What is the System Life Cycle?

Quick Definition: The System Life Cycle is a structured method for managing IT investments from their initial idea through development to retirement. Its goal is to create and deliver systems that meet or exceed stakeholder expectations both in business and financial terms.
The typical enterprise operates with a mix of network, hardware, cloud, and software technologies. IT execs must manage the life cycle of these technologies – from provisioning new applications, maintaining and operating them, to phasing-out and replacing them as they reach the end of their useful life.
As businesses and technology change, everything in the IT infrastructure has a life cycle; even data stored in the cloud can reach the end of its useful life.
This post discusses the system life cycle and its component system life cycle development phases. It will also discuss why system and network technical professionals need to be familiar with the system life cycle and how it is addressed in the CompTIA Network+ certification program.
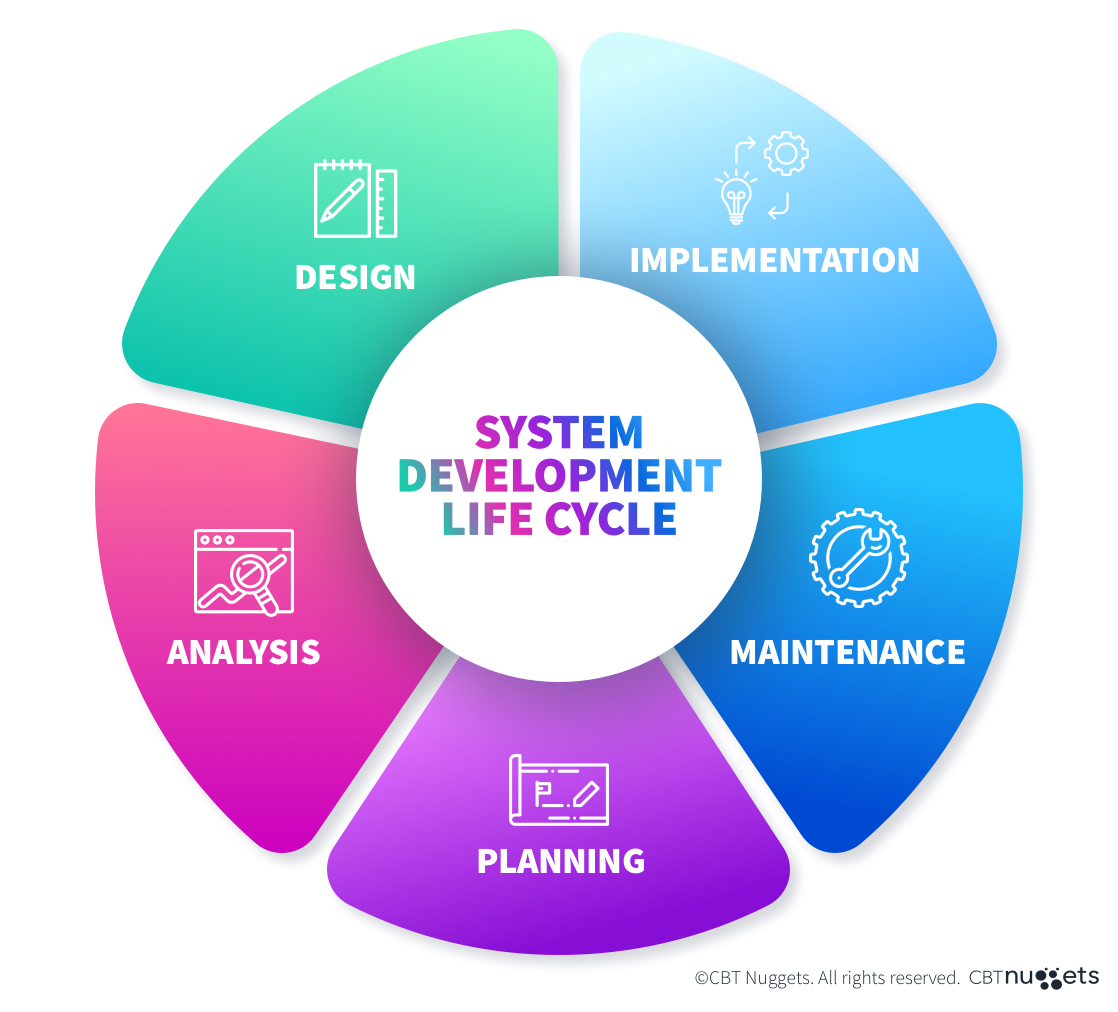
Phases of System Life Cycle Management
The system development life cycle comprises a number of stages, beginning with planning, then moving on to development and implementation, to live operation and maintenance, all the way to final decommissioning and removal from service.
Phase 1: Planning
The Planning Phase of the system development life cycle begins when management identifies a