Network Device Management Access Methods to Know for CCNA

Device misconfiguration can bring down parts of your network—or the entire thing. It's important to decide who has access to network interfaces and the methods of access. The most common methods to handle these tasks are SSH, Telnet, and HTTPS, which we'll cover here.
The CCNA will cover all these access methods, so it's important to have a thorough grasp of each one. Don't worry—we'll cover them all. We'll start with primitive Telnet and wrap up with sophisticated cloud access.
First, though, let's get a clear grasp of what "network device management access" means.
What is Network Device Management Access?
Network device management access is the ability to log in to, troubleshoot, and monitor network devices. "Network devices" refer to routers, switches, firewalls, gateways, and all the devices required to make a network tick.
Each device is critical to a network and can create a single point of failure. You can manage these devices using either a command-line interface (CLI) or a graphical user interface (GUI). The CLIs used will be SSH, Telnet, or TACACS+. The GUIs will be cloud management access or a proprietary management system.
Accessing devices allows you to take several actions. For one, initial setup is done through direct device access. Traffic analysis is often accomplished through network device management. It's also used to identify bottlenecks, unusual activity, or security threats. Now, let's look into one of the most common access types: Telnet.
Telnet
Telnet is a remote access protocol developed in the late 1960s. It operates over TCP/IP and was one of the first protocols. Although Telnet has been largely supplanted by SSH, let's discuss a couple of niche cases where it still might be handy.
Simple Networks
If you need to troubleshoot a basic network without an internet connection, Telnet is a simple solution. It offers an easy interface for verifying that servers are up and accessible.
Legacy Systems
Some legacy systems may not have SSH installed. These would probably be old, mainframe applications. If Telnet is the only option, then that is a good reason to use it.
Installing Telnet
Telnet is easy to configure and install. However, it is disabled by default on Windows 10/11 System. To enable Telnet, follow these steps:
Open the Start Menu and type "Control Panel" to open it.
Go to Programs > Programs and Features.
Click on Turn Windows features on or off on the left side.
Scroll down and check the box next to Telnet Client.
Click OK and wait for Windows to install the Telnet client.
Then, go to your command line console and enter this syntax:
telnet <hostname> <port>For example, telnet www.cbtnuggets.com 80
Security Concerns
The dealbreaker with Telnet is that everything sent to and from it is unencrypted, including usernames and passwords. This makes it extremely easy to intercept. Regularly using Telnet would be a grave miscalculation from a security standpoint. Use SSH instead of Telnet for other than the listed niche uses.
SSH (Secure Shell)
SSH (Secure Shell) is a common protocol that allows users to access a device remotely. The device can be anything, from a PC to a router or switch. It has replaced Telnet as the go-to remote access CLI tool. The key reason is in its name: secure shell. SSH encrypts data by default, so it is far safer to use when accessing remote terminals.
SSH is installed by default on Mac, Linux, and Windows. To execute an SSH command, open your terminal and type ssh <username>@<ip address>—for example, ssh root@127.0.0.1. If you use SSH a lot, I would recommend downloading mtputty, or a similar SSH organizer. Mtputty allows you to organize, save, and use multiple SSH connections at the same time.
How Does SSH Encrypt?
SSH uses asymmetric encryption to ensure data security. When a user sets up SSH, a public and private key are generated. The public key is shared by the server and client, while the private key is hidden on the client machine.
The process begins when the server shares its public key with the client. The client uses this public key to encrypt data and send it to the server. Remember that only the server has the corresponding private key. So, only the server can decrypt and read this data. This ensures that no one else can intercept and decrypt the communication.
Suffice it say, SSH is by far the most common way to connect to a remote router, switch, or computer.
HTTP and HTTPS
HTTP (Hypertext Transfer Protocol) is a protocol designed to send data across the internet. HTTPS is like HTTP, but it adds a layer of security; the "S" stands for "Secure." If you have ever used the internet, then you have used HTTPS. In fact, you used it to get to this very post.
Additionally, HTTPS is not limited to web browsing. It's also used to access and manage network devices securely. HTTP provides a GUI to manage a network infrastructure.
HTTP and HTTPS operate the exact same way, but HTTP uses TLS to send data, while HTTP uses TCP/IP. TLS (Transport Layer Security) encrypts data exchanged between a client and server. It generally operates on port 43, while HTTP is aligned with port 8080.
HTTPS has to be enabled on a router to access it. Then, a certificate that the client recognizes needs to be installed on the router. It can be self-signed if testing, but for production, use a trusted certificate. Once the certificate is configured, navigate to the router's IP address from your browser. For example, https://<router-ip-address>.
