What are Protocol Packets and Byte Counts?

Quick Definition: Protocol packets and byte counts refer to the number of data packets and the total amount of data (measured in bytes) transmitted or received by a specific network protocol. These metrics help analyze the traffic and performance of different network protocols.
Imagine you and a few friends are driving from one place to another. However, you won't all fit in one vehicle, so you take separate cars. While you all might try to take the same route, it’s more likely that at least one car uses a different lane, and another car may take a different road. In the end, you all arrive at the same destination around the same time, though.
This is similar to how network packets work. Network packets can often be referred to by different names such as packets, protocol packets, or IP packets, but they all represent the same thing, which is a unit of data sent from and received by computers.
Going back to our group adventure, your group knows how many people are involved, how many vehicles are needed for this outing, and how many people are in each vehicle. Similarly, protocol packets break down large chunks of data into smaller, more easily transported chunks of data. These packets also know how many are involved and how much data is in each packet, and they even arrange the packets in the same order they were sent upon arriving at their destination.
Understanding protocol packets and byte counts is especially important for CCNA and Network+ exam takers. In this article, we'll discuss how this all works, how you can monitor network packets, and the different types of protocols via which packets are transmitted.
What are Interface Statistics?
Interface statistics is the data collected about the performance and activity of a network interface, including the amount of data sent and received, error rates, and the status of the connection. These metrics help monitor and troubleshoot network performance.
Continuing with our example of a group car ride, imagine if one of the vehicles got stuck in traffic, ran out of gas, or experienced some other obstacle that causes them to either not make it to the event or arrive late. All of these obstacles can be communicated in a group chat, providing some form of metrics and expectations for standard travel time.
Similarly, computers create and store metrics about the travel times and paths of network packets. Network analysts and engineers use this information to identify network latency, packet loss, and other issues, such as loopback errors.
What are Protocol Packet Counts?
Protocol packets are how computers transmit data across a network. Each packet can be broken down into three main sections: header, payload, and footer. (Also called a trailer.)
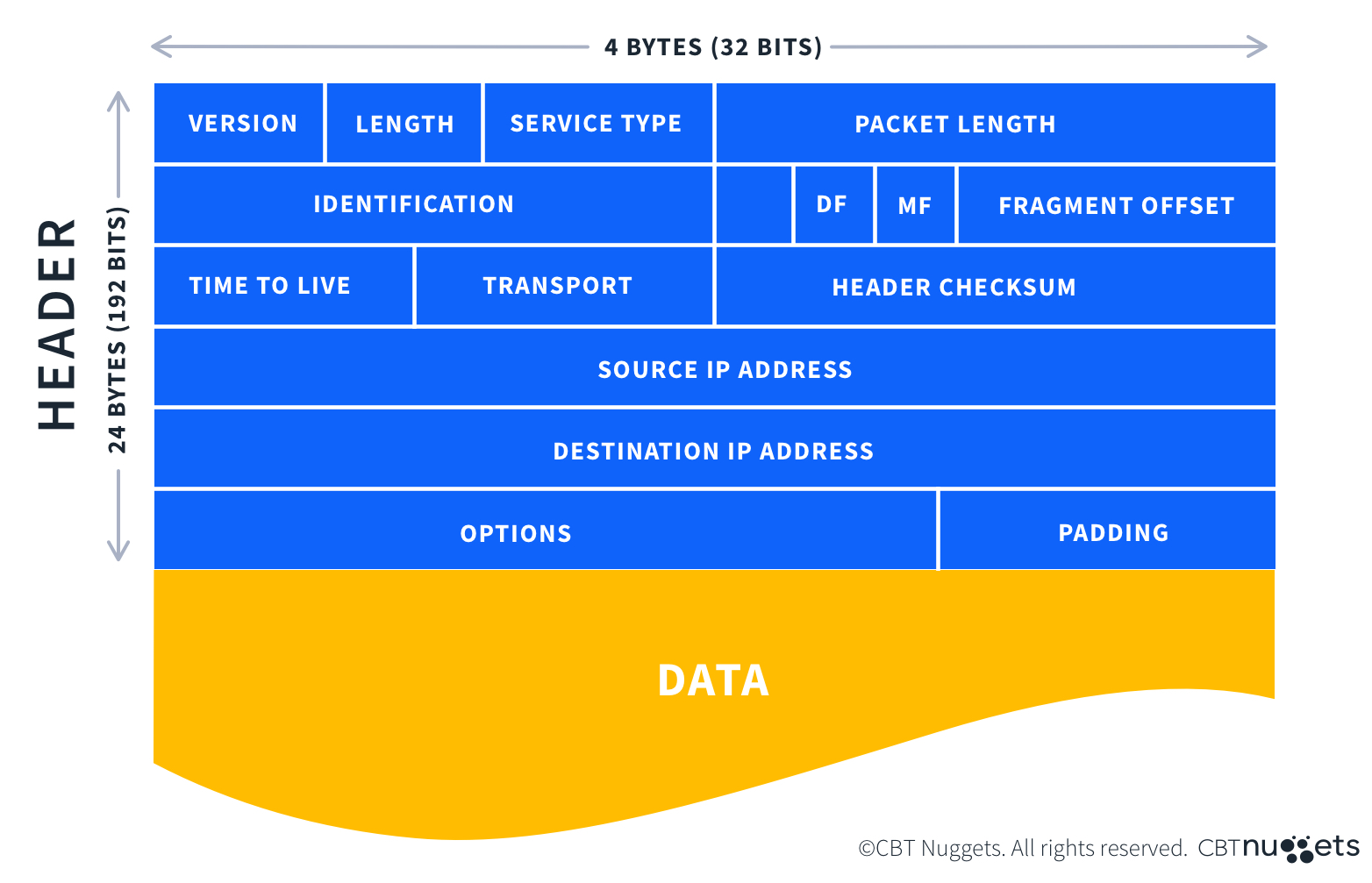
Header
The header contains information about the data being sent, such as sending and receiving IP addresses, the length of the packet, the protocol via which the packet is being sent, and the sequential number of that specific packet (ex., 1 of 5 or 3 of 4).
