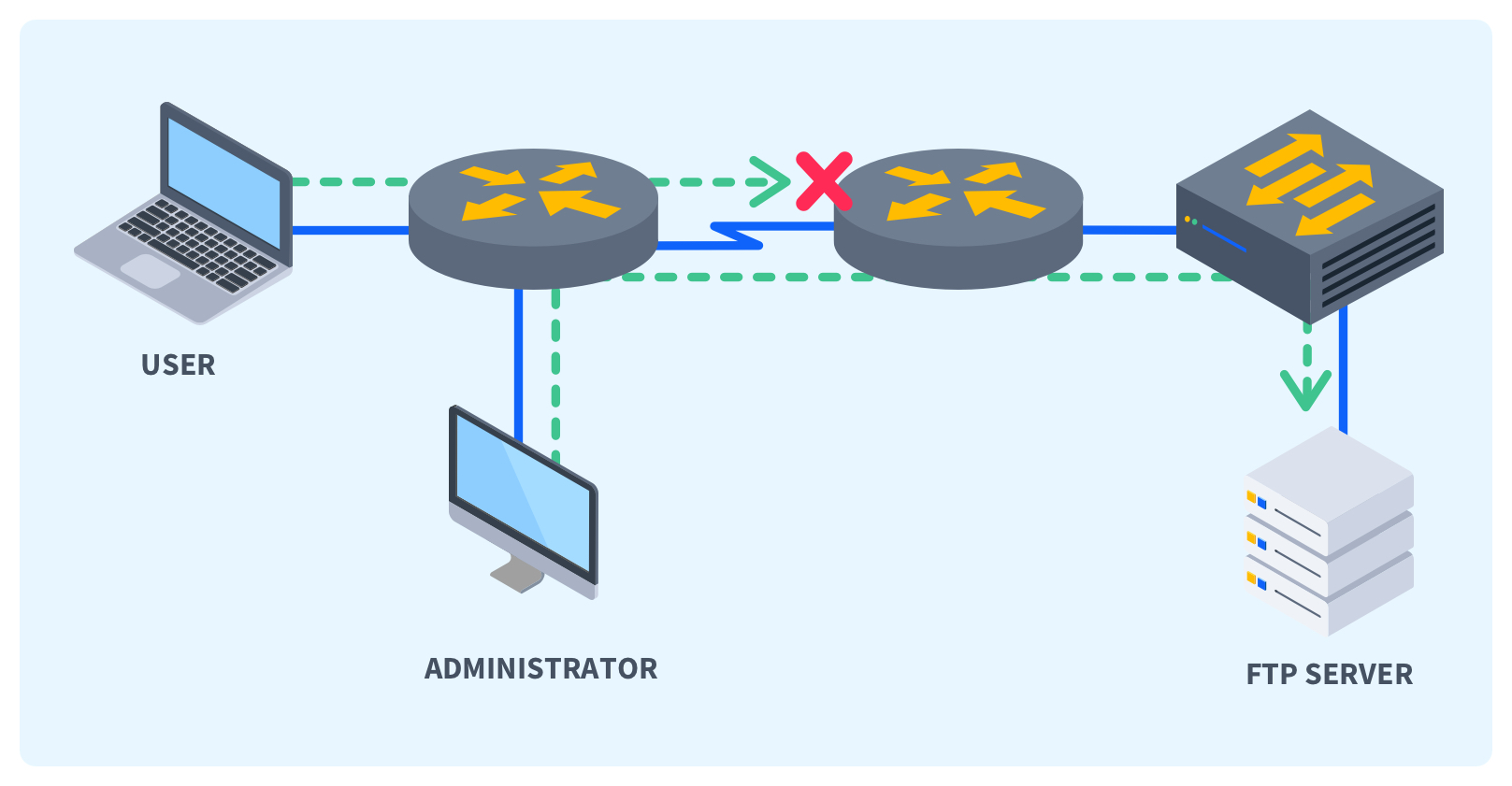
What is an Access Control List (ACL)?