As a caveat, always install the latest firmware on your router to ensure secure exchanges.
Console Access
Console access refers to accessing the device directly. An IT professional will use an Ethernet cable to connect directly to the router. Direct console access is used for initial setup, troubleshooting, or unlocking a machine.
To access a machine, you'll need a router, a PC, and an Ethernet cable connecting them. Refer to the router's manual to verify the IP address. Since it is not on the internet, HTTP can be used to access the router.
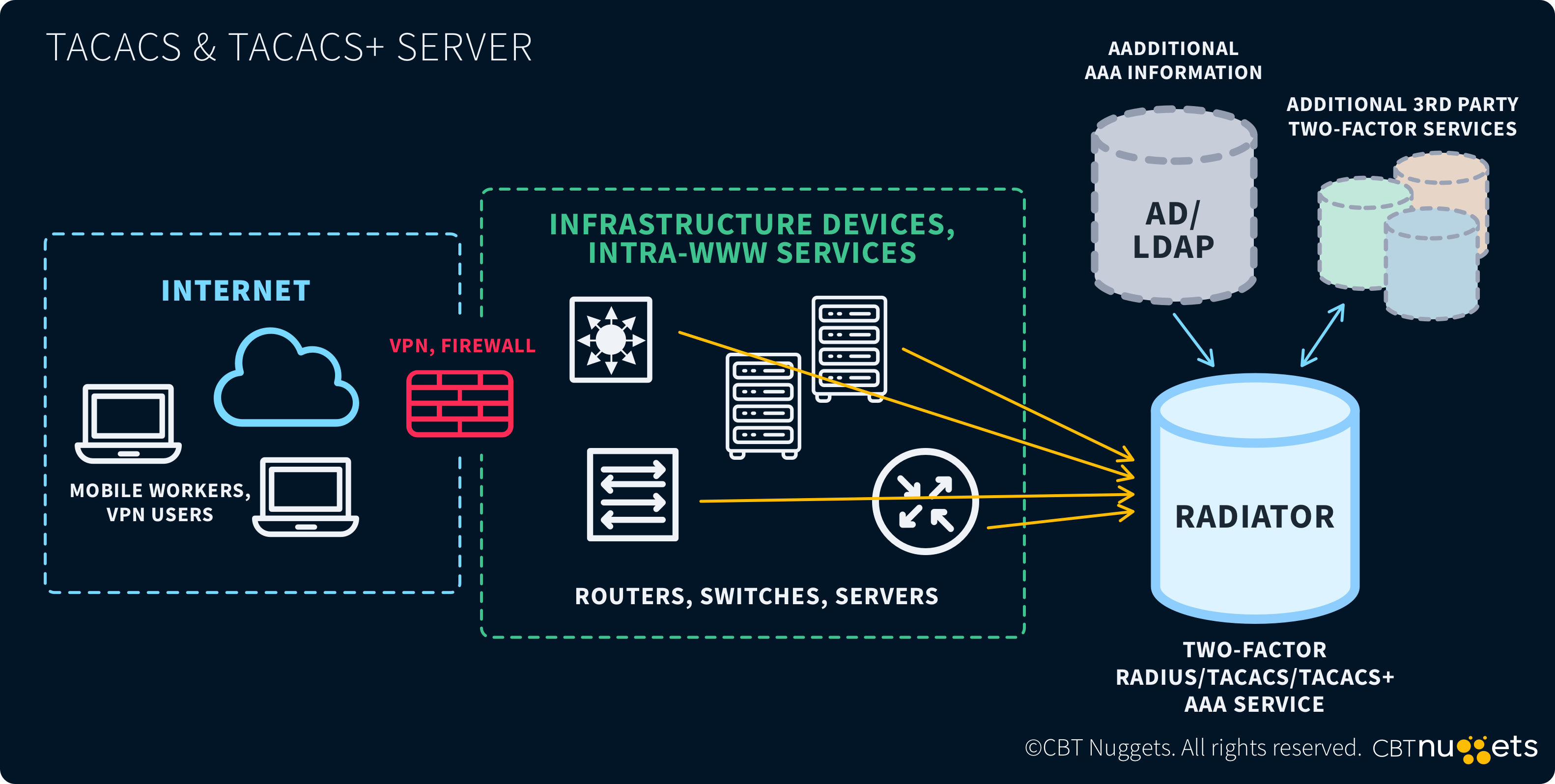
TACACS+ and RADIUS
TACAC+ and RADIUS are both protocols designed to control access to network devices. Yet, each does so in a different manner. Let's review each now.
