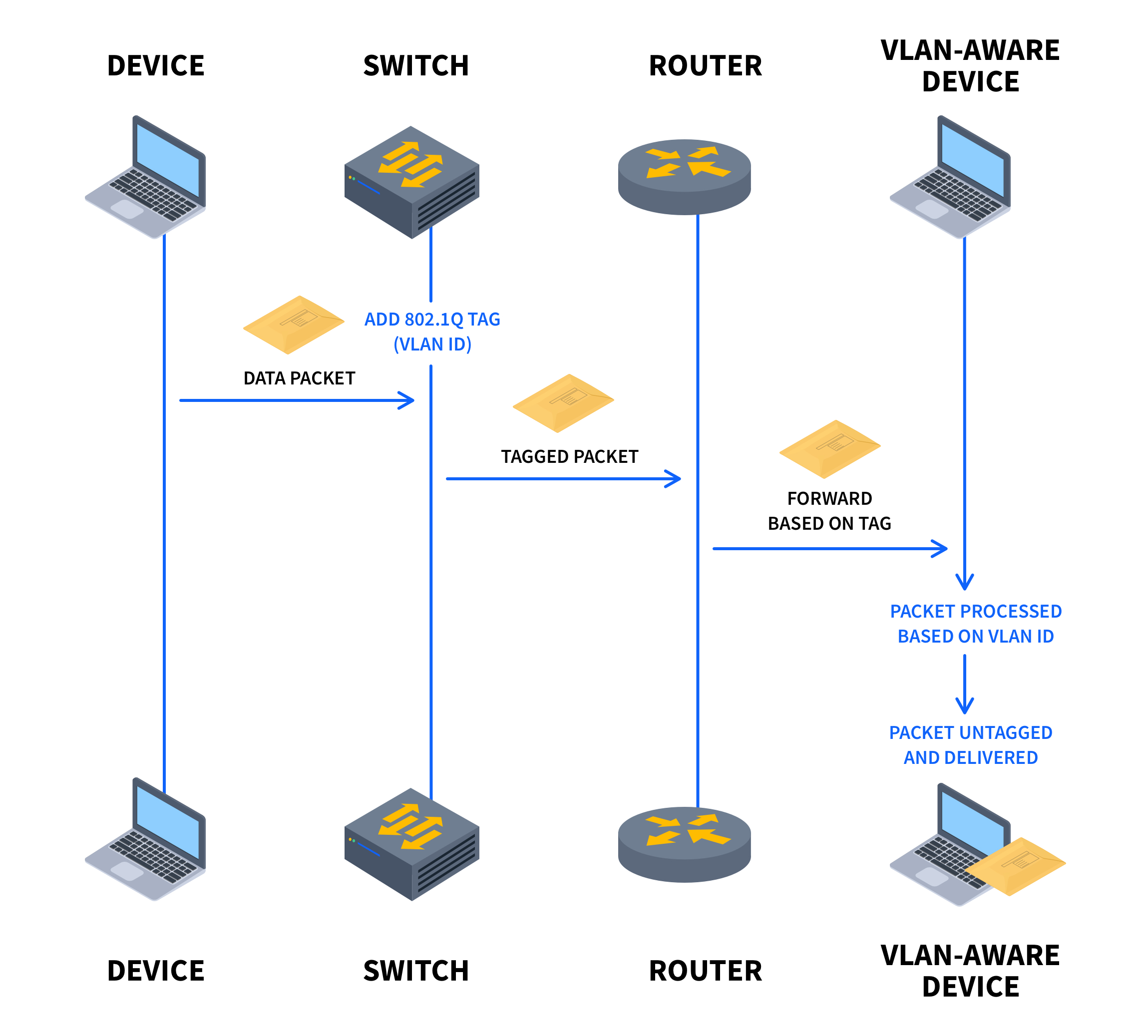
What is 802.1Q Port Tagging?

Quick Definition: 802.1Q is a protocol for tagging Ethernet frames with VLAN (Virtual Local Area Network) information, enabling efficient network segmentation and management.
