What is XSOAR and How is it Used?

Quick Answer: XSOAR platforms take security orchestration, automation, and response beyond traditional SOAR by adding advanced features like case management and deeper automation. This is helping organizations increase efficiency and response time while reducing the amount of hands-on work analysts need to do upfront.
As technology advances and becomes more accessible, cyber threats evolve just as quickly. Thankfully, security monitoring and alerting solutions have also become more advanced, allowing organizations the chance to identify and respond to threats in real-time.
One such solution is XSOAR, which is known as Extended Security Orchestration, Automation, and Response. It’s also referred to as Cybersecurity Orchestration, Automation, and Response.
This article will discuss the features and benefits of XSOAR and touch on how organizations are implementing XSOAR to help protect their networks.
What is XSOAR? How Does it Work?
Traditional security platforms, referred to as SOAR, offer the components of security orchestration, automation, and response. XSOAR further extends those capabilities by adding features like case management and more versatile automation.
There are a few key components of XSOAR:
Orchestration is crucial to integrating all the organization’s security tools for a streamlined workflow. This helps analysts detect and confirm problems more efficiently across multiple tools.
Automation helps reduce the amount of time analysts and engineers spend responding to incidents by working through predefined runbooks. This is especially useful for filtering through potentially erroneous alerts.
Response, similarly to automation, helps reduce the amount of time between detection and mitigation.
Case management provides a centralized system for tracking ongoing and closed incidents, much of which can be updated in real-time via automation.
XSOAR provides greater flexibility and customization than traditional SOAR platforms. It is designed to reduce the time spent on manual input for incident analysis and response. XSOAR also empowers organizations to fully integrate all of their security tools and interact as one unit rather than separate tools.
What are the Key Features of XSOAR?
What separates XSOAR from traditional SOAR are the enhancements like centralized incident management, advanced automation and playbooks, seamless integration with security tools, and collaboration tools.
Centralized Incident Management
Teams can more efficiently manage, track, and work through incidents. This provides more visibility to those who need it in a more timely manner than traditional incident response workflows.
Advanced Automation and Playbooks
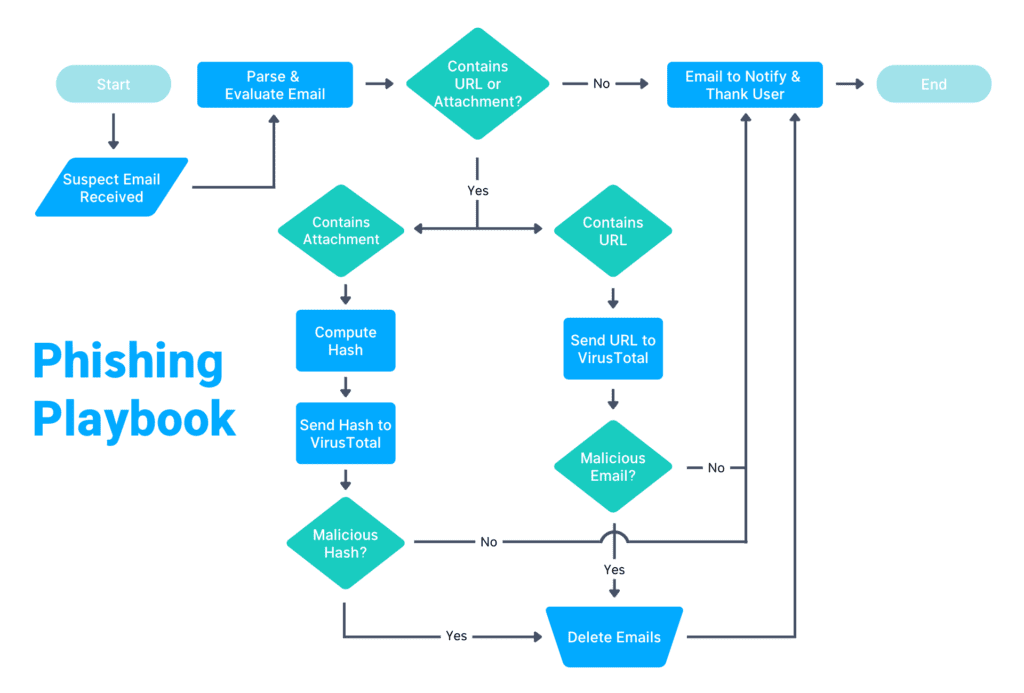
XSOAR provides automation capabilities through playbooks, which help reduce the time analysts spend on tasks such as responding to phishing attempts and analyzing potentially malicious code. This allows analysts to spend more time on higher-tier tasks and projects.
