Azure Security Center: Top 3 Best Practices

As cloud computing becomes increasingly pervasive, so will threats to the data stored within it. Many corporations cite data security as a primary concern regarding cloud migration. After all, they're expected to migrate their customers' sensitive data to Azure, integrate existing software and APIs, and then train current employees—or hire new ones—to administer the cloud security environment.
These steps can be rife with pitfalls, such as insecure APIs, access management intrusions, user error, and everything in between. While security concerns are warranted out of due diligence, Microsoft provides us with an incredible tool to combat every one of them: The Azure Security Center.
Let's discuss some security threats that can be identified and mitigated using the Security Center. This article will then walk through the three best practices regarding Azure Security Center—implementing secure governance, access control, and safeguarding data and resources.
Azure Security Center: A Brief Overview
The Azure Security Center is a one-stop shop for all your security needs. Virtually every service required for a production environment can be monitored here. For instance, let's say your company has just spun up five new virtual machines and needs to know which ones are currently encrypted, online, and installed with antivirus software. All of that information is located on the Azure Security Center dashboard. Here is an example of the dashboard:
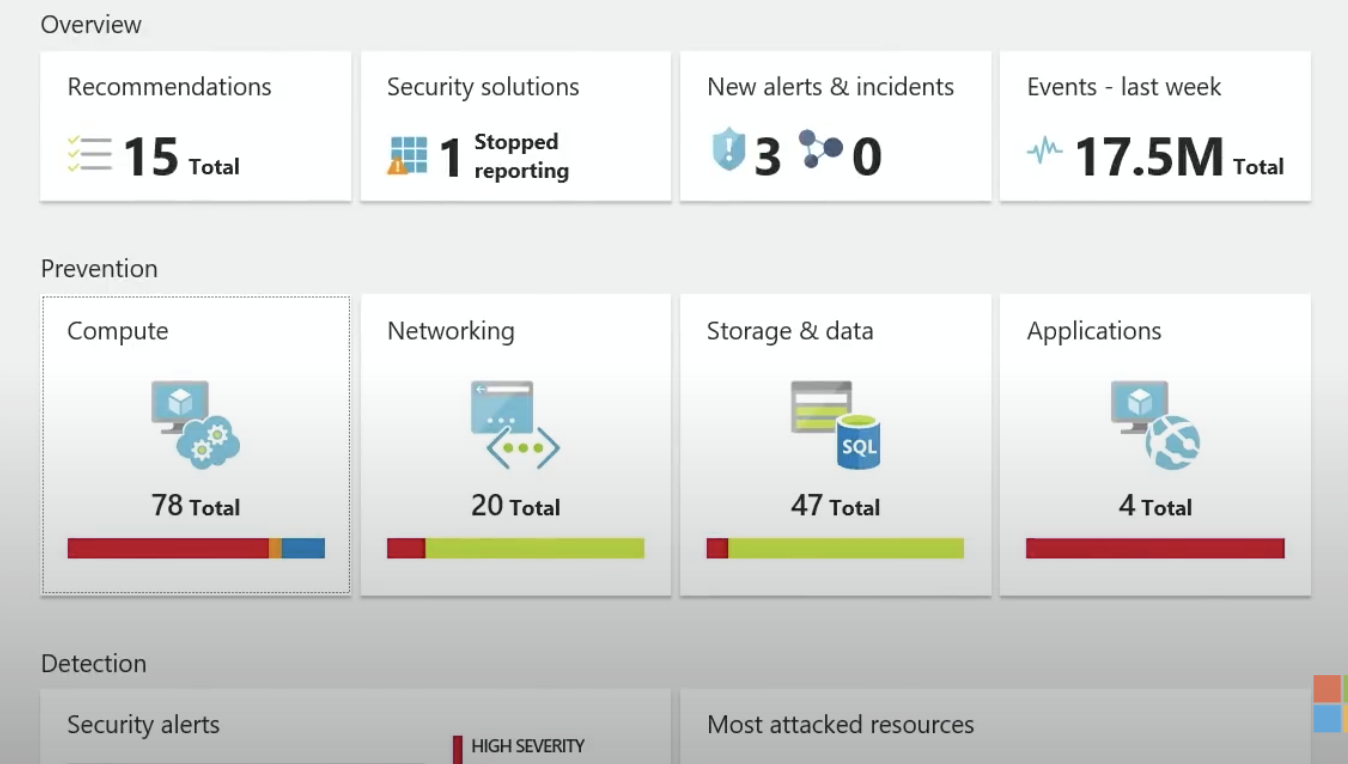
As shown above, the Security Center provides a dashboard that provides secure alerts, recommendations, the most attacked resources, and much more. Regarding attacked resources, let's discuss the most common attack against cloud environments: RDP Brute Force Attacks.
