What is Port 135?
by Colin Cohen | Published on June 13, 2024
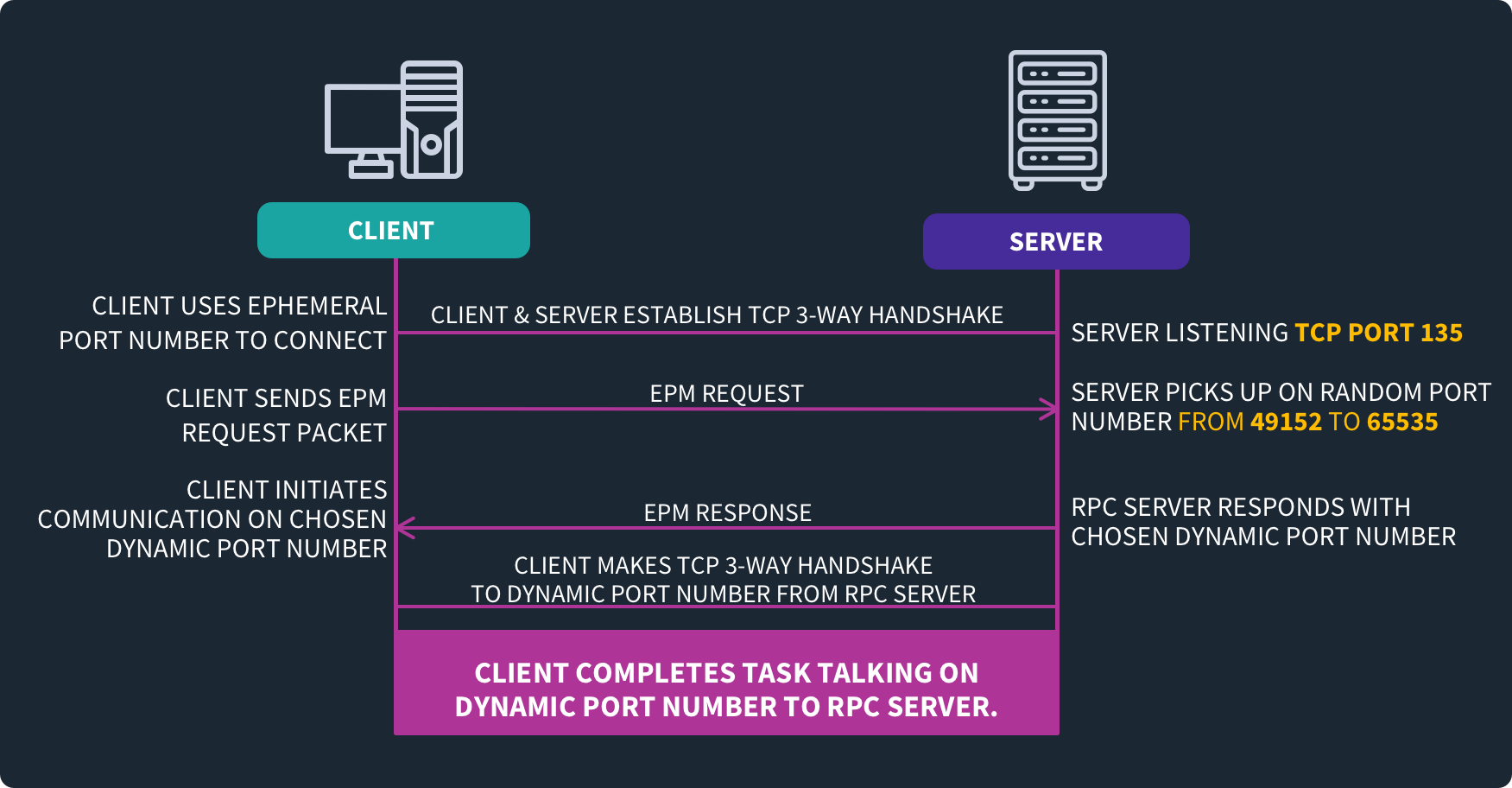
Port 135 is dedicated to the Windows Remote Procedure Call (RPC) Mapper Service.
Many crucial services, such as Windows Server Active Directory, rely on the port for remote client-server communication.
What is Port 135?
You use port 135 in Windows environments when you have clients and servers that need to remotely connect to each other. They use the RPC Mapper Service running on the port to determine what services are available to them and to learn which ports they are available at.
