What is Port 31337?
by Colin Cohen | Published on July 18, 2024
Port 31337 has been used by a number of malicious backdoor applications, most notably Back Orifice, to remotely control compromised devices. It also has legitimate purposes, as it’s the default listening port for ncat.
Background of Port 31337
Backdoor hacking tools such as Back Orifice often use port 31337, but the ncat command also uses it. Both allow clients to remotely control servers.
Definition of Port 31337
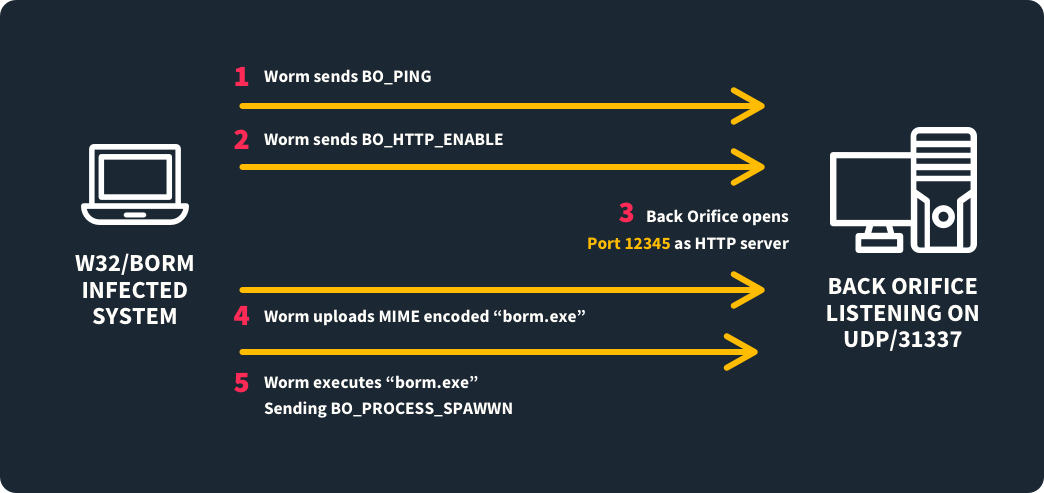
Port 31337 was originally created as a hacker port. Back Orifice, a backdoor application that lets hackers remotely read and write files on Windows computers, used the port when communicating with a compromised computer. Many other backdoor applications use port 31337 for similar reasons, such as:
Back Fire
Baron Night
Beeone
Port 31337 also has legitimate uses. The ncat command, which lets you read and write data over a network, listens on the port by default, perhaps in homage to Back Orifice. It should be noted that hackers can misuse ncat for similarly malicious purposes as Back Orifice if it’s not properly secured.
Technical Aspects of Port 31337
Applications that use port 31337 implement a client-server architecture, where a client remotely accesses a server that is listening on the port. Once connected to the server, the client can perform functions as if it were the server.
Tools that use port 31337 operate in the application layer of the Open Systems Interconnection (OSI) model.
Protocol Association
You can use both Transport Control Protocol (TCP) and User Datagram Protocol (UDP) on port 31337 as a transport protocol. Hacker tools such as Back Orifice tend to use TCP while the ncat command can use both protocols.
What is Port 31337 Used For?
Applications use port 31337 so that clients can administer remote devices. While the port has historically been used by hacking tools such as Back Orifice to maliciously control compromised systems, the ncat command uses the port for legitimate purposes.
Primary Functions
The primary purpose of port 31337 is to be a listening port in client-server applications that support remote computer administration. Hacking tools such as Back Orifice use the port as a backdoor into compromised systems. The ncat command uses it to legitimately administer systems remotely.
Industry Use Cases
Historically, port 31337 has been associated with hacking tools like Back Orifice. These tools let hackers control remote computers. But some organizations use the port for ncat, a standard command-line tool that was developed for legitimate remote administration of systems.
How to Ensure Port 31337 is Secure
As exploitation risks associated with port 31337 are high, it’s important to properly secure the port. You should follow best practices to secure it.
Exploitation Risks
The exploitation risk associated with port 31337 is as high as it comes. With the port open, a hacker could run any number of backdoor applications that could give it full control of a device. A hacker could even exploit the ncat command, a legitimate application, to give them control of a device through the port.
Best Practices for Security
At a bare minimum, you should limit access to port 31337 to private IP addresses within your organization. But you should probably consider completely blocking it on all your devices. Even if you use the ncat command, you should change its default listening port.
Disabling and Closing Port 31337
To block port 31337 in Windows, do the following:
Open the Firewall Control Panel by running firewall.cpl in a command prompt.
Select Advanced Settings and click Inbound Rules.
Click New Rule under Action.
Select TCP and Specific local ports, and enter 31337.
Under Action, select Block the connection and click Next.
Under Profile, select Domain and Private, and click Next.
Under Name, enter a name for the rule and click Finish.
Repeat steps 2 through 7 for Outbound Rules.
Monitoring and Troubleshooting Port 31337
If your organization uses port 31337 for the ncat command, you need to be able to detect whether the port is open on your devices. You also need to know how to troubleshoot conflicts on the port.
Detecting Port 31337 Activity
To determine whether port 31337 is open on a device, run the following command from a command prompt or terminal:
netstat -aonResolving Port 31337 Conflicts
Only one service can listen to port 31337 at a time. If you want to run the ncat command on port 31337 and discover through the netstat command that another service is listening on this port, you will need to disable this other service before you can start ncat.
Frequently Asked Questions
The following FAQs answer questions typically asked relating to port 31337. They provide a basic understanding of the port and its uses.
What is TCP Port 31337 Used For?
TCP port 31337 has traditionally been used by hacker tools such as Back Orifice to remotely control a remote device. The ncat command also uses port 31337 for legitimate purposes as its default listening port. Though hackers can even misuse ncat for malicious purposes.
What is Port 31337 TCP?
Hackers often use port 31337 to control remote devices. They do this by connecting to a compromised device over the port. The ncat command, which is a legitimate tool for reading and writing data over a network, listens on port 31337 by default.
What Ports Do Hackers Use?
Hackers often use port 31337 to remotely control a compromised computer. While the port was first used by Back Orifice, many backdoor tools since have used the port too. Hackers often use other ports as well, such as 21, 22, 23, 80, 443, 445 and 3389.
Conclusion
Port 31337 is commonly associated with hacker tools such as Back Orifice, which allow malicious third parties to control compromised devices. The ncat command also uses the port, for legitimate purposes. Because of the way the port has been exploited, it is critical that you know how to secure it.