What is Cisco VRF (Virtual Routing and Forwarding)?

Quick Definition: Cisco Virtual Routing and Forwarding, known as Cisco VRF, gives routers a virtualization functionality that enables network engineers to create multiple routing tables using a single layer 3 device. This technology can improve security and optimize network performance, all while being easily configurable and relatively scalable.
Cisco Virtual Routing and Forwarding, commonly referred to as Cisco VRF, allows you to do more with less. Without Cisco VRF, your network engineer or network administrator would need to deploy and configure multiple routers to utilize multiple routing tables.
Cisco VRF provides the functionality for one router to utilize more than one routing table, similar to how Virtual Local Area Networks (VLANs) work. Cisco VRF allows for routing table interconnectivity where it's wanted and separation where it's needed. Let's explore how it works, how it differs from VLAN, and how to configure Cisco VRF.
What is Cisco VRF (Virtual Routing and Forwarding)?
Cisco VRF (Virtual Routing and Forwarding) is a technology that enables network engineers to create multiple routing tables using a single layer 3 device. This technology can improve security and optimize network performance, all while being easily configurable and relatively scalable.
In the past, network technicians had to configure multiple routers to use multiple routing tables, since each router typically only allowed for one routing table at a time. Cisco VRF introduced the ability to use multiple routing tables through the use of virtual routing and forwarding, which means less equipment to purchase and maintain while still reaping the benefits of multiple independent routing tables.
If you know anything about VLANs, you know the concept behind a VLAN is to create multiple virtual computers from one physical device. Virtual routing and forwarding works similarly by creating multiple routing tables from one device. The ability to create virtual routers offers many benefits, which we will cover in the next section of this article. First, though, let's discuss the differences between VLANs and VRF.
What is the Difference Between VLAN and VRF?
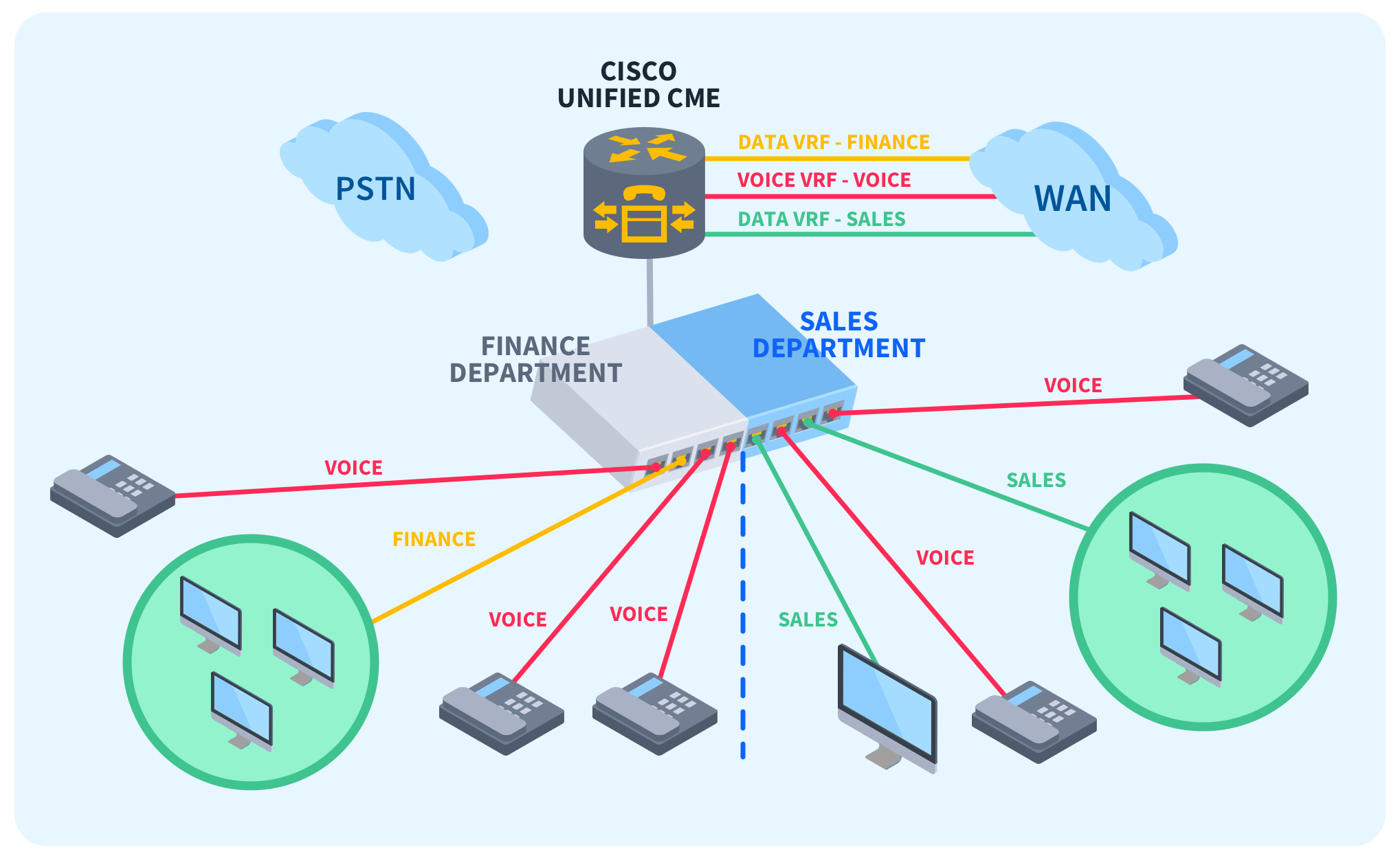
VLANs are mostly used for logical network segmentation. Let’s say you’re the network administrator for a small franchise of coffee shops. You might configure VLANs within each coffee shop to provide separate networks for guest wifi, point-of-sale systems, and any IoT devices or smart appliances within the shop.
