What is Port 5432?
by Colin Cohen | Published on October 11, 2024
Port 5432 is dedicated to PostgreSQL connections, allowing enterprise-level applications to communicate over the port to read and write data from and to PostgreSQL databases.
To understand port 5432, you need to understand PostgreSQL as well as relational databases in general.
PostgreSQL, like MySQL, is an open-source relational database system that uses Standard Query Language (SQL) to read and write databases. Applications communicate with PostgreSQL databases by establishing a connection with them through a server and then by sending SQL queries to them to perform CRUD (create, read, update and delete) database operations.
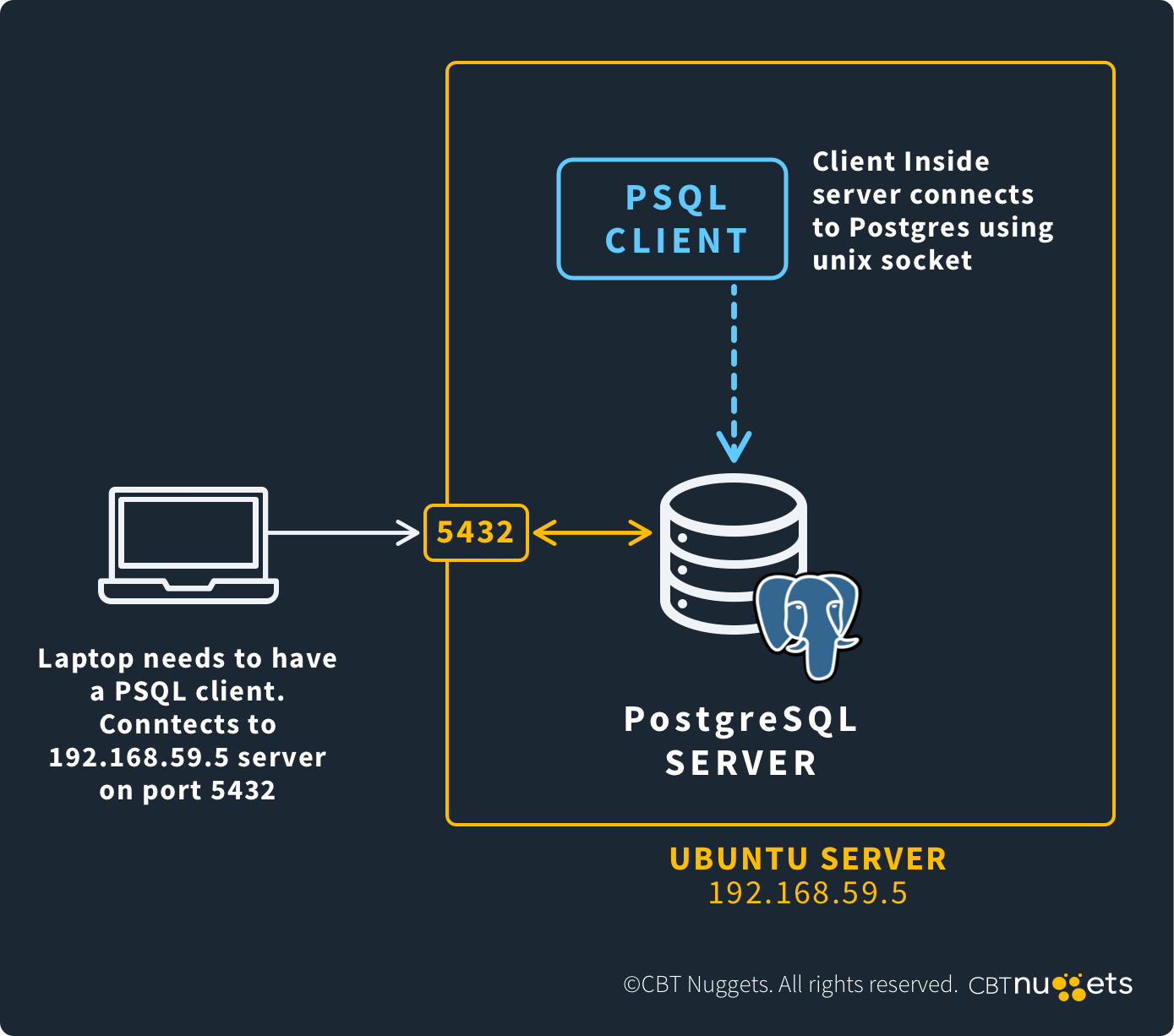
PostgreSQL servers listen on port 5432 for connections from applications running on PostgreSQL clients.