Threat #1: RDP Attacks
The list of potential network security threats to enterprise-level businesses is long. RDP (Remote Desktop Protocol) attacks are among the most common attacks against an IaaS (Infrastructure as a Service) environment.
This is a DDoS (Distributed Denial of Service) attack where an attacker continually tries to RDP into a particular VM, thus clogging up the ports. The most common port target is port 22, the dedicated port for the SSH protocol. This attack will prevent regular users from accessing company resources and significantly hinder productivity.
In the era of COVID, this vector of attack is particularly threatening. Luckily, Azure Security Center provides a method to mitigate this threat and strikes an excellent balance between convenience and security.
Azure handles these threats through a nifty feature called Just-In-Time VM Access. JIT VM Access allows administrators to keep particular ports open only for a given time. For instance, we may only want specific ports open to provide admins enough time to log onto the virtual machines and perform required updates.
Using JIT VM Access, we can configure the ports to be opened between 1:00 PM and 2:00 PM on Saturdays. In other words, it's all about the Golden Rule of IT Security: Least privileged access!
Threat #2: Data Breaches
A CEO's worst nightmare is answering a call in the middle of the night that begins with these three words: we've been hacked. Generally, the worst hacks involve data integrity—the unauthorized insertion, deletion, and retrieval of production data.
Preventing the loss of data, especially customer data, is extremely important. Let's look at how Azure Security can mitigate this threat.
First, data stored on Azure will likely be in Cosmos DB—a NoSQL database—or some flavor of SQL database. Either of these database types can easily be spun up on the cloud.
Better yet, all data stored on Azure is encrypted at rest by default, which is one less thing to worry about. However, once you or your software developer has transferred the data into your new database, ensure a SQL Vulnerability Assessment runs on the Azure Security Center.
The SQL Vulnerability Assessment (SVA) is an invaluable tool that lists all possible security threats to your database and the connections between them from highest to lowest. The SVA not only lists each security vulnerability but also provides actionable advice to mitigate the threats. For instance, in the image above, one High Vulnerability action item states that the Server Principal Guest should not be a member of any role. Without getting too deep into the specifics, database roles are the primary method of separating Azure duties.
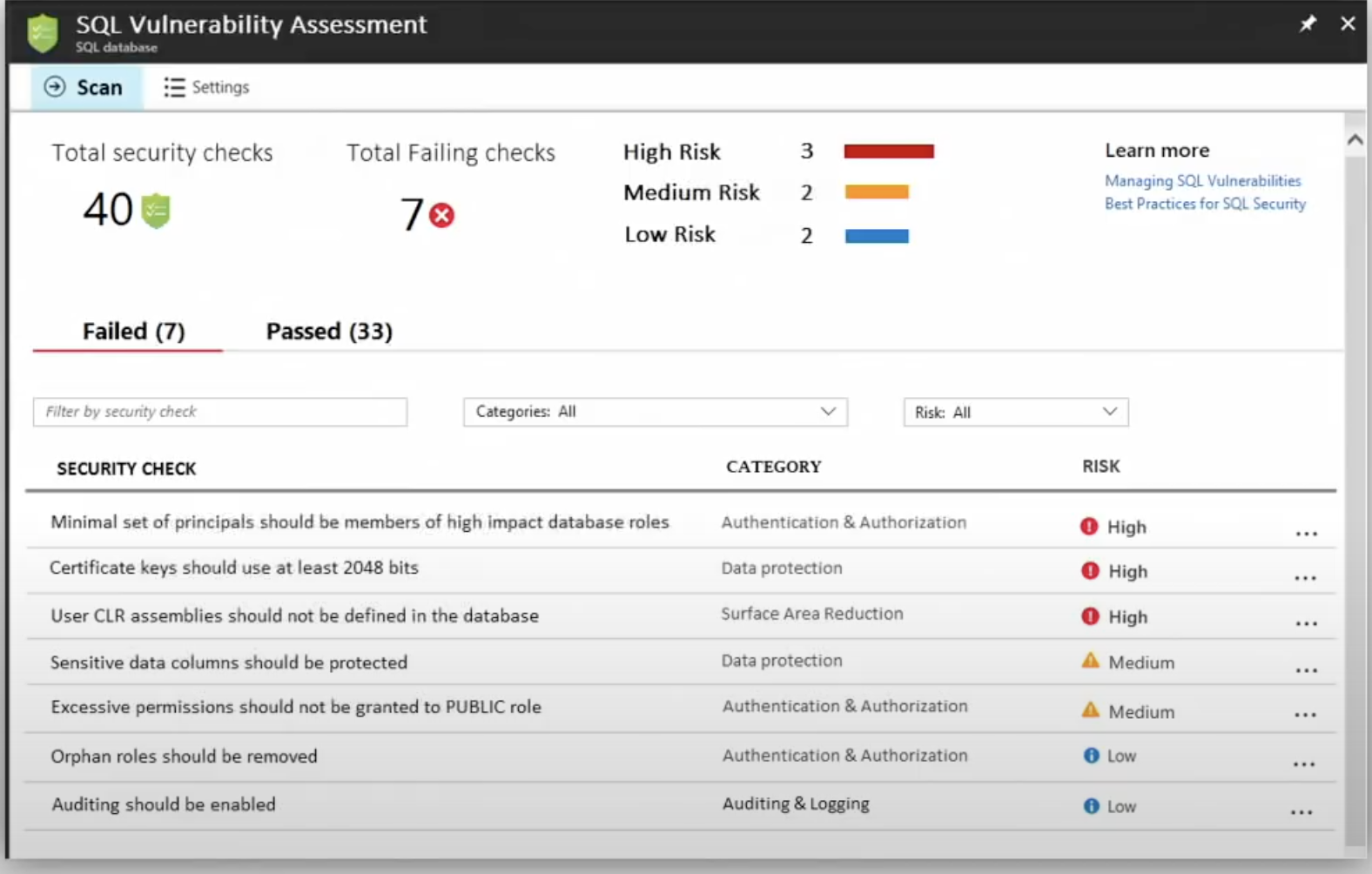