Payload
The payload is the information being transmitted. When your friend sends you a message, the payload is the message itself, the stuff we all care about. Depending on the size of the information being sent, the payload may be padded with additional, blank data to fit the overall packet size correctly. Think of this blank data as virtual packing peanuts so the message fits snugly inside the rest of the packet.
Footer / Trailer
The footer specifies the end of the packet and can contain some form of error checking, such as a checksum value. Think of the footer of the packet like the “over” message people say when using walkie-talkies.
All of the extra information included in the header and footer provides valuable insight into a network’s health. Network analysts can use this information to determine if there’s an issue with the network and then begin to find the issue’s origin. For example, if you receive packets 1, 2, 3, 5, and 6 of 6, you know somewhere along the way packet number 4 was lost. Likewise, if any of the checksum values provided by the footer don’t match the checksum values of the received packets, that’s a good indication something happened to the packets along the way.
Although there are several networking protocols, we will discuss three related to protocol packets: TCP (Transmission Control Protocol), UDP (User Datagram Protocol), and ICMP (Internet Control Message Protocol), all of which have unique characteristics.
TCP
The TCP protocol is the most common protocol related to network packets. This is what’s referred to as a reliable transport system because of the various checks and confirmations that packets are being both sent and received. Think of TCP as mailing a letter through certified mail with tracking. You know where it is and when it’s received, and if something happens to it in transit, you can track the issue back to a relative location.
UDP
Opposite of TCP is UDP, which is considered unreliable transport. If TCP is similar to mailing a letter via certified mail, UDP is similar to putting a letter in your mailbox and hoping the post office takes care of the rest. You have no way of confirming the packets arrive at their intended destination, and tracking isn’t nearly as extensive as with TCP.
With that said, UDP packets are used almost every day, and most people never notice transmission issues – I’m specifically talking about video output. If you watch movies and shows on a TV or if you binge short-form content on your favorite social media app, you’re receiving UDP packets. The next time you’re on a video call for work or to speak with friends, just know you’re using UDP packets there, too.
ICMP
ICMP protocol is specifically used for error reporting and monitoring. Let’s say your computer sends a packet to another computer, and for some reason, it’s too large to receive. Well, the recipient will return an ICMP packet to your computer stating so. You may be more familiar with using ICMP packets if you’ve ever used the “ping” command.
What are Byte Counts?
A byte refers to the most common unit of measurement used for data. Monitoring byte count in network traffic analysis helps provide an understanding of how much data is flowing, both internally and externally, and how quickly.
Monitoring data transfer sizes and rates over a period of time can establish a baseline of what you might consider normal traffic for your network. Comparing traffic to that baseline can help detect anomalies such as network bottlenecks and equipment failures. For example, an increase in packet sizes can result in slower transfer rates.
Tools and Techniques for Monitoring Packets and Byte Counts
There are several tools available for monitoring components of network traffic, both free and paid, some with a graphical user interface (GUI) and some without. Some tools are native to operating systems via the Command Line Interface (CLI), such as Ping, Traceroute, and Tcpdump. Other tools may require an additional download, such as Wireshark and Nmap.
Each of these tools provides varying degrees of information about network connections and traffic between a source and destination, all of which can be used either separately or together to provide a holistic view of your network and any issues it may be experiencing. These tools are fantastic resources for troubleshooting, and should be used regularly to identify anomalies within your network.
Conclusion
For networking professionals, keeping an eye on network packets, byte counts, and protocols is vital to ensuring your network runs smoothly. Understanding how packets work and the different ways they’re transferred gives you valuable insight into the overall health of your network. If you're gearing up for CCNA or Network+ (N10-009) certification, these concepts are especially important—they’re not just part of the test, but crucial tools that will help you in your everyday work.
To learn more about networking, see what Networking Certification Training CBT Nuggets has to offer!
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.