Networking has advanced over the decades, and if you work with modern network infrastructure, you know the importance of VLANs. You’ll also need to understand things like port configurations and tagging to manage daily operations effectively.
Today, we'll examine the 802.1Q standard and how it works. We'll explore the details behind 802.1Q port tagging and learn what it's for, why you should use it, and how you can implement it.
What is Port Tagging?
Port tagging is used to identify and segregate network traffic according to the VLAN it belongs to. Assigning tags to Ethernet frames helps network devices distinguish between different VLANs and apply different configurations and policies depending on the setup.
Port tagging is also useful for situations where multiple VLANs need to share the same physical infrastructure, such as enterprise networks or data centers. This saves you the hassle and expense of running entirely separate network cabling and network switches if you need to isolate equipment and ensure no access is possible between two networks, which is a huge win.
Benefits of Port Tagging
There are additional benefits to port tagging, including:
Network segmentation: The best way to organize and manage a network is to divide it into smaller logical segments using VLANs. This allows you to manage and control traffic flow better, which increases network efficiency.
Traffic isolation: Port tagging lets you create separate broadcast domains, which improves security by isolating VLANs from one another. This is very useful for managing network environments that deal with sensitive information or data that needs to be separated for security or compliance requirements.
Simplified management: Port tagging allows you to apply consistent policies and configurations across multiple VLANs, reducing the complexity of managing a large network. This streamlines tasks like access control, Quality of Service (QoS), and IP address configurations.
Bandwidth optimization: When you create broadcast and multicast traffic inside individual VLANs, port tagging helps optimize bandwidth usage and minimize unnecessary network load. When this is set up correctly, you will see improved performance and reduced latency, especially in networks with high traffic volumes.
It’s not all smooth sailing, though. Port tagging can be challenging, as it can introduce misconfiguration and compatibility issues between devices. But with careful planning, you can avoid common issues and get your network running faster and more securely.
802.1Q: The Standard for VLAN Tagging
The 802.1Q standard was developed by the Institute of Electrical and Electronics Engineers (IEEE), and is the most widely used protocol for VLAN tagging. It works by inserting a VLAN tag into the header of an Ethernet frame and allows switches and other network devices to identify and process the frame through something called a VLAN membership.
Key features of 802.1Q include:
12-bit VLAN identifier (VID) field that supports up to 4,096 unique VLANs: This is a pool of available VLAN IDs that allows you to create complex network segments that are easily customizable.
Priority Code Point (PCP) field for Quality of Service (QoS) prioritization: The PCP field allows you to assign priority levels to different types of traffic. When tagged, critical data receives preferential treatment, allowing for seamless data transfer during network congestion.
Native VLAN support for untagged frames: 802.1Q has a native VLAN (usually VLAN 1) that handles untagged frames. This feature allows for compatibility with devices that do not support VLAN tagging, allowing you to integrate non-VLAN-compatible devices into mixed networks.
When you implement 802.1Q, you can create logically separate networks over the same physical network infrastructure, simultaneously improving security, performance, and manageability.
How to Implement Port Tagging and 802.1Q
To set up port tagging with 802.1Q in your network, you’ll generally follow these steps:
First, you need a plan for your VLAN design. It’s a good idea to consider things like security precautions and your network's performance right from the start, as this will help you structure your plan without too many surprises later. Every organization is different, so you will need to understand what resources need to be available to each VLAN before you start.
Next, consider how many VLANs are needed and what each one will be used for. Each device on your network needs to be associated with a VLAN. Drawing a sketch or diagram is very useful for this phase.
Set up networking equipment such as switches, routers, and firewalls to support 802.1Q tagging. This involves enabling tagging on specific Ethernet ports on each device and defining VLAN memberships.
Example: This is a very basic list of commands you could use to set up a simple VLAN (VLAN 10) for the Finance department on port 0/1 on our fictional network:
Switch(config)# vlan 10
Switch(config-vlan)# name Finance
Switch(config-vlan)# exit
Switch(config)# interface GigabitEthernet0/1
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan 10
Based on your design, assign ports to the right VLANs. This can be done through the device's management interface or command-line interface (see the above example commands for a Cisco device).