Technical Aspects
PostgreSQL applications communicate with PostgreSQL servers by establishing a connection over port 5432 and then sending a set of SQL queries to them. For example, if an application wanted to retrieve all data that was stored in a database table called Company, it would issue the following query to the server:
SELECT * FROM CompanyPostgreSQL applications are often user applications, such as web apps, but they can also be systems tools. The latter connects with PostgreSQL servers so database administrators can perform maintenance tasks.
PostgreSQL running over port 5432 exists in the application layer of the Open Systems Interconnection (OSI) model.
Protocol Association
PostgreSQL clients that connect with PostgreSQL servers over port 5432 use Transport Control Protocol (TCP) as a transport protocol. This is because TCP, unlike User Datagram Protocol (UDP), establishes the kind of reliable connections necessary for database applications.
What is Port 5432 Used For?
PostgreSQL uses port 5432 to facilitate connections between PostgreSQL clients and servers. Organizations use the port to run enterprise-level applications that require heavy database writes and use advanced database features.
Primary Functions
Port 5432 facilitates connections from PostgreSQL clients to PostgreSQL servers. It allows database applications running on PostgreSQL clients to read and write data from and to PostgreSQL databases. Both user applications and systems tools may communicate with PostgreSQL databases over port 5432.
Industry Use Cases
The primary use case of PostgreSQL databases is enterprise-level applications that require heavy database writes. Organizations may also use PostgreSQL when their applications require advanced database features, such as stored procedures, triggers, and materialized views, that are not available (or not as effective) in other database systems.
PostgreSQL applications communicate with PostgreSQL databases over port 5432 using a client-server model.
How to Ensure Port 5432 is Secure
Due to the serious exploitation risks of port 5432, it's crucial to follow best practices for securing it. You should also know how to close the port on your devices.
Exploitation Risks
There are a number of serious exploitation risks associated with using PostgreSQL on port 5432, especially remote code executions (RCEs). As many enterprise PostgreSQL applications house sensitive data, these vulnerabilities can have dire consequences for organizations. Exploits can lead to unauthorized access to data, significant data loss, and even ransomware attacks. So, it is critical that you secure port 5432.
Best Practices for Security
If you are not using PostgreSQL, you should block access to port 5432 on your devices. If you are using PostgreSQL, you should only allow access to your PostgreSQL servers from known IP addresses. You should also make sure that your devices always run the latest versions of PostgreSQL. Finally, you should implement rules that require users to have strong credentials.
Disabling and Closing Port 5432
To block port 5432 in Windows, do the following:
Open the Firewall Control Panel by running firewall.cpl in a command prompt.
Select Advanced Settings and click Inbound Rules.
Click New Rule under Action.
Select TCP and Specific local ports, and enter 5432.
Under Action, select Block the connection and click Next.
Under Profile, select Domain and Private and click Next.
Under Name, enter a name for the rule and click Finish.
Repeat steps 2 through 7 for Outbound Rules.
Monitoring and Troubleshooting Port 5432
If your organization uses port 5432 for PostgreSQL, you need to know how to detect traffic on the port and resolve port-related conflicts. Here's how:
Detecting Port 5432 Activity
To determine whether port 5432 is open on a device, run the following command from a command prompt or terminal:
netstat -aonResolving Port 5432 Conflicts
Only one service can listen to port 5432 at a time. If you want to run a PostgreSQL server on port 5432 and discover through the netstat command that another service is listening on this port, you will need to disable this other service before you can start the server.
Frequently Asked Questions
The following FAQs answer questions typically asked about port 5432 and provide a basic understanding of the port and its uses.
What is Port 5432?
Port 5432 is for making database connections between PostgreSQL clients and servers. Applications communicate with databases over the port to read and write data. Organizations typically use PostgreSQL when they require extensive database writing and advanced features not available with other database systems.
Is PostgreSQL Port 5432 TCP or UDP?
When using PostgreSQL over port 5432, you are using TCP as a transport protocol. This is because TCP, unlike UDP, facilitates the type of reliable connections that are required for PostgreSQL applications.
Is Port 5432 Vulnerable?
Hackers have exploited port 5432 through numerous RCE vulnerabilities, which can have serious consequences for your organization. To protect it against these exploitations, you should implement the recommendations detailed in the Best Practices for Security section.
Conclusion
PostgreSQL servers listen on port 5432 from clients looking to connect to PostgreSQL databases. Many enterprise-level applications rely on PostgreSQL to write large amounts of data and implement advanced database features. Due to serious vulnerabilities associated with port 5432, it is critically important that you properly secure the port on your devices.