What Is a GRE Multipoint (mGRE) Tunnel?

Quick Definition: A GRE multipoint tunnel, or Multipoint Generic Routing Encapsulation (mGRE), is a protocol used for connecting multiple remote sites through a Virtual Private Network (VPN). It employs a hub and spoke topology to encapsulate and forward data packets from one remote site to another, making VPN management simpler and more scalable. GRE tunnels are essential for routing data efficiently and securely over multicast-enabled networks, particularly in Cisco technologies.
Multipoint Generic Routing Encapsulation is a protocol used for creating Virtual Private Networks (VPNs) over a multicast-enabled network, particularly for Cisco technologies. It is essential to have a firm understanding of mGRE if you are studying for the Network+, CCNA, or CCNP. With that in mind, let’s walk through exactly what mGRE is.
What is mGRE?
Multipoint Generic Routing Encapsulation (mGRE) is used to connect multiple remote sites through a VPN. mGRE uses hub and spoke topology to encapsulate and forward packets from one remote site to another. Encapsulating data packets from different sources into a single tunnel facilitates scalability and simplifies VPN management.
What is Encapsulation?
Encapsulation is the process of taking a source data packet and adding additional headers to allow the usage of different protocols. With respect to mGRE, “encapsulating a packet” means concatenating the original IP packets with additional headers to facilitate the creation of a virtual tunnel.
Let’s break it down step by step:
The IP packet is sent from a given workstation. For example, an email is sent.
mGRE now encapsulates that packet inside another packet. This will generally happen in the central hub.
The “outer” packet allows the “inner” packet to tunnel through a VPN. The central hub will forward this packet to the destination.
The packet is “decapsulated” at the destination and is executed upon. In this instance, the email shows up in the correct inbox.
That all sounds great…but is all that work really necessary?
Why is Data Encapsulation Necessary?
Data encapsulation is necessary because it provides security, a uniform standard, and a mechanism for packet tunneling. Data encapsulation offers an extra layer of security by providing metadata about the destination and source IP addresses. Firewalls can be configured to analyze the source and destination to maintain proper security posture.
Data encapsulation provides a uniform standard. All source workstations can expect the same type of data to encapsulate and decapsulate. For example, a data packet from an email will look different from a printer packet. However, once they’re encapsulated, the central hub will be able to route them all in the same way. This uniformity facilitates both simplicity and scalability.
Without data encapsulation, there would be no way to tunnel through networks. Data encapsulation provides a common “language” for routers, switches, and nodes to work cohesively over virtual networks.
So, that is why encapsulation is necessary, but it still may not be clear how encapsulation is different from mGRE.
What Does Multipoint Generic Routing Encapsulation Mean?
mGRE is a way of encapsulating data specifically for Cisco networks to manage and direct packet data through a VPN with remote hosts. By adding additional headers to packets, mGRE simplifies the routing process by creating a common communication standard.
Explained another way: when you send a letter via snail mail, the letter is encapsulated in an envelope. The post office expects the destination address to be in the middle, the originator’s address in the top left, and postage in the top right. If everyone sent letters without encapsulating them in an envelope first, it would be difficult for the post office to route letters efficiently. mGRE is just like that, except for data packets. Tunneling is another important aspect of the protocol–let’s touch on that next.
What is a GRE Tunnel?
Compared to a split tunnel, a GRE tunnel is a point-to-point networking technology to tie two endpoints together. These two endpoints often are a spoke node and a central hub – thus creating a hub and spoke topology. Ultimately, the most significant advantage GRE tunnels provide is a common understanding between devices to route traffic accurately.
How Does an mGRE Network Work?
An mGRE Network works by creating a common protocol for multicast network packets. By encapsulating source packets in a common GRE protocol, the transmission of data to foreign networks is simplified and scalable. Let’s discuss GRE tunnel configurations, mGRE ports, and how they relate to hub and spoke technology.
