What is BPDU Guard?
Quick Definition: Cisco BPDU guard is a security feature that protects the main network infrastructure, like switches and routers, from malicious user devices. Most effective when implemented on edge devices, BPDU guard blocks BPDUs from being transmitted past the receiving device. This helps ensure that only authorized devices can act as switches and routers, reducing the likelihood of rogue devices compromising the network.
If you know anything about technology, specifically networks, you know safeguards are available to mitigate the risk of being attacked. One of those safeguards is BPDU Guard, or bridge protocol data unit guard. BPDU Guard is a feature specifically designed to stop attackers from disrupting your spanning tree network configuration. Specifically, BPDU Guard helps a spanning tree root bridge maintain its status as the root bridge. We’ll discuss that in greater detail in just a bit.
By the end of this article, you should expect to have an understanding of what Bridge Protocol Data Units are, as well as what BPDU Guard does, and why it’s important to network security.
You should also have a better understanding of the spanning tree protocol, which is a large part of why BPDU Guard exists. Additionally, you'll learn the basics of configuring and troubleshooting BPDU Guard, as well as receive some recommendations for furthering your understanding of BPDU Guard.
What is BPDU Guard?
Cisco BPDU guard is a security feature that protects the main network infrastructure from malicious user devices by blocking BPDUs from being transmitted past the receiving device. This ensures that only authorized devices can act as switches and routers.
Before we dive too deep into BPDU Guard, let’s discuss the environment in which someone like a network engineer or network admin would use this. Spanning Tree Protocol (STP) is a network topology that prevents loops and allows for redundancy by establishing a “root” switch. This root switch, or root bridge, is what prevents loops.
The root switch sends messages from one device to the next, and once the message gets back to the root switch it knows to terminate the communication with the understanding every device in the tree has received it. The root bridge is the key to preventing messages from being transmitted in an endless loop.
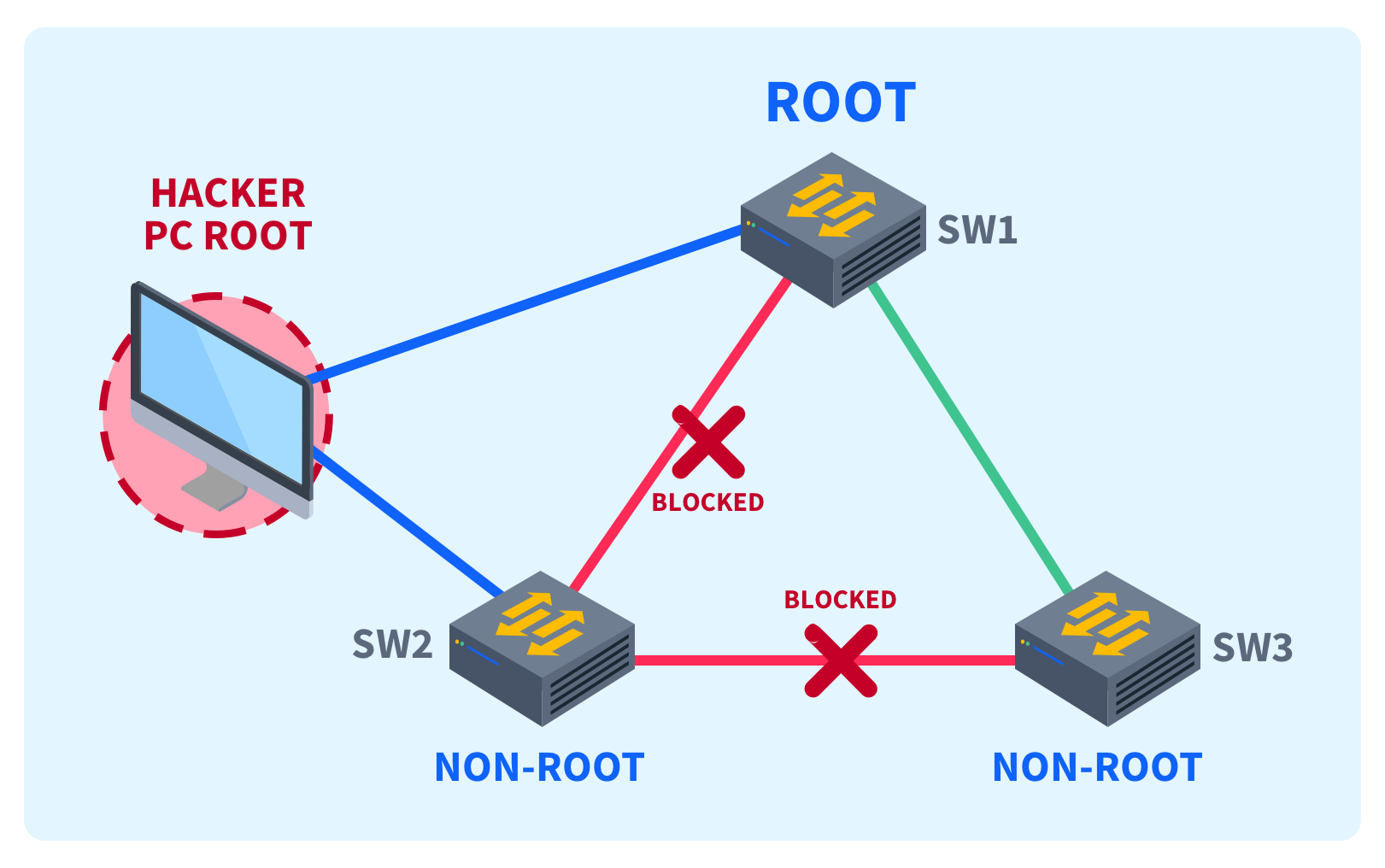
A root bridge becomes a root bridge by having the lowest bridge ID (BID), which consists of IP address and MAC address, and is usually designated as such by network engineers based on its performance and location. Attackers will often attempt to designate one of their own malicious devices as the root bridge by assigning their device a lower BID and sending BPDUs to other devices in the spanning tree.