This separation provides protection from things like malicious guests trying to attack point-of-sale systems or data from the point-of-sale systems being accidentally available to guests using the guest wifi.
Virtual routing and forwarding could be used to restrict each coffee shop from communicating with one another while still being able to communicate with a single centralized server, such as an instance of cloud storage.
This cloud server might be a corporate server used to store sales and inventory information that the corporation wouldn’t want accessible to each franchise. The VRF would act as a VPN (virtual private network) between your shop locations and the cloud storage.
A common question people ask about Cisco VRF is whether it is layer 2 or layer 3 of the OSI model. It is layer 3 of the OSI model because layer 3 is responsible for transmitting data between two different networks, whereas layer 2 is responsible for transmitting data between two devices on the same network.
Remember, layer 3 (the network layer) is used to ship data packets to different networks, similar to how you might use the postal service to deliver a letter across the country. Layer 2 (the data link layer) is used to transmit data packets within the same network, similar to how a postal worker places letters into the correct mailbox in an apartment building.
Cisco VRF Benefits
Cisco VRF offers many benefits, including security, segmentation, and enhanced performance. Virtual routing and forwarding are also relatively easy to set up, which we'll cover in the next section. The major benefit of using Cisco VRF is the security it provides.
When setting up Cisco VRF, you get to specify which networks can communicate with each other by configuring them to do so, and simply not configure any networks you don’t want communicating with each other. It's similar to how access control lists (ACL) work, with the key difference being that with VRF, the network is completely unaware of any subnets not explicitly listed in the routing table. It’s the difference between an ACL knowing not to route traffic from specific sources and VRF never knowing specific sources ever existed.
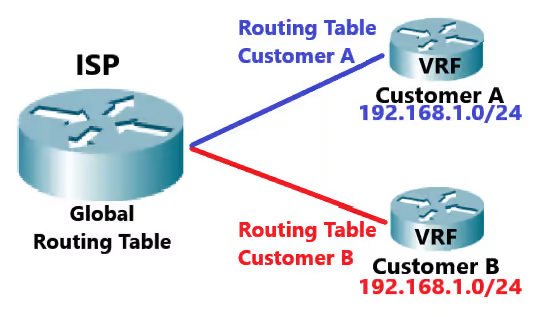
Another benefit to Cisco VRF is network segmentation. Remember our coffee shop example from earlier? Let’s look at an example on a larger scale. Remember that cloud server each franchise was able to communicate with while not being able to access information from other franchise locations?