Definition
Devices in Windows environments will often run the RPC Mapper Service on port 135. This allows other machines that remotely connect to them to learn what services are running and on what ports they can connect to them. These services typically relate to remote access and management.
Understanding Port 135
You use port 135 for making remote procedure calls using the RPC protocol. The protocol lets you execute functions on a remote device over a network. It operates in both the application and transport layer of the Open Systems Interconnection (OSI) model used in network communication.
Protocol Association
When using port 135 for the Windows RPC Mapper Service, you are implementing the RPC protocol. It allows devices to remotely communicate with each other over a network to determine what services are available and how to connect to them.
What is Port 135 Used for?
Port 135 enables remote communication between clients and servers in Windows environments. Important services such as Windows Management Instrumentation (WMI) and AD rely on this port being open so that they can function properly.
Primary Functions
The purpose of port 135 is to facilitate remote communication between clients and servers in a Windows environment. Without access to port 135 on devices, other devices would be unable to determine what services are available on them, nor would they be able to know on which ports these services are running.
Industry Use Cases
A typical example of a service that relies on port 135 is Windows Management Instrumentation (WMI). It allows administrators to remotely administer client devices. If port 135 is not open on the remote computer, WMI will not function.
Another service that depends on port 135 is AD. This is a directory service that allows clients to remotely access important network resources.
How to Make Sure Port 135 is Secure
Port 135 is susceptible to several serious exploitations, so it is important for you to know how to secure it properly.
Exploitation Risks
If port 135 is left open on the public Internet, it can leave devices vulnerable to dangerous attacks such as remote command executions (RCEs), sensitive data exposure, and distributed denial-of-service (DDoS) attacks. Because of this, you must properly secure port 135 on your client and server devices that use the port.
Best Practices for Security
If you are not working in a Windows environment or don’t need remote access and management, you probably should close port 135 on your devices.
Otherwise, you should restrict access to port 135 in your firewall to local IP addresses only. You should also consider implementing authentication and encryption mechanisms on the port, such as SMB signing, IPsec, and Kerberos.
Disabling and Closing Port 135
To close port 135 in Windows, do the following:
Open the Firewall Control Panel by running firewall.cpl in a command prompt.
Select Advanced Settings and click Inbound Rules.
Click New Rule under Action.
Select TCP and Specific local ports, and enter 135.
Under Action, select Block the connection and click Next.
Under Profile, select Domain and Private and click Next.
Under Name, enter a name for the rule and click Finish.
Repeat steps 2 through 7 for Outbound Rules.
Monitoring and Troubleshooting Port 135
If your organization uses the RPC Mapper Service for remote access and management of your devices, you need to know whether port 135 is open on them. You also need to know how to troubleshoot conflicts on the port.
Detecting Port 135 Activity
To determine whether port 135 is open on a device, run the following command from a Windows command prompt:
netstat-aonResolving Port 135 Conflicts
Only one service can listen to port 135 at a time. If you want to run the RPC Mapper Service on port 135 and discover through the netstat command that another service is listening on this port, you must disable this other service before you can start the RPC Mapper Service.
Frequently Asked Questions
The following FAQs answer questions typically asked relating to port 135. They provide a basic understanding of the port and its uses.
What is TCP port 135 used for?
You use TCP port 135 for remotely connecting clients and servers in a Windows environment through the RPC Mapper Service. It allows devices to see what services other devices provide and on which ports these services are available.
Can port 135 be exploited?
If you leave port 135 open on the public Internet, your devices can be susceptible to serious exploitations, such as RCE and DDoS attacks. So it’s important to implement security practices as described in the How To Make Sure Port 135 is Secure section.
Is it safe to block port 135?
If you don’t operate in a Windows environment or don’t need remote access and management, it is safe to block port 135 on your devices. But if you do need remote access and management in a Windows environment, you should leave the port open and instead implement security practices such as those described in the How To Make Sure Port 135 is Secure section.
How do I know if port 135 is listening?
You can check if a device is listening on port 135 by using the netstat command, as described in the Monitoring and Troubleshooting Port 135 section. Both clients and servers need to listen on this port to enable important Windows services such as WMI.
Conclusion
You use port 135 to implement the RPC Mapper Service in a Windows environment. It allows clients and servers to communicate for remote access and management. However, as port 135 is susceptible to various serious exploitations, you must know how to properly secure the port.