What is a CRC (Cyclic Redundancy Check)?

Quick Definition: Cyclic Redundancy Checks are an algorithm used to assign a unique value to data blocks, ensuring file integrity and verifying network transmission are complete.
When you receive a package in the mail, there are usually a few ways to determine whether the package has been tampered with. For example, the package might have tamper-evident tape along the seam. The package weight is also usually listed, which you can confirm upon receipt.
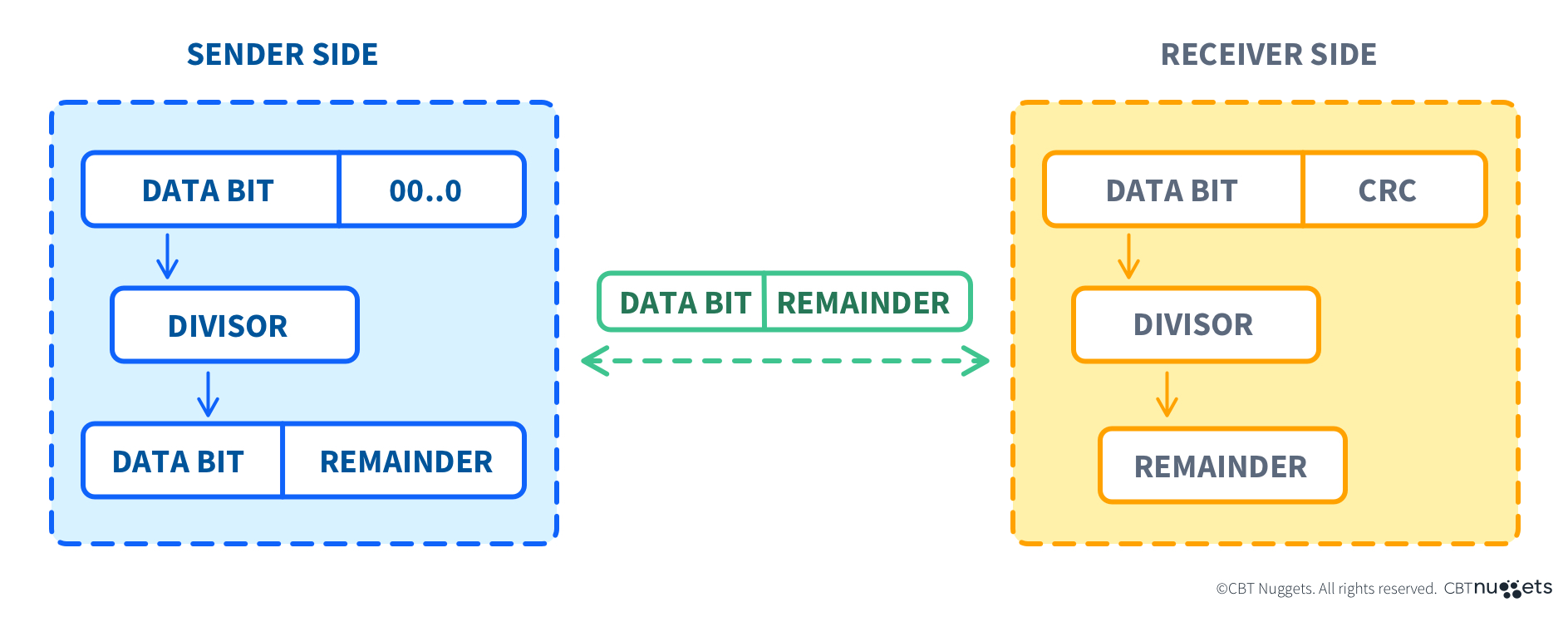
Data transmission uses similar checks to confirm whether the data you receive is the same data that was sent. A Cyclic Redundancy Check (CRC) is an error detection formula that relies on mathematics to calculate and compare what is called a checksum.
This checksum is the calculation's result and is appended to the original data so it’s all transmitted at the same time. It acts as a sort of virtual tamper-evident tape. If the checksums don’t match on the sending and receiving sides, it means something went wrong during transmission. A solid grasp of how CRCs function and their importance in network communications is valuable for anyone preparing for the CCNA and Network+. In the following section, we’ll delve into the details of CRCs.
What are Cyclic Redundancy Checks (CRCs)?
Cyclic Redundancy Checks are a validation method that uses mathematical formulas to create a value unique to the blocks of data being transmitted. This value, called a checksum, is added to the data during transmission as a reference for the recipient.
The recipient then calculates a checksum against their received data and confirms whether the two values match. If the two values match, the data is transmitted correctly. If the values don’t match, the data is not transmitted correctly.
Understanding CRC Algorithms
Cyclic Redundancy Checks, at their core, are mathematical computations. There are different Cyclic Redundancy Check algorithms, each with its advantages and disadvantages. The main types of Cyclic Redundancy Check algorithms we will discuss are CRC-8, CRC-16, and CRC-32.