Quick definition: An access control list (ACL) is a set of rules or conditions defined on a network device, such as a router or firewall. It dictates which network traffic is allowed or denied based on specific criteria, such as source and destination IP addresses, port numbers, and protocols. ACLs are instrumental in managing and securing data flow within a network.
Access control lists (ACLs) are crucial in safeguarding any networking. ACLs serve as a first line of defense to ensure that only authorized traffic is transmitted to and from a network. Understanding ACLs and how to implement them is crucial to passing the Network+ Exam and hardening the security posture of a LAN or WAN.
Clearly defined ACLs prevent security intrusions, malware, ransomware, and more before they can even become a threat. In this article, we’ll walk through ACLs in detail, including how they work, how to implement them, and the importance of ACL monitoring.
How Does an Access Control List (ACL) Work?
ACLs work by defining rules on a firewall regarding how the traffic flows in and out of a network. The traffic is either allowed or denied based on what the ACL authorizes. ACLs inspect each incoming and outgoing packet and verify whether it is authorized. Here's a breakdown of that process.
Rule Creation and Ordering
ACLs are defined by criteria such as port, IP address, or specific protocols. For instance, you could write an ACL that blocks all incoming traffic headed to port 80 from the IP address 192.68.103.55.
Once the rule is created, it is put into a specific order for evaluation on the firewall. ACLs are evaluated from top to bottom, so it is crucial that one rule does not involuntarily interfere with any other.
Packet Evaluation
Once a packet enters the firewall or router, it is evaluated according to the list. Think of an ACL like a bouncer at a nightclub. He quickly scans the guest and checks against the list. The guest is either allowed in — or gets the boot. Remember, ACLs are evaluated starting at the top of the list, and the packet is only flagged once a rule that matches the packet’s characteristics is met.
Default Actions
If the packet does not match any rule in the ACL, a default rule often specifies the action to take. It will be a catch-all rule at the bottom of the priority list. This could allow or deny the packet, depending on the security policy.
Often, for enhanced security, a zero-trust approach is adopted, allowing only packets that meet specific criteria and defaulting to deny all others.
With that said, there are two different versions of ACLs — standard ACLs and extended ACLs.
What’s the Difference Between Standard ACLs and Extended ACLs?
Standard ACLs and extended ACLs are the two types of control lists used in networking. Standard ACLs have a simple configuration that only considers the destination IP address. Extended ACLs, on the other hand, are more complex and consider both the source and destination IP addresses.
Extended ACLs are required for more granular requirements, while standard ACLs are suitable for broad rules that will not need to change often.
That’s the gist of how ACLs work; now, let’s walk through a couple of scenarios.
When to Use an ACL
Let’s say an organization wants to restrict access to its internal network from external traffic. It could set up an ACL to deny all incoming IP addresses not part of the internal network.
In another scenario, let’s say your organization has limited bandwidth and wants to prioritize VoIP calls. An ACL can be set up to prioritize VoIP traffic to ensure crystal-clear calls.
Lastly, the network administrator may want to deny services like peer-to-peer file sharing. This could be done by denying entry to ports often used to execute file-sharing protocols.
How to Implement ACL
Implementing ACLs can be a time-consuming process, but it is better to have all the rules needed upfront and organized before putting them into action. After all, the ACLs must be effective, meet security requirements, and not inadvertently disrupt network traffic.
Understand Network Traffic
You'll want to have a firm understanding of your network flow before creating any ACLs. Analyzing user behavior and business requirements will help you craft ACLs that strengthen your organization’s security posture while mitigating disruptions to the end-user. One way to do this is to document commonly used ports and protocols. Also, keep a record of which IP CIDR addresses are commonly used on the network.
Prioritize Rules from Specific to General
When implementing ACLs, keep in mind rule prioritization is critical. The most specific rules should be at the top, while general rules should be at the bottom. This will mitigate unnecessary network congestion and ensure adequate QoS (Quality of Service) while maintaining a tight security posture.
