What is RADIUS (Remote Authentication Dial-In User Service)?

Quick definition: RADIUS is a network protocol providing centralized authentication and authorization for network access.
Network security must always be the top goal for IT pros. In its most basic form, this means keeping unauthorized users off the network. Even the best firewalls and IPSes are useless if someone can just walk into the building and plug into an Ethernet port. And what about users sharing the Wi-Fi password outside of your organization?
Fear not—a technology called RADIUS can mitigate these security nightmares and more. Today, we'll explore what RADIUS is, what it can protect against, and how to set up your own RADIUS server. We'll also examine the pros and cons of RADIUS to help determine if it's right for your network.
What is RADIUS? Definition of RADIUS
RADIUS stands for Remote Authentication Dial-In User Service. It is a network protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for your users.
You might remember AAA from your Network+ exam, but if not, it is a framework for controlling and logging network access. RADIUS fits nicely into AAA by requiring users to authenticate with either credentials or a certificate before being granted network access. Picture RADIUS as a bouncer at a bar, checking IDs (credentials or certificates) before letting patrons into the bar (network).
How RADIUS Works
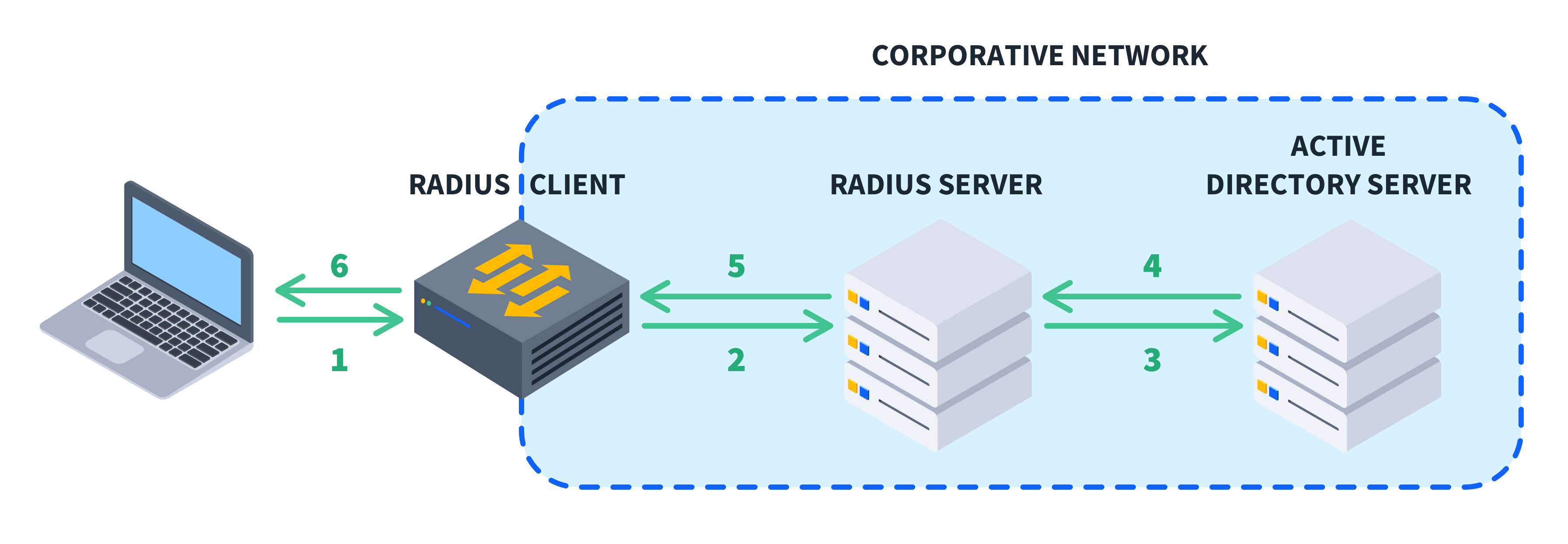
RADIUS requires two pieces to work: the client and the server. The RADIUS client (sometimes called a network access server, or NAS) is a network device, like a wireless access point or switch, that supports 802.1X (a protocol for network authentication).
The other piece, the RADIUS server, is an application running on a Linux or Windows server that receives the client's authentication requests and checks them against a user directory. That directory can be a database or a directory service like Active Directory or OpenLDAP.
Let's look at a real-world example. You connect your laptop to an ethernet port in an office where the network is set up to use RADIUS for network authentication. That port is connected to a switch set up as a RADIUS client to restrict network access.
The switch asks the laptop for credentials (username and password), which the user provides. The client then forwards the request to the RADIUS server, in this case, a Linux machine running FreeRADIUS (a widely used open-source RADIUS server). FreeRADIUS queries Active Directory, which verifies the credentials. FreeRADIUS replies to the switch to grant access, and your laptop can then access the network.