TACACS+
TACACS+ is an authenticating, accessing, and accounting (AAA) protocol for network devices. It is a TCP/IP protocol that runs over port 49. TACACS+'s goal is to provide authentication and roles to users accessing devices.
One thing to consider is TACACS+ is a service that provides authorization to users. It is not used to control network devices itself. TACACS+ works in conjunction with other tools such as SSH to ensure secure access to users. It is also in charge of dishing out appropriate roles to users logging in. For example, the ability to install a certificate on a router is governed by a TACACS+ role.
RADIUS
RADIUS is another AAA protocol used to manage network devices. While there are similarities between the two, they also have plenty of differences. TACACS+ is used in enterprise environments to control and manage access, while RADIUS is used in ISP environments, Wi-Fi settings, and remote access scenarios. Another important difference is that RADIUS uses UDP. Also, it only encrypts the password, so everything else is plain text.
RADIUS is more robust and lightweight, though it does not have as thorough auditing as TACACS+. RADIUS logs when a user enters and leaves a remote device but doesn't log specific commands, while TACACS+ provides the ability to do both.
Ultimately, both TACACS+ and RADIUS serve as essential AAA protocols. TACACS+ offers more granular control and detailed auditing for enterprise environments, making it ideal for managing access to critical network devices. RADIUS provides a lighter and more scalable solution for broader network access scenarios.
Cloud-Managed Access
Cloud-managed access provides access to network infrastructure hosted on the cloud. It allows monitoring and configuring through a cloud-based platform like AWS or Azure. It also removes the upfront cost of purchasing, maintaining, and updating on-premise solutions. The goal is to provide a one-stop-shop access point to all your cloud-based infrastructure.
Key Features and Advantages of Cloud-Managed Access
Cloud-managed access yields a host of advantages, each of which is hard to duplicate with on-premise solutions. For the sake of illustration, I'll refer to AWS, but these concepts will apply to any cloud solution.
Centralized
The centralized aspect is maintained and updated by the cloud host. It is also designed for easy access, control, and auditing of each device in the cloud. Examples of cloud access on AWS would be AWS Network Manager and AWS Transit Gateway.
Secure
Cloud-managed access points offer built-in security features. The provider is responsible for upgrading and maintaining the software itself.
Automation and Integration
AWS provides tons of options for automation. These choices allow you to integrate network management with other AWS services. For example, you can trace user logins with Amazon CloudWatch. Or, use AWS Lambda to trigger events when network events take place.
Global Reach
AWS’s global infrastructure allows you to access network resources anywhere in the world. Its global nature nearly guarantees consistent performance and connectivity worldwide.
Best Practices for Network Device Management
Several steps can ensure your device management scheme is safe and effective. Let's go over some best practices that are useful regardless of access method.
Use Strong Security Practices
When possible, implement multi-factor authentication (MFA) to ensure maximum security. Use role-based authentication (RBAC) to ensure only necessary employees have access to resources. Try to segment the network based on security needs. VLANs are useful for quarantining the network if a segment is compromised.
Standardize Configuration Management
Automate configuration with tools like Ansible, Kubernetes, or CloudFormation. Configuring and deploying resources via templates ensures rapid-fire and error-free network solutions.
Regular Audits and Compliance
Make sure all network access is logged. TACACS+ and RADIUS are perfect solutions for this. All changes to configuration files should be documented and added to version control. Having comprehensive logs to refer to is invaluable while troubleshooting errors.
Combining Multiple Access Methods for Robust Management
It's vital to have multiple ingress routes to your network devices. Make sure you can access them via SSH, HTTPS, and direct access. Also, verify connectivity through VPNs and RDPs. If disaster strikes, it's best to have as many access points as possible.
Final Thoughts
Effective network device management hinges on a robust and versatile access strategy. To ensure that you can manage and troubleshoot network devices under various conditions, try to incorporate multiple access methods, including SSH, HTTPS, and direct console access.
Leveraging advanced protocols like TACACS+ and RADIUS enhances security and auditing. Cloud-managed access offers scalability and centralized control. Implement best practices such as strong security measures, configuration management, and regular audits.
These steps will help you maintain a reliable network environment, and a good understanding of each concept will bring you one step closer to acing the CCNA.
Want to try a CBT Nuggets course? Get a free 7-day trial.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.