Testing and Verification
Before testing ACLs in a production environment, do a dry run in a lower non-production environment. This decreases the chance of significant service disruption to the end user. Essentially, you need to “try before you buy” and test the ACLs to actually do what you expect. This can be done on test servers in a controlled environment.
These are just a few of the many factors to consider when implementing an ACL. Next, let’s discuss how exactly an ACL is configured.
How to Configure ACL
ACLs are configured on either the firewall, the router, or both. While proprietary configuration may differ slightly, the process is ultimately the same. A frequently used hardware brand for routers is Cisco.
Let's review configuring an Access Control List (ACL) on a Cisco router. We highly recommend practicing these commands either on your router or on a router simulator –plenty of them are free!
Enter Global Configuration Mode
enable
configure terminal
Create an ACL
A Standard ACL
access-list 1 permit 192.168.1.0 0.0.0.255 (Permits any traffic between 192.168.1.0 to 192.168.1.255)
access-list 1 deny any (Denies all other traffic)
An Extended ACL
access-list 101 permit tcp 192.168.1.0 0.0.0.255 10.0.0.0 0.0.0.255 eq 80 (permits TCP traffic from the source IP range 192.168.1.0 to 192.168.1.255 to the destination IP range 10.0.0.0 to 10.0.0.255 on port 80 (HTTP).
access-list 101 deny ip any any (Denies all other IP traffic)
Hit enter and these ACLs will be committed.
Verify Configuration
show-access-list. This command will show all ACLs. Verify the ACL you just created is showing properly.
How to Test and Troubleshoot ACL
Testing an ACL is a critical step to ensure uninterrupted traffic flow. One of the best ways to test and troubleshoot an ACL is with a packet analyzer such as WireShark.
1. Open WireShark
Download and install WireShark.
2. Generate Test Traffic
Let’s say you want to verify that all traffic outside the range 192.169.1.0 — 192.169.1.255 is DENIED. Start by creating test traffic where some of the packets would fall both in and out of that range.
3. Capture the Packets
Verify WireShark is capturing packets, and then add a filter on the IP source, such as src != 185.23.23.0 or anything else outside of the allowed IP range.
4. Analyze the Results
Verify the packets are not reaching the intended destination. If you observe this behavior, then you’re seeing the ACL in action!
How to Monitor and Maintain ACLs
After a while, a network may end up with a staggering amount of ACLs. As the number of rules accumulates, it is important to monitor and maintain them to ensure proper security posture. Here are a couple of tips to get you and your team going.
Regular Audits
Reviewing ACLs on a regular cadence provides important insight into how they work. Verify the rules align with your organization’s security policies and operational needs.
Performance Monitor
Regularly review the network's performance and verify none of the ACLs are denying necessary traffic. If your ACLs leverage QoS for VoIP or other protocols, verify they receive the necessary bandwidth to meet operational needs.
Logging and Review
If logging is enabled in your ACL rules, regularly review the logs. Check for denied traffic or unexpected patterns indicating security incidents or misconfigurations.
Final Thoughts on ACLs
ACLs are a cornerstone of both security and networking and should be second nature to a network engineer. They also hold a prominent place on the Network+ Exam. Here are a few quick takeaways from the article.
Extended Vs. Standard ACLs
Standard ACLs are simpler and only deal with the destination IP address. Extended ACLs can include the destination, source, protocols, and more. These are for more granular access control.
Configuration ACLs
ACLs are configured on a router or firewall, and either deny or grant access to network packets that meet specific criteria. Often, this includes an IP range, a QoS threshold, a port, or a protocol. Whether you’re using Cisco, Aruba, Meraki, or any other competitor, the steps will be similar. However, there may be slight differences in ACL configuration since the hardware itself is different.
WireShark Analysis
ACLs can easily be seen in action using WireShark. Fire up the tried and true app and verify whether or not packets are making it to their intended destinations.
Lastly, make sure your ACLs are prioritized, with the most specific at the top and the most general at the bottom. There has never been a better time to get into networking, and there is no better place to start than ACLs. Happy networking!
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.