What other instances might we want specific networks to be able to communicate with the centralized device while not being able to communicate with each other? Cloud service providers (companies like AWS or Microsoft Azure) also want their customers to be able to access servers while not being able to access networks belonging to other customers.
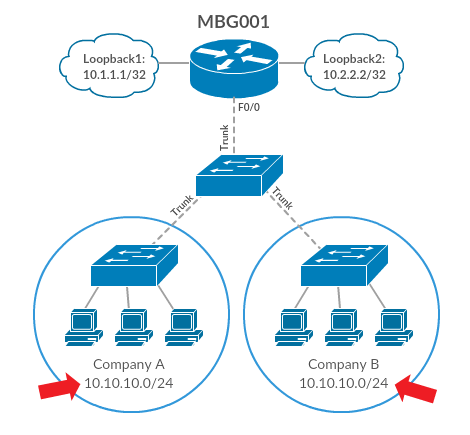
The final benefit is network optimization. There are only 253 usable IP addresses in a single /24 subnet, which makes IP addresses somewhat of a scarce resource. Through the use of Cisco VRF, multiple networks can use the same IP addresses without issues. The reuse of IP addresses greatly increases the number of devices a service provider can support.
Virtual routing and forwarding can also be configured to allow different subnets to have more optimal paths, which could be used by service providers to separate users based on pricing or subscription tier. The ability to manipulate network speeds and the ability to reuse IP addresses greatly increases the number of devices and quality of service a network can support.
How to Configure Cisco VRF
The exact method and commands you use to configure virtual routing and forwarding will depend on the version of the Cisco switch you are using. You may be able to use a graphical interface, but we’ll focus on using the command line interface. First, you’ll need to enter configuration mode using the conf t command.
Once you’re in configuration mode, you need to create a new VRF and give it a name using the command vrf definition VRF_Name where “VRF_Name” is replaced with whatever name you choose.
Then, You will specify whether this VRF will be using IPv4 or IPv6 using the address-family ipv4 command. As you set up the VRF and address family, you will automatically navigate into that deeper level of configuration mode, so you’ll need to use the exit command twice to get back to generic configuration mode before continuing.
Once you’re back to the top-level configuration mode, specify an interface using the interface gigabitEtherenet #/# command, then use the vrf forwarding VRF_Name command to correlate an interface with the newly created VRF.
Note that you’ll want to replace “#/#” with whatever interface you want to use. Finally, you’ll need to configure the IPv4 address for the interface, and you can do this by entering the ip address 123.123.123.123 255.255.255.0 command, where you replace those arbitrary numbers with whatever IP you want.
It might seem daunting at first, but the whole thing should look like this:
conf t
(config)#vrf definition VRF_Name (config-vrf)#address-family ipv4 (config-vrf-af)#exit (config-vrf)#exit (config)#interface gigbitEthernet #/# (config-if)#vrf forwarding VRF-Name (config-if)#ip address 23.123.123.123 255.255.255.0 (config-if)#end
You will use the same set of commands when creating any additional VRFs you may need. You should now be able to view the routing table using the ip route vrf VRF_Name command.
Cisco VRF Best Practices
While Cisco VRF is relatively easy to implement, it may not be necessary, depending on the needs of your network. Before deciding whether to utilize virtual routing and forwarding in your environment, consider the size and function of your environment. If your network consists of only a handful of users, no guests, and no outside users connecting to your servers, VRF may be unnecessary.
If you decide Cisco VRF would benefit your network, take some time to plan how you want to separate your existing network. Additionally, plan with scalability in mind as your network may grow over time, so your routing tables may need to be updated as your network evolves.
Conclusion
Cisco Virtual Routing and Forwarding is an easily configurable technology that allows network administrators and network engineers to establish multiple routing tables through one device, similar to how VLANs allow for the configuration of multiple networks through a single switch.
The use of multiple routing tables provides the ability to segment networks with or without the use of firewalls or access control lists and can act as a virtual private network. Some common uses for Cisco VRF include Internet service providers (ISPs) and cloud services providers.
Advance your career with Cisco training from CBT Nuggets.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.