department, another for the R&D department, and the last one for the HR department. In a pre-VLAN world, each one would have its own designated router. However, there would be far more ports on the router than required nodes on the network, resulting in wasted ports.
With VLAN, all three departments can use the same switches by carving out logical partitions within the LAN. In summary, VLANs save money by consolidating hardware.
Scalability
Trunking also facilitates scalability. As network traffic grows, you can add more physical links to the trunk to accommodate the increased demand for bandwidth. This scalability is far more cost-effective than adding completely new sections.
Optimize Network Efficiency
Trunking optimizes networks by aggregating multiple physical links into a single logical link. In other words, instead of connecting several Cat5 cables into a switch, only one “trunking” cable needs to be connected to join two disparate LANs. This increases overall bandwidth, which is especially valuable for VoIP, video streaming, and large file transfers.
Additionally, load balancing is inherent to trunking because data is automatically routed to the next available port. This efficient networking system reduces congestion and increases the overall speed of the network.
How to Implement Trunking
Implementing trunking involves various technologies and protocols throughout the process. Also, testing and documentation are vital steps to ensure all network traffic is routed correctly and efficiently to the designated network. Here is a brief, step-by-step guide to implementing VLAN trunking.
Create a Plan for VLAN Trunking
The first step is identifying how the network will be divided into subnetworks. Determine the topology of the LAN and how many switches, routers, and gateway are required. Take special care to document and annotate which network devices will be configured for creating VLANs.
Configure VLANs
Log into the switches themselves and designate them as VLANs. This will partition the LAN to ensure data flows to the proper subnetworks. Each VLAN needs a specified VLAN ID, as per the IEEE 802.Q1 protocol. Assign each port on the switch to a specific VLAN.
Configure Trunk Ports
Once you’ve completed assigning ports to each subnet, configure which ports will be designated trunk ports. Set the ports as “trunked” or “tagged” so VLAN data can flow through them.
VLAN Tagging
Configure the VLAN tagging method. For IEEE 802.1Q trunking, set the tagging to IEEE 802.1Q. For ISL (Cisco's proprietary protocol), use ISL. Ensure the VLAN tag is added to outgoing Ethernet frames and processed correctly on incoming frames.
Connect the Devices
Connect the devices to the newly trunked switches and routers. Trunk ports on different devices must be connected together. Ensure the connections go into the designated trunk ports, or the data will not transmit properly.
Test and Verify
Conduct thorough testing to ensure all data is flowing to the correct VLANs. Verify all frames are tagged with the correct VLAN IDs. This can be done using a packet sniffer, ping, or traceroute.
Document Your VLAN Trunking Setup
Maintain comprehensive documentation on the VLAN trunking setup. Include VLAN IDs, designated VLAN ports, and the trunk ports. Periodically revisit the document as the network grows and evolves.
Best Practices for VLAN Trunking
There are numerous best practices you can follow to make your VLAN journey easier. For starters, make sure you have multiplied trunked links between subnetworks. This will add redundancy to the network in case either of the ports or the cable itself fails.
Next, enable load balancing across trunked links to distribute traffic evenly. Load balancing can use several methods, such as round-robin, source/destination IP, MAC address, or traffic volume. Consider the type of traffic and your network's needs when choosing a load-balancing method.
Finally, make sure your VLAN is always logically designed. Do not allow nodes to creep into the network that should not be there. They should always be logically grouped by department, function, or security requirements.
How to Troubleshoot Trunking Issues
Sometimes, trunking does not go as planned. Here are a few helpful troubleshooting tips you can use to diagnose common issues with trunking.
Check if the VLAN is Mismatched
If traffic is not routing to the correct LAN, ensure all the ports are accurately assigned to the correct LAN. If the wires get crossed, then the packets will not arrive at the intended destination.
Hardware Failures
While this may seem obvious, it is worth checking if all the cables and hardware are in working order. Checking the device and software statuses can often lead to a quick resolution. Additionally, make sure you can ping all of the hardware devices in the path. Also, verify the cables are working properly.
Routing Issues
If VLANs are unable to communicate, check the configuration of the device responsible for inter-VLAN routing. Ensure routing is correctly set up to allow traffic between VLANs. Also, verify that the access control lists (ACLs) on the router are authorizing traffic to the intended destination.
Final Thoughts
In this article, we delved into the world of trunking and how it can benefit your organization. For the Network+ exam, and for networking in general, it's important to understand what VLAN trunking is. VLAN trunking is a way to segment and organize a LAN into several sub-LANs. It employs the IEEE 802.Q1 protocol (and, to a lesser extent, ISL) to structure Ethernet frames for efficient identification within the LAN.
Remember that trunking has to be configured on the switch or router that plans to join the subnetworks. Carefully consider which ports will belong to which LAN and which ports will be the “trunk” port, i.e., the ports that will connect the disparate LANs.
Trunking is a widely adopted concept and is virtually ubiquitous in modern LANs. Having a comprehensive grasp of this concept is essential, not only for examination purposes but also for your role as a networking engineer.
Not a CBT Nuggets subscriber? Sign up for a 7-day free trial.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.