What is 802.1X?

Quick Definition: 802.1X is a port-based authentication standard, key to AAA. It’s closely linked to EAP. 802.11x functionally does not exist but is a misnomer that is commonly parroted.
First: 802.1X vs. 802.11x: What's the Difference?
The two terms above are very commonly confused, but aren’t the same. As a matter of fact, the capitalization and use of the two cause both conflict and confusion more often than one might think.
Here, we'll explain the differences between the two and make sure that you understand what’s common, correct, and valuable between them.
What is 802.1X? Why This Format?
802.1X (a key area in your Net+ Test) is an IEEE standard. Anytime you see a number starting with 802, it’s a safe bet that it belongs to the IEEE 802 group, which is responsible for networking standards, particularly for LANs, MANs, and PANs.
WLANs also fall under this umbrella as a subtype of LANs. Under PANs, you’ll find technologies like Zigbee, which supports small networks with short ranges. Bluetooth and BLE were once categorized here but have since moved to the Bluetooth SIG (Special Interest Group) as they expanded.
Now, 802.1 specifically focuses on network management and security. Understanding IEEE standards means knowing how they’re indexed:
Capital letters indicate full standards.
Lowercase letters indicate amendments.
So, 802.1X is:
Related to LANs, MANs, and PANs
Focused on security and management
A full standard, not just an amendment
To clarify, 802.1X covers a Port-based NAC, or Network-Access-Control. Put more simply, it controls the way data moves or does not move through the network. It does this by establishing a “Controlled Port” and an “uncontrolled port.”
Think of the uncontrolled port as the vision slot in a seedy club’s door—it’s where you’re asked who you are, and you respond with your name and passphrase, sometimes literally. The controlled port is the door itself—if you’re allowed, it transmits your traffic.
This forms the basis for almost every authentication that you will see in an enterprise environment above a simple password, especially in WLANs. This can even happen behind the scenes, but more on that later.
What is 802.11x and How is it Different?
Usually, this is a misunderstanding. 802.11x is a placeholder for an amendment that was never ratified. It’s often confused with the above, generally by beginners in the early stages of their wireless education.
Building on what we established above, it WOULD:
Have to do with LANs, PANs, or WLANs or MANs
Have to do specifically with wireless or WLANS (.11 is WLAN-specific)
Be an amendment to the 802.11 standard, commonly called Wi-Fi. (Remember, Capital is a standard, and lowercase is an amendment.
Fortunately for us all, and in part to avoid confusion, it’s not an amendment in active use. (If you’re curious about the ones that are in active use, we provide a lot more detail in our CBT Nuggets' Wireless Network Administrator training.)
Why is 802.1X or EAP Important?
802.1X, or the EAP (Extensible Authentication Protocol, or on the wire EAPoL, simply adding “Over LAN.” Yes, it’s adding an initialism in another one. They’re bad about that) is interesting due to both the prevalence of its use and the flexibility of the structure.
It’s less a “thing” and more of a suite of things, much like most of the cipher suites in use. (Out of our scope, you can find an excellent explanation in our Wireless Security Professional training.) Attacking the latter first, EAP can use… Well, Just about any type you want if you configure it correctly and have the requisite backend. A short list includes:
MD5: Don’t use this. The encryption is deprecated like WEP.
TLS: Stands for “Transport Level Security." It's seen a LOT in browsers and tunnels.
TTLS: Tunneled TLS. Note it’s not Transport layer security, but that’s splitting hairs.
PEAP: Very common. Protected EAP. Superficially similar to TLS, very common on WLANs.
FAST (Or EAP-FAST): Originally used and created by Cisco. Support can be spotty.
LEAP: Semi-deprecated; originally WLAN-native before being licensed by Cisco.
That’s only a partial list, but it’s a lot. When you need to decide what to use and what not to use, your choice will generally depend on your architecture, how many certificates you want to set up, and what your client base will support.
Some can be used with just a username and password, for example. This makes them suitable for BYOD with less hassle. If you need to use certificates, generally, you want an MDM situation, but it’s more secure. Interestingly, TLS is widely used because of the ability of browsers to store and query certificates. Still, it’s not being used in that case for device authentication but rather for making sure that the server itself is who it says it is.