Finally, verify the configurations and test connectivity between devices within the same VLAN and across different VLANs, also called trunking. You can use tools like ping, traceroute, and packet analyzers to map out your VLAN segmentation and check off each device and port once you are happy with the results.
Best Practices for Setting up 802.1Q
Here are some best practices for 802.1Q to ensure a smooth setup:
Use VLAN names and numbers that make sense for your environment for easy identification and documentation.
Document your VLAN design and configurations with write-ups and diagrams, including port assignments and device roles. Once you have validated that everything works as it should, save your configurations for each device. You can store all of this together for ease of reference if you ever need to check something later.
Audit and update your VLAN documentation whenever your setup changes. This is important so you can keep track of how things have changed over time and identify if any changes might have caused issues. These issues could be things like VLANs no longer communicating with one another or devices no longer being able to reach certain network resources.
For security and peace of mind, you should look at access control lists (ACLs) and other security measures to ensure your VLAN segregation is rock-solid. This can take time and might need tweaking as you go. Remember to document these configurations as well.
Troubleshooting Common Issues During Configuration
Troubleshooting is sometimes part of the journey to setting up your 802.1Q environment. Common issues you might face include VLAN mismatches or incorrect tagging. When you do have issues, you might need to review your device configurations and analyze traffic if you have gone through all your basic checks.
If you think something is not quite right with your setup, use packet captures and other networking tools like WireShark to find suspicious activity. You can also contact your hardware vendor or read through their support material to understand what the issue could be, like a bad configuration or something more serious.
If you are new to networking in general, the CompTIA Network+ can help you get a better understanding of basic network fundamentals like VLANs, as well as other basic skills for managing and troubleshooting networks and understanding the basics.
802.1Q Security Considerations
802.1Q allows you to segment your network, but there are other security measures you should implement to protect your network. Common security issues include:
VLAN hopping attacks: These occur when an attacker gains unauthorized access to other VLANs by exploiting misconfigurations or vulnerabilities in your network devices. In some cases, this allows an attacker to bypass security controls and access sensitive resources that they are not supposed to.
Double-tagging attacks: This is an exploit that can bypass VLAN restrictions. When this happens, an attacker injects frames with two 802.1Q tags, tricking the switch into forwarding the frame to an unauthorized VLAN and allowing access.
Unauthorized modification of VLAN configurations: This occurs when an attacker manipulates VLAN settings to gain access to restricted network segments or disrupt your network with malware and other malicious payloads.
Here are a few steps you can take to protect your network from these security concerns:
Port security measures: As an additional security measure, you can implement port-specific controls like MAC address filtering and DHCP snooping. These help prevent unauthorized devices from connecting to the network and control IP address assignment so unrecognized devices can’t communicate with your network.
Secure your network equipment: It is best practice to change your default logins to your networking equipment so that nobody can log in with default credentials. Even if you are certain a device won’t ever be exposed to the internet, it is always a good idea to secure your devices with proper passwords and not the manufacturer’s default credentials. (You would be surprised how many devices are never secured with new passwords after being configured). This ensures that only authorized personnel can modify your network’s VLAN configurations and port settings.
Scheduled checks: Perform regular security checks and make sure any changes to your devices have been documented properly. While not necessary for most networks, you can also look at penetration testing and security audits to identify vulnerabilities and misconfigurations in your network. This usually involves hiring a consultant, so it might not make sense for smaller companies unless there is some suspicion about the security of the network.
Further security measures: Techniques like private VLANs (PVLANs) and VLAN access control lists (VACLs) further restrict communication within and between VLANs, minimizing the impact of successful attacks.
Conclusion
Port tagging and the 802.1Q standard might seem a little intimidating at first, but they are very important skills to learn if you are working with complex networks. When you understand concepts like tagging, VLANs start to make sense and will give you an idea of the potential configurations that you can implement in your own environment.
Want to learn more about networking? Consider our CompTIA Network+ and Cisco CCNA training.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.