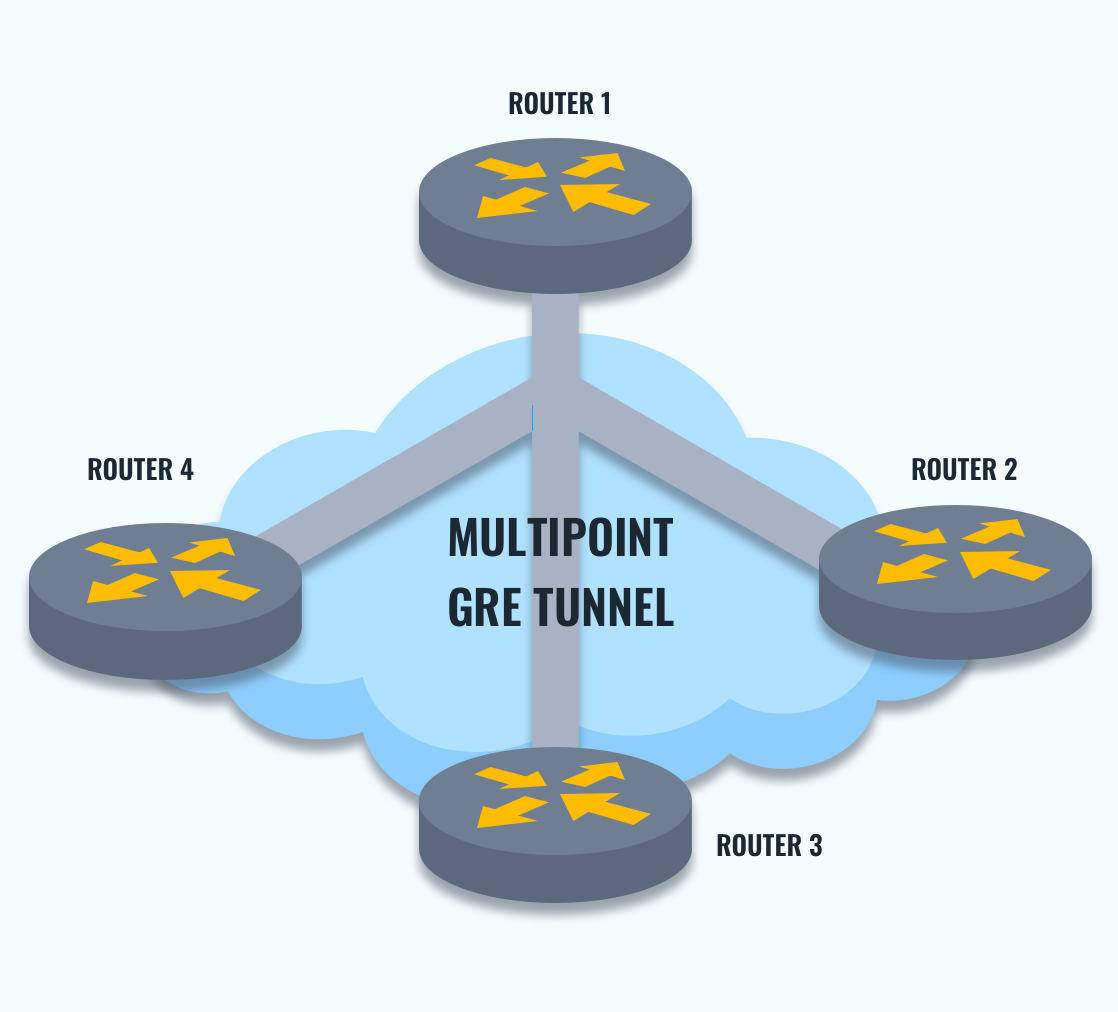
An Overview of GRE Tunnel Configuration
GRE tunneling must be configured on Cisco routers to establish multipoint communication tunnels between various endpoints. Here is an incredibly high overview of configuring your network for GRE tunneling.
Determine which network device will act as a central hub and which will act as spoke nodes.
Log into the Cisco switch or router that serves as the central hub. Enable mGRE configuration on the central hub router.
In the router, create a tunnel interface for each spoke node and assign IP addresses to each GRE tunnel.
Configure all subsequent routers and switches to direct traffic to the new GRE tunnels.
Update all the route tables so that they’ll see the new GRE tunnels.
Verify everything works by using ping or traceroute from a spoke node.
It is very important to note there is no mention of security in the above simplified steps. Configuring IPsec in conjunction with mGRE is important for creating a secure environment. Next, let’s talk about the port GRE traditionally runs on.
Understanding GRE Ports
One thing to consider when dealing with GRE is that it operates on OSI Model Layer 3 (Or layer 4, depending on how you look at it). GRE encapsulates packets and tunnels them to the intended destination via point-to-point communication.
However, GRE tunnels’ IP addresses will often be configured with port 47. This is the traditional GRE port, and the packet encapsulated with port 47 will be tunneled to its destination using GRE.
The Relationship Between mGRE and Hub and Spoke Topology
mGRE is the perfect example of hub and spoke topology in action. Each node establishes a GRE tunnel with the central hub. Therefore, every connection is a point-to-point communication with the central hub. The following operation occurs when a source node needs to transmit data to a destination node.
First, the node sends the data to the central hub, which is encapsulated. After that, the central hub forwards the data to the destination node. Lastly, the destination decapsulates the data and reads the transmission.
All in all, mGRE is a textbook example of the hub and spoke model (which is also an important concept for Network+ certification).
What are the Advantages of mGRE and mGRE Tunnels?
There are numerous advantages of mGRE and mGRE tunnels. In this section, we will outline why Cisco-centric organizations use mGRE. Then, we’ll walk through how mGRE can future-proof your network.
Scalability From mGRE Tunnels
One of the greatest advantages of mGRE is how mGRE tunnels facilitate scalability. mGRE plays a significant role in network scalability by simplifying the process of adding new host machines to the VPN.
This is because mGRE relies on a hub and spoke model. That means adding a machine is as easy as configuring a GRE tunnel and adding it to the route table. Next, let’s talk about how mGRE is cost-effective.
