What is DHCP Snooping?

Quick Definition: DHCP snooping is an easy-to-implement security feature that protects your network from unauthorized devices acting as a DHCP server by blocking specific DHCP traffic from untrusted ports and limiting the rate of DHCP requests per device. The main purpose of DHCP snooping is to combat DHCP spoofing attacks.
Picture this: you’ve decided to get some studying done at a local library. It’s your first time visiting this location, so you’ll need to join their guest network, meaning your laptop needs a new IP address to be able to operate on this network.
You connect without issue, but notice your connectivity is a bit slow. You don’t think much of it at the time, and continue logging in to your email and checking social media. A few days later you notice you’ve been locked out of your social media accounts, and your email inbox is full of notifications about changes to your passwords and security questions.
What may have happened is someone at the library was connected to the same WiFi network as you, and used their device to act as a DHCP server. Your laptop connected to their device instead of the library’s DHCP server, which gave that malicious user the ability to intercept every network packet to and from your laptop while you were connected to what you thought was the library’s network.
This could have been prevented if the library had implemented a security feature called DHCP snooping.
What is DHCP Snooping?
DHCP snooping is a security feature that prevents DHCP spoofing, which we'll cover in a few minutes. Let’s briefly review how DHCP works before we get into the details of DHCP snooping.
When your device is connecting to a network, it starts a multistep process to communicate with a DHCP server and obtain an IP address.
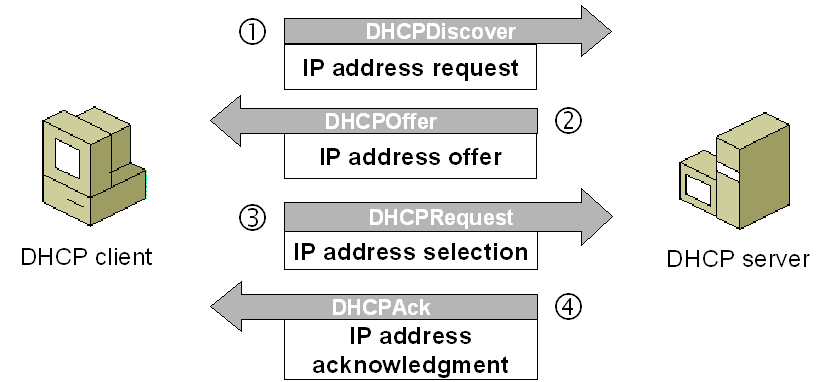
First, your device sends a DHCP Discover message, essentially saying “I’m new to the network and I would like an IP address if there’s one available”, to which a DHCP server will respond by broadcasting a DHCP Offer message to the local network “Here’s an available IP address”, including the requesting device’s MAC address.
The requesting device receives the DHCP Offer message and responds with a DHCP Request, which lets the DHCP server know the offered IP address has been accepted. Finally, the DHCP server sends a DHCPACK, which lets your device know it can now use that IP address, and that the transaction is complete.
Now that we understand how DHCP servers allocate IP addresses, we can discuss some potential methods attackers use, and how DHCP snooping helps prevent them:
None of the communication between the DHCP server and the requesting device is authenticated. If a rogue device on the network is claiming to be a DHCP server, there’s little a requesting device can do to verify such claims.
There’s always the possibility that the DHCP server runs out of available IP addresses. Referred to as DHCP starvation, a malicious user could make multiple DHCP requests within a short timeframe and exhaust all available IP addresses. This would allow the malicious user to portray their device as the true DHCP server.
Since none of the communication between DHCP server and requesting devices is unauthenticated, network administrators use DHCP snooping as a way to restrict which devices can transmit DHCP Offer and DHCPACK messages on the network.