There is a security feature separate from BPDU guard called spanning tree root guard, which works by rejecting all “superior” BPDUs, which are BPDUs with lower BIDs, from any device other than the known root bridge.
If a device other than the root bridge attempts to send superior BPDUs to any device with STP root guard enabled, the receiving port will enter a root-inconsistent state for as long as superior BPDUs are being received. This means no traffic will transmit through that port for the duration of the transmission. Although the two features are similar, BPDU guard works slightly differently.
How Does BPDU Guard Work?
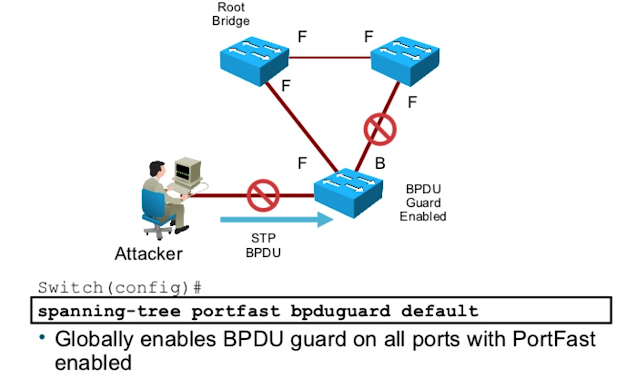
While this article is specifically about BPDU Guard, it is important to mention BPDU Guard often works in tandem with the spanning tree root guard. Both of these security features exist to protect the root bridge’s status as the root bridge, and to prevent unauthorized devices from attempting to use a lower BID as a way to conduct malicious network activities.
BPDU Guard must be activated on any ports that should not receive bridge protocol data units from any devices, which typically means ports directly accessible by end-user devices like mobile phones, laptops, and other devices not typically used as a network switch or routers.

Once configured, BPDU Guard acts like a security guard, keeping people outside of a building by holding the door shut, only in this case, the people are BPDUs from unauthorized devices, and the building is the spanning tree topology. BPDU Guard achieves this by disabling any port receiving BPDUs from an unauthorized device, changing its status to err-disabled.
The main difference between STP root guard and BPDU guard is the type of traffic they listen for and how they react. STP root guard listens for superior BPDUs and temporarily disables the port(s) receiving superior BPDUs, where BPDU guard completely disables the port when any unauthorized device begins transmitting BPDUs. This will require a network administrator or engineer to manually reenable the disabled port.
How to Configure BPDU Guard
BPDU guard needs to be configured on every port you do not want receiving BPDUs, and thankfully Cisco BPDU guard can be configured globally, saving you the trouble of having to configure one port at a time.
You should always verify the commands specific to the switch you are configuring, but the setup should look something like this:
Switch# conf t
Switch(config)# spanning-tree portfast bpduguard default
Switch(config)# show spanning-tree bpduguard info
Once you’ve logged in to your switch, the first command sets you in configuration mode. The second command enables BPDU guard globally, saving you the time and effort of having to enable each port individually. Finally, the last command is to confirm BPDU guard is properly enabled.
The process is similar if you need to enable or disable BPDU guard on specific ports. It looks something like this:
Switch# conf t
Switch(config)# interface 1/1
Switch(config-if)# spanning-tree bpduguard enable
Switch(config)# exit
Switch(config)# show spanning-tree bpduguard info
Here, the interface 1/1 command enters into the specific interface on which you want to enable BPDU guard, and you’ll want to swap “1/1” with the numbers of the interface you’re configuring.
How to Troubleshoot BPDU Guard
The most common issue you will experience when working with BPDU guard is disabled ports. You may notice a lack of traffic on your network, and you may be right to assume BPDU guard has something to do with it. Luckily, determining which ports are disabled and why is a simple task.
To discover which ports are disabled, you can use the following command:
show interfaces status err-disabled
To determine why a port is in err-disabled status, use this command:
What are Some Best Practices for Using BPDU Guard?
BPDU guard is an easy-to-implement security feature to protect your network from rogue devices attempting to compromise your network. Specifically, BPDU guard should be configured on user-facing devices on your network, where BPDUs usually aren’t being transmitted.
Another best practice is remembering that BPDU guard is only one tool in your network security arsenal. BPDU guard should be used in conjunction with other tools like DHCP snooping, spanning tree root guard, and BPDU filter, to name a few.
Conclusion
BPDU guard is a security feature that network administrators and network engineers alike can use to prevent rogue devices from compromising their network. BPDU guard works by disabling ports when BPDUs are transmitted, and is most effective when implemented on user-facing network devices.
In addition to being easy to configure, it’s also easy to troubleshoot, as Cisco BPDU guard explicitly states when it is the reason for a port being disabled. BPDU guard is a great addition when securing your spanning tree network.
Not a CBT Nuggets subscriber? Sign up today.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.