How 802.1X Works to Authenticate
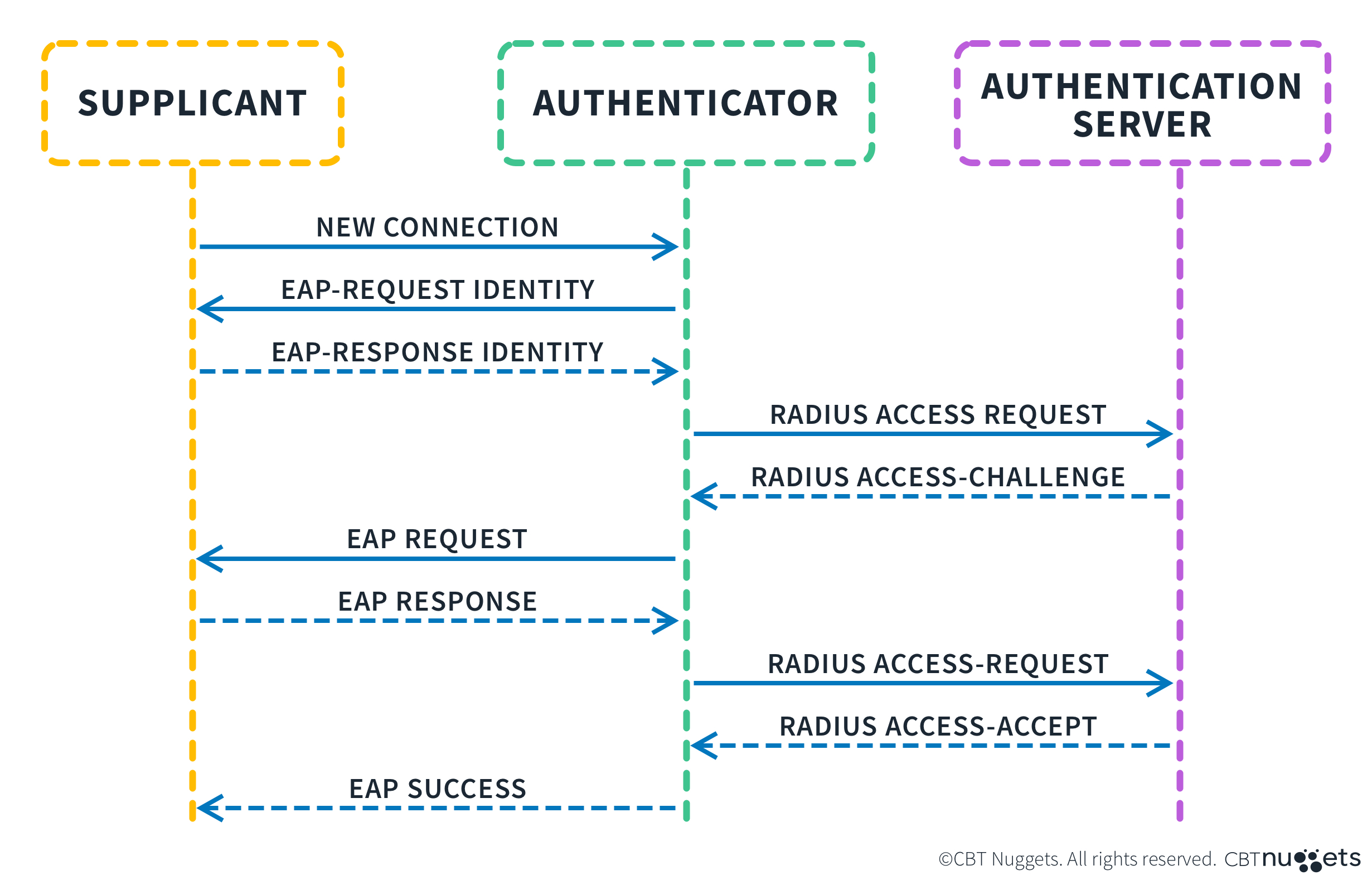
Keeping it high level, EAP is a conversation between three entities or computers over the network:
The Supplicant: Generally your client device, or more precisely, the part of your device that handles security, encryption, and access. It’s a subprocess in your drivers most of the time.
The Authenticator: This is the device doing the checking itself, the gatekeeper. Can be a WLAN controller, for example.
The Authentication Server: A RADIUS server, or central identity store. This is the thing that “knows” who is allowed. This and the Authenticator can be combined in some cases and significantly smaller networks. Ruckus and Aruba have internal Radius Servers in the WLAN Controllers.
The process goes like this:
A new connection is made to the network. Uncontrolled port is used for the following:
The Authenticator (Auth) requests the Supplicant’s (Sup) Identity. Usually the format will be agreed upon previously by whatever PHY and MAC protocol is in use.
Sup sends Auth the ID.
Auth sends the received ID to the Authentication Server (AS), as a RADIUS access-request.
AS sends Auth the Access-Challenge, which serves to establish ID.
Auth forwards the Challenge to Sup, in the form of a EAP request
Sup sends Auth the EAP response, responding to the “Access Challenge” (5)
Auth forwards as a new Access-request to the AS.
AS responds positively or negatively depending on the data, to the Auth.
Success or failure is forwarded to Sup.
Access is (hopefully) granted to the Sup device, and the controlled port opens.
Final Thoughts
EAP can be a bit tricky, but simplifying it makes troubleshooting easier. By isolating EAP traffic in Wireshark, you can quickly spot issues and better understand the process.
Now, you're equipped to discuss the key differences confidently and explain them clearly. There’s MUCH more to learn about it, but this covers most of what you need to get to your Network+
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.