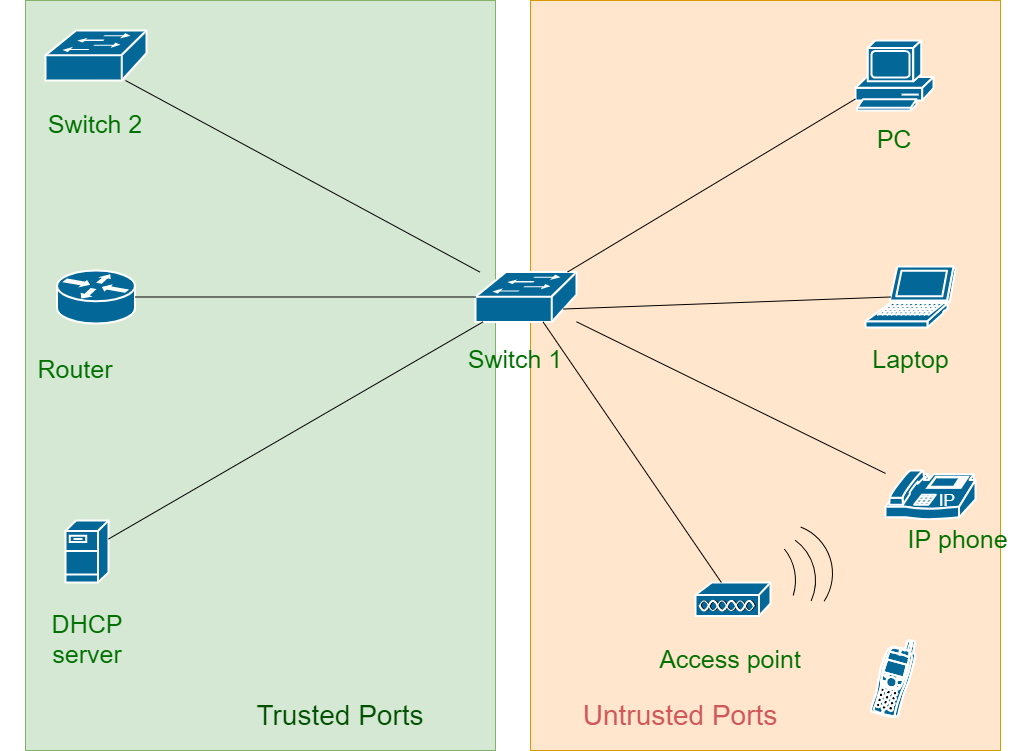
Cisco DHCP snooping allows for the configuration of trusted ports, which establishes which devices on the network are allowed to send DHCP Offer and DHCPACK messages, and all other ports are considered untrusted, and cannot transmit DHCP Offer and DHCPACK messages. Configuring trusted ports is a simple process which we will cover in the next section.
Cisco DHCP snooping can also prevent DHCP starvation attacks via rate limiting. Since DHCP starvation attacks rely on sending multiple DHCP request messages to consume all the available IP addresses within a given range, limiting the number of DHCP messages traversing untrusted ports within a set timeframe mitigates the likelihood of successful starvation.
DHCP Snooping vs. DHCP Spoofing
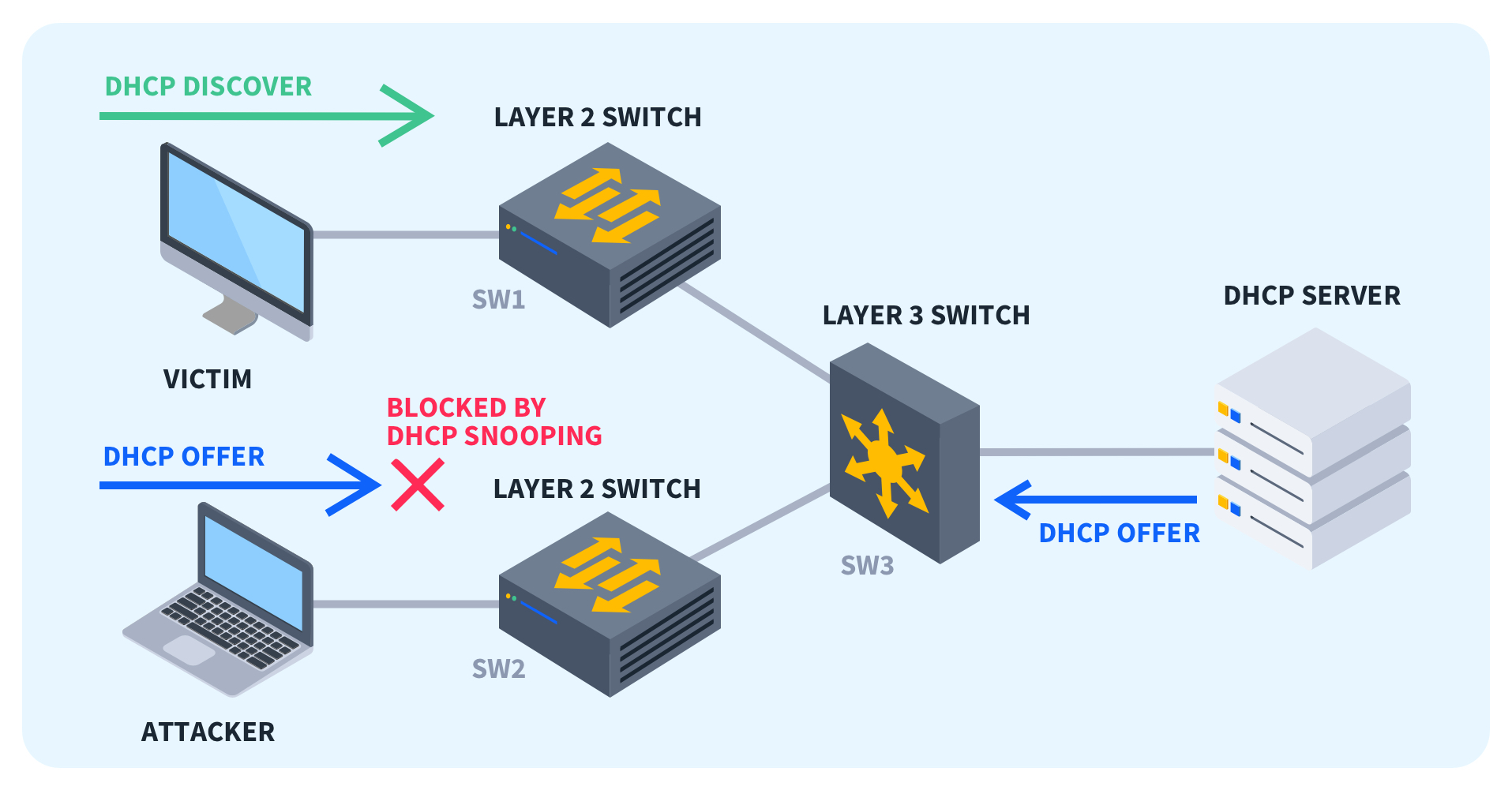
Remember that malicious user at the library? That person was using DHCP spoofing to intercept traffic, meaning that person had intentionally used their laptop to make it appear as though their malicious laptop was the DHCP server everyone else needed to connect to in order to obtain an IP address.
DHCP snooping combats this malicious behavior by monitoring the network for any untrusted device attempting to transmit DHCP traffic and blocking that traffic. The names sound similar, so if you’re having trouble telling the two apart try to remember spoofing is pretending, and snooping is monitoring.
Configuring Cisco DHCP Snooping
Basic DHCP snooping can be configured in just a few easy steps. First, you’ll need to log in to your switch, then enter configuration mode using the conf t command. Once you’re in configuration mode you'll need to enable DHCP snooping on the switch using the ip dhcp snooping command.
Then, specify which VLAN(s) to monitor with the ip dhcp snoop vlan 1 command, changing “1” to whatever VLAN number you need. Now, you’ll need to specify your trusted switch port by entering the specific port’s configuration mode with int g0/24 and then the ip dhcp snooping trust command. Finally, verify the configuration is working as expected with the show ip dhcp snooping command. Altogether, the process looks like this:
switch#conf t
switch(config)# ip dhcp snooping
switch(config)# ip dhcp snoop vlan 1
switch(config)# int g0/24
switch(config-if)# ip dhcp snooping trust
switch(config-if)# exit
switch(config)# exit
switch# show ip dhcp snooping
There are more advanced configurations, but this should be enough to get you started protecting your network from a malicious user trying to set up a rogue DHCP server.
DHCP Snooping Best Practices
DHCP snooping is not configured by default, so you will need to enable it manually, specify which specific VLANs to monitor, as well as designate trusted ports. All ports not specifically designated as trusted ports are considered untrusted by default, which means if you misconfigure DHCP snooping, you risk blocking legitimate DHCP traffic.
One recommendation is to specify rate limiting, which can be done using the command ip dhcp snooping limit rate <#>, where <#> would be the number of packets per second. This will help further reduce the risk of DHCP starvation attacks.
Another recommendation is to monitor your switch’s logs for messages related to untrusted ports and blocked DHCP traffic. It would be even better if you’re able to feed those logs into a Security Information and Event Management system (SIEM) to receive real-time alerts for any DHCP spoofing attempts.
One final recommendation is to download a current copy of your switch configuration file. It’s always a good idea to have a backup readily available for deployment, just in case something happens and you need to quickly restore your configuration from factory settings. This saves you from having to spend time manually configuring everything again and reduces the risk of deploying a misconfigured switch during disaster recovery efforts.
Troubleshooting DHCP Snooping
One of the most common issues you’ll run into when implementing DHCP snooping is your DHCP server not being able to assign IP addresses to requesting devices because no trusted ports were specified.
Remember, all ports are considered untrusted by default, so you need to specify which switch ports connect to your network’s DHCP server(s) when configuring DHCP snooping. This is a relatively easy fix since you can use the show ip dhcp snooping command to view the specifics of your DHCP snooping configuration.
Conclusion
DHCP snooping is an easily implemented security feature that can help protect your network and your users from DHCP spoofing attacks. By monitoring and blocking specific DHCP traffic from untrusted ports and setting rate limits for DHCP request messages, DHCP snooping works at layer 2 of the OSI model to ensure no other device on the network establishes itself as a rogue DHCP server.
Not a CBT Nuggets subscriber? Start learning today.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.