Cost-Effective Compatibility Thanks to mGRE Tunnels
mGRE tunnels are cost-effective on numerous fronts. If the network needs to be scaled up to handle a heavier load, then the only hardware requiring more resources will be the central hub. This saves a lot of money on resource allocations.
mGRE tunnels also save money on the price of troubleshooting. Network administrators can focus on the particular VPN tunnel associated with the spoke node causing the issue. This is different than mesh topology of point-to-point links, where the issue could be in any number of places.
Finally, centralized routing entails that all security configurations required for packet analysis can be concentrated on a single node—the central node. This means all security protocols and software only need to be licensed to one node, saving cash.
How mGRE Tunnels Simplify Configuration and Management
One of the best things about mGRE is how easy it becomes to add and remove nodes from the network. As alluded to earlier, mGRE makes it extremely easy to add a node by configuring a tunnel that points directly to the central hub.
Also, configuration becomes a breeze because all management occurs on the central node. This includes firewall configuration, packet analysis, network load analysis, and more.
Do mGRE Tunnels Simplify Data Transmission?
Yes, by creating a universal standard for receiving and transmitting data, packets can be sent across wide virtual ranges without a gap in communication.
Also, all data routes through a central hub, which provides all of the auxiliary network needs, instead of having to do that work on the node itself.
What are the Downsides of Using mGRE Tunnels?
While mGRE is great, there are downsides to using mGRE tunnels. In the following section, we’ll go over some of the drawbacks of leveraging mGRE on a network and some of the extra steps you’ll have to go through to get it to work correctly.
The Centrality of mGRE Tunnels Can Be Dangerous
While centralized management can be a benefit, it can also be a double-edged sword. The biggest issue is that the central hub becomes a single point of failure. If the central hub goes down, then the entire network falls to its knees until the issue is corrected.
Also, it serves as a bottleneck for all traffic. The network latency can become soul-crushing if the central hub is not powerful enough.
Lastly, the central hub becomes a massive attack vector, since they know all “the eggs” are in that single basket. If hacked, it could expose the location of every remote site on the network. Not good!
mGRE Tunnels Can Lead to Network Complexity
In addition to the inherent danger of a centralized hub, mGRE tunnels can be quite complex to leverage when the network reaches sufficient complexity. One of the key features of mGRE is multicast transmissions (what the M stands for). Multicast is great in many ways because it allows a source node to send data to specified nodes.
Unfortunately, multicast can become quite complex to manage as the network enlarges. Configuring which nodes send traffic to other nodes can quickly get out of hand, and the routing tables can start to look very complicated. This can cause human errors when configuring the IP addresses, and cause wasted resources if redundant multicast transmissions are initiated.
mGRE Tunnels Lack Native Encryption
As mentioned earlier in this piece, mGRE lacks native encryption. This means configuring IPsec is non-negotiable. mGRE has no native encryption associated with it: it is simply a protocol for transmitting packets quickly and reliably over vast distances.
IPSec is a suite of protocols and techniques used to secure communication over a network. IPSec is primarily used to create secure channels over VPN, and it's exactly what you’ll need to tackle mGRE tunnels.
Technologies That Rely on GRE Tunnels
Cisco technology is nigh ubiquitous with the networking world. That’s why it should not be a surprise that several technologies rely on GRE tunnels.
VPNs and GRE Tunnels
A VPN with GRE tunnels relies on mGRE technology. GRE tunnels are specifically designed to encapsulate packets with mGRE metadata so they can multicast to several different destinations.
Bear in mind that Cisco offers plenty of other VPN solutions besides mGRE, but mGRE is certainly popular.
Can WANs Use GRE Tunnels?
Absolutely! Since GRE is a tunneling protocol, it can be used on any virtual network. One situation when mGRE would be advantageous is when setting up a private network extension.
A private network extension extends a private VPN over a public network, such as the Internet. This is useful for connecting geographically dispersed offices or data center security in conjunction with IPSec.
mGRE may work out okay with a WAN, but whether Cisco’s invention is cloud-compatible may not be clear. Let’s touch on that in our final section.
GRE Multipoint Tunnels and Cloud Networking
GRE Multipoint Tunnels are not native to any major cloud platform. However, just because it is not native doesn't mean it is not supported.
Several cloud providers such as AWS and IBM have solutions that allow GRE tunnels to travel into cloud data centers. For example, if you already have or want a hub and spoke topology within the cloud, mGRE would be an excellent protocol to make it possible.
Also, particularly in AWS and GCP, mGRE can integrate multiple VPCs (Virtual Private Clouds), allowing you to create a hub and spoke technology inside the cloud.
Conclusion
This may have felt like a huge payload of information, but you’ll need to know all of it to pass the Network+ certification exam.
Now that you understand mGRE tunnels well, it would be advisable to learn about the topology that makes it all possible: hub and spoke. Then, move on to the other topologies, such as mesh and ring topology. Thanks a lot for sticking with it, and happy networking!
Not a CBT Nuggets subscriber? Create your account now.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.