If a Guest principal were inadvertently part of an Admin role, an anonymous user could update, drop, and manipulate tables. Not good. Luckily, the SVA finds this and many other types of security risks. Naturally, this isn't the only way for a data breach to occur. There are many ways this tragedy can occur. Thankfully, numerous broad actions can be taken to mitigate these threats as much as possible. Now that we've touched on some specific threats, let's dive into which portions of cloud security the user is responsible for and the three best practices to mitigate events in general.
Azure Best Practices
Whether a corporation is leveraging Google Cloud, Azure, or AWS, there will always be a concept of shared responsibility. Shared responsibility is the idea that the cloud service provider handles certain security portions; the other is the user's responsibility. Shared responsibility can boil down to a simple concept: the cloud provider maintains the security of the cloud while the user protects the cloud.
While cloud security is vitally important, let's focus on the cloud user's three core responsibilities instead of the cloud provider. The first responsibility is to protect the employees and customers via identity access and management policies. This means ensuring the least privileged access to all employees. Secondly, the cloud customer's responsible for protecting the applications they are hosting. Lastly, all services are the sole responsibility of the cloud customer.
Let's look at how these responsibilities are a pillar for Azure's following three best practices.
Control Access
A cloud that the whole world could access would be worthless. After all, it is a sacred bond between a company and its customers that their private data is kept confidential. Controlling which employees have access to different portions of the cloud is the first best practice to discuss.
MFA
MFA (Multi-factor authentication) should be implemented immediately, especially if you have a remote team. MFA ensures that an employee knows a password and has a device that can be used as additional authentication. The most common method is a phone number in which a passcode is pushed.
MFA is invaluable because it relies on three main principles: something you are (e.g., biometric data), something you have (e.g., a smart card), and something you know (e.g., a passphrase). For instance, if a hacker steals an employee's password, he would only have something the user understands. Therefore, MFA makes it far more challenging to access a system via theft or brute force algorithms. If you need to know which employees have not activated MFA, head to the Azure Security Center.
Active Directory
In addition to MFA, user identities must be secured using Azure Access Directory. Managing and maintaining user accounts, roles, and permissions is vital. Ensure that all access is handled in this single location. The AD permissions will cascade down to all related services.