Seamless Integration with Security Tools
By integrating tools like SIEM, EDR, vulnerability scanners, and threat intelligence feeds, XSOAR gives security teams a unified view of their organization's security posture and attack surface.
Collaboration Tools
XSOAR’s collaborative capabilities make it easier for different teams and roles to work together toward a common goal, whether that’s incident response, vulnerability management, or forensics.
What are the Benefits of Using XSOAR?
XSOAR provides many benefits, such as improved efficiency, quicker and more effective incident response, scalability, and, most importantly, improved security posture. Its advanced automation capabilities reduce analysts' hands-on-keyboard time. These automations also increase the speed at which organizations can react to threats, reducing their overall impact.
Centralized incident response workflows provide security teams with comprehensive overviews of the overall threat landscape and security posture. This allows teams to work together to resolve incidents quickly and efficiently. XSOAR is also scalable and can benefit organizations of any size.
What is XSOAR Used For?
XSOAR is used for a multitude of security activities, from incident response to threat hunting. It automates response efforts for things like phishing attacks and initial malware containment, proactively detects and conducts threat-hunting activities using threat intelligence information, streamlines patch management activities, and automates compliance efforts, helping organizations maintain compliance with less hands-on activity.
How to Implement XSOAR in Your Organization
Organizations should be mindful of a few key components to successfully integrating XSOAR into their existing environment:
Assess Your Security Needs
Tools and platforms are only effective when used properly. Before integrating XSOAR within an environment, stakeholders should identify the areas in which they believe XSOAR can make the most impact. For example, a financial institution implementing XSOAR could start by automating phishing email investigations, reducing response time from hours to minutes.
Integrating with Current Systems
Prepare for a smooth integration with minimal disruption to existing systems and tools by conducting a phased rollout. Start with non-critical workflows, test automation playbooks in a controlled environment, and ensure proper logging and monitoring are in place before full deployment. This approach helps identify potential conflicts early and ensures a seamless transition.
Training and Onboarding Teams
Ensure all team members receive hands-on training tailored to their roles. Start with foundational courses covering XSOAR’s interface, key features, and workflows. Then, provide role-specific training, such as playbook creation for security engineers and incident response workflows for analysts.
Conduct practical exercises, like simulated threat scenarios, to reinforce learning. Encourage ongoing skill development by assigning a dedicated administrator to update training materials and facilitate regular workshops on new automation and integration techniques.
What are the Challenges and Considerations Associated with XSOAR?
Like other technologies, XSOAR platforms do not come without their issues. While these points are not meant to steer anyone away from using an XSOAR platform, users and stakeholders alike should be aware of the following:
Initial Implementation Complexity
As with any new implementation, introducing an XSOAR platform into your environment can be time-consuming and frustrating in the beginning. To ease the complexity of implementation, start with a phased rollout, automating low-risk tasks first before integrating with critical systems.
Playbook Customization
Customizing playbooks may also take a lot of time upfront, which could put analysts and engineers under additional pressure as they create and validate playbooks within the new XSOAR platform. To reduce customization time, leverage prebuilt playbooks for common security incidents before developing custom ones.
Ongoing Updates and Maintenance
An XSOAR platform is one more item to consider when working through budget meetings, security updates, compatibility considerations, and other activities. Be sure to keep that in mind when adopting an XSOAR platform to help your environment.
Conclusion
XSOAR, or Extended Security Orchestration, Automation, and Response, platforms are helping organizations drastically improve their security posture by automating smaller tasks. This reduces the risk of human error and increases response times. XSOAR platforms offer capabilities such as threat detection, vulnerability management, and seamless tool integration.
Want to learn more about XSOAR? Consider one of CBT Nuggets' Palo Alto training courses.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.