The same process can be used with different variables, like Wi-Fi access points or VPNs instead of switches, certificates instead of AD credentials, Windows Network Policy Server instead of FreeRADIUS, or Okta instead of Active Directory. Regardless of the implementation, the authentication process is the same.
Benefits of RADIUS
RADIUS is one of the more secure authentication methods, but there are several other benefits as well.
Improved Security Through Centralized Authentication
By limiting network access via a central point of authentication, you drastically lower the risk of unauthenticated access, enforce consistent and secure access control policies across the network, and reduce managing credentials to one source of truth that you probably already have in place (like Active Directory or Okta).
Physical access for ethernet connections is one thing, but take Wi-Fi, for example. Without RADIUS, Wi-Fi access to the private network would require a password shared with the entire staff. Do you trust everyone to never, ever share that password? Do you change the password every time someone leaves the organization? Either would be chaos; RADIUS brings order.
Scalability for Large Networks
As a robust protocol, RADIUS can scale to as many users and devices as you have. Since the RADIUS server only acts as a middleman between the client and the user directory, the load per user is minimal. When demand surges, most RADIUS server applications can be configured with redundancy and failover to handle the most demanding workloads. There are even cloud-based solutions. RADIUS is a solution that you just won't outgrow.
Support for Various Authentication Methods
We've mentioned credentials and certificates as common auth methods for RADIUS, but users can authenticate with a variety of other methods if the server supports them, such as hardware tokens or biometrics. Regardless of the method, multi-factor authentication, like a code texted to your phone, can be used for an extra layer of security.
Setting up a RADIUS Server
While installing and configuring a RADIUS server isn't complex, there is a lot of context to understand as you go. Instead of just listing commands to run, understanding this context and what the commands do is very important when implementing a new system, especially one that will control access to your entire network. We recommend starting your RADIUS journey in a test environment before implementing anything on your live network.
While there are lots of options, we also recommend starting with FreeRADIUS. It's open source, very well documented and maintained, and easy to get started. The makers of FreeRADIUS have a comprehensive tutorial for setting up your server; it's as good a place as any to begin.
Setting up a RADIUS Client
One important piece that the FreeRADIUS tutorial does not address is setting up your RADIUS client (remember that the client is the switch or Wi-Fi access point that sends your auth request to the server and acts as the gatekeeper until the server verifies your access).
Let's walk through a quick example configuration on a Cisco switch that should work with the configuration in the FreeRADIUS tutorial.
Enable AAA on the switch and set the RADIUS server IP and key.
Switch(config)# aaa new-model
Switch(config)# radius-server host 192.0.2.2 key testing123
2. Set AAA to use the RADIUS server and enable 802.1X authentication globally.
Switch(config)# aaa authentication dot1x default group radius
Switch(config)# dot1x system-auth-control
3. Enable 802.1X on a switch port.
Switch(config)# interface FastEthernet0/1
Switch(config-if)# switchport mode access
Switch(config-if)# authentication port-control auto
Switch(config-if)# dot1x pae authenticator
Switch(config-if)# end
Advantages and Disadvantages of RADIUS
Now that we've discussed RADIUS's shiny benefits and how to set it up, you might think things are ready to go. Not quite. While the benefits generally outweigh the disadvantages, there are a few things to remember.
Advantages of RADIUS
Enhanced Security: RADIUS strengthens your LAN security, hands down. It employs strong authentication to limit network access without adding much overhead. It also logs who gets on the network and when allowing admins to correlate users with suspicious activities and security incidents.
Centralized Management: RADIUS is managed from a central point: your RADIUS server. Policy enforcement is consistent and simple to apply, reducing the risk of misconfigurations across devices. Admins are also happy because RADIUS uses your existing user directory; there are no extra steps to onboard users or additional systems to manage.
Compatibility: RADIUS can be configured to authenticate via a variety of methods that suit your existing systems and security or regulatory requirements. Adding more stringent authentication makes systems requiring extra hardening trivial, meaning RADIUS is expandable to meet future growth.
Disadvantages of RADIUS
Complexity of Configuration: While RADIUS isn't complex overall, matching the configuration with your specific hardware and user directory can require some detective work. Careful research and documentation reading are key. We haven't mentioned yet the RADIUS server built into Windows, but setting it up is a real beast.
Single Point of Failure: Using a single RADIUS server to grant access to everyone on your network can be a huge liability if that server goes down. Therefore, setting up multiple servers in a failover configuration is essential to maintaining availability. FreeRADIUS and other solutions luckily allow for redundant failover servers. Test in your lab, and don't skip this crucial step!
Final Thoughts on RADIUS
RADIUS is a crucial tool for the security of your LAN, providing a robust means of controlling who can access the network. Centralizing that access control isn't a burden for admins to manage, and it scales easily for networks of any size. The setup can be tricky, but once you crack the code, your network will gain a new security superpower.
Want to learn more about network security? Consider our Network+ training course.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.