Whenever managing Azure AD (now known as Entra) groups, always follow the principle of least privileged access. The best way to do this is to create a user with no access and then grant access pertinent to that employee's job role. Additionally, enable conditional access whenever possible. For instance, is there a reason a software developer should test production API at 3 in the morning? Maybe, but probably not. So, configure their AD group to only have access during business hours. T
his is one such example of controlling access via conditional requirements. Access control plays a pivotal role in a tightly run Azure environment, but let's see how to implement best practices regarding cloud governance and administration.
Implement Secure Governance
The most critical aspect of secure data governance is having well-trained employees. Experts are vital for overseeing the vast information on the Azure Security Center. While it may seem obvious to have well-trained employees administer Azure Cloud, it can sometimes fall through the cracks for several reasons.
One is that a corporation may initially underestimate the complexity associated with cloud governance. Two, deadlines and skill shortages may impede their search for qualified candidates. In this case, recruiting from within may be a great choice. The first best practice of secure data governance is ensuring that Azure administrators thoroughly understand their duties.
Create Admin Accounts Proactively
Now that your company has qualified employees to work in the cloud, it is time to create the admin accounts. According to best practices, create two Azure admins who can act as Product Owners. This will ensure that at least two pairs of eyes are on all critical decisions. It also eliminates any single point of failure in case of an emergency.
Speaking of emergencies, create a separate Azure account that can be used if the primary one becomes compromised. In the same vein as having two admin employees, this will prevent any heartache if the original admin account is deleted or locked.
Audit, Audit, Audit.
Last but certainly not least, ensure a separate employee has read-only rights to Azure audit logs. Doing so will ensure that any possible error by either admin is promptly caught and any untoward activities are found. These logs can be found on Azure's Active Directory portal and help determine if any data and/or resources have been compromised. Regarding data and resources, let's discuss how these two assets can be secured in our final best practice.
Safeguard Data and Resources
Safeguarding data and resources is not just the administrator's responsibility but everyone's responsibility. That said, plenty of steps can be taken to mitigate any threat to either of these assets.
Monitor Azure Secure Score
The first best practice is to monitor the Azure Security Center continuously. All possible threats and security events are accounted for on its dashboard. Make sure that each threat is resolved promptly. Generally, the best way to do this is to dedicate a team or persons to a specific type of threat. That way, there is no confusion or finger-pointing if a situation escalates.
In addition to outlining security threats, Azure Security Center has a dashboard card called Azure Secure Score. On a scale from 1 to 100, Azure will rate your applications' security. Ensure the Secure Score is turned on for all applications.
Inject Secrets at Run Time
In the Wild West days of development, database or API passwords were placed directly into the application files. However, it is now a best practice to ensure this never happens. Any production password placed in an application file is a big violation of our customers' trust. Instead, ensure that the password (known as the secret) is injected at run time.
This DevOps strategy ensures that no one will know that password. Instead, when the application is built in Azure DevOps, an encrypted key is decrypted, and access to the specific resource is granted.
Web Application Firewalls
Lastly, I would be remiss in speaking of best practices without mentioning Web Application Firewalls (WAFs). A WAF is configured directly on your Application Gateway in Azure and helps detect malicious requests sent to your web application. It will protect from numerous threats, such as SQL injection and cross-site scripting (XSS) attacks. Also, an Azure WAF can protect up to forty websites, so don't worry about setting up one after another.
It also allows the user to filter various requests. For instance, a company can block certain countries and regions from accessing its web application. It comes with numerous other rules and is fully customizable. To configure a WAF, head over to the Azure Portal and type it into the search bar.
Wrap Up
If nothing else is remembered from this article, remember Azure Security Center. Live it, learn it, love it. All roads (with regards to security) lead right back to the Security Center. Large companies benefit the most from Azure Security, but Azure even offers Microsoft for Startups, which gives new companies access to technical resources, free cloud, and even marketing support.
Always consider the three best practices: control user access, implement secure governance, and safeguard data and resources. Control user access by leveraging the least privileged AD groups and MFA. Implement data governance by limiting the number of admins and always having a dedicated auditor. Safeguard data and resources by monitoring your security score like a hawk. And remember, a security score is only as useful as the number of resources it measures!
This article has barely scratched the surface of all the fantastic features in the Azure Security Center. However, by now, you may be convinced that it is a great tool and a one-stop shop for all your cloud security needs. Learning these best practices can help your company have a cost-effective, easy-to-manage, and secure infrastructure.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.