One of the key concepts to understand about Cyclic Redundancy Check algorithms is the lower the algorithm, the higher the likelihood of a data collision. This means using CRC-8 will result in a higher percentage of data collisions over time than one might experience using CRC-16 or CRC-32.
Data collisions occur when two unique blocks of data generate the same checksum value. An oversimplified example would be if you were to assign a unique value to unique boxes. If you only used numbers 0-9, the eleventh box will have no choice but to match the value previously assigned to another box, even though the boxes are unique. If you increase your pool of values to between 0 and 99, you can assign 100 unique values before risking data collision.
Now, let’s complicate things. Instead of assigning values, you’re computing values by adding numbers together. Think of all the ways you can add numbers 0-9 to get to a value of 13.
Let’s again increase our possible values to 0-99. How many ways can we add numbers between 0 and 99 to achieve a value of 43? As you can imagine, the likelihood of a collision is drastically reduced when using a more complex algorithm and more values, but the concept remains the same.
Each algorithm involves some tradeoff between computational effort, speed, and collision risk. The CRC-8 algorithm calculates faster and uses less energy, but the risk of data collision for two unique blocks is much higher than the risk of collision when using the CRC-32 algorithm. The CRC-32 algorithm's complexity results in a slower computation utilizing more resources.
How CRCs are Used in Network Communication
Cyclic Redundancy Checks are used for more than just file integrity. It’s also used to detect network traffic errors. Cyclic Redundancy Checks append a checksum to data blocks at rest and in transit, which enables real-time network monitoring. These monitoring capabilities allow for faster error detection and response times amongst network analysts and engineers, which reduces the overall negative impact on the network.
By detecting errors, specifically discrepancies between the checksums of the data blocks sent and received, network and security analysts alike can detect both genuine network issues as well as potentially malicious activities. From a network perspective, checksum discrepancies can mean a network device is experiencing a bottleneck or is offline entirely.
From a security perspective, detecting mismatched checksums could mean network or file integrity has been compromised, meaning either traffic has been intercepted and modified or a file’s contents have been modified.
To try an example of a checksum, you can often download software from a reputable site and copy the checksum value to a separate note. Once the file has been downloaded, you can enter this command in your command line interface (CLI) or Terminal:
cksum <file_name>If you’re running the command in PowerShell, try this:
Get-FileHash <file_name>The exact algorithm used to calculate the hash value may be different from one of the CRC algorithms we’ve discussed, but the concept of integrity checks remains the same. The website you downloaded the software should tell you which algorithm was used to calculate the provided hash value.
What are Interface Statistics and CRC Errors?
Cyclic Redundancy Checks use checksums to detect variations in data being sent and received, so it makes sense that CRCs are mostly used to detect and repair network issues. Some common causes of CRC errors include electrical interference, faulty equipment such as cables and connectors, and hardware issues.
Electrical interference can be caused by other electronic devices of potentially greater signal strength broadcasting on the same frequency as the device experiencing data integrity issues, and in some cases can even be caused by wired devices with improper conduit and spacing from other wires.
Faulty cables and connectors are another common cause of CRC errors. When equipment is damaged, whether connector pins are bent or cables are frayed, it can result in data loss, which may result in checksum discrepancies and CRC errors. Hardware malfunctions, such as devices overheating or improper connections, such as a network card not being fully seated within a device, may also cause CRC errors.
Regardless of the cause of the issue, CRC errors lead to packet loss, performance degradation, and network downtime. Network analysts and engineers must monitor CRC error rates (the number of errored frames compared to the overall number of frames received) to detect issues within their networks.
Further, discovering patterns amongst those errors can help narrow the scope of the issue. Doing so helps determine the root cause of the errors and gives network engineers a chance to resolve the issue before its impact becomes greater.
Best Practices for Managing CRC Errors
The best way to manage Cyclic Redundancy Errors is through regular monitoring and analysis. This includes monitoring network packets and statistics, as well as physical equipment. Consistent monitoring increases the likelihood of early detection, which ultimately reduces any downtime the network may experience.
Deploying and maintaining failover network equipment can help respond to CRC errors while also mitigating network downtime and further packet loss. Logging and log forwarding should also be implemented to ensure network analysts can determine the root cause of the issues should the device go offline or become otherwise unreachable.
Regular maintenance of the equipment is also crucial to managing CRC errors before they start. CRC errors can often be traced back to issues with physical equipment, whether devices aren’t properly connected or equipment is damaged. Regularly conducting physical inspections is a good way to reduce the risk of CRC errors.
Conclusion
Cyclic Redundancy Checks, or CRCs, are a method developed to confirm that received data matches the data sent.
CRCs achieve this validation through the use of mathematical algorithms, and different algorithms exist to achieve the right balance of speed, resource utilization, and collision risk. Cyclic Redundancy Check errors can sometimes occur and are often the result of damaged or improperly connected hardware.
To learn more about network performance monitoring, check out our Cisco Network Management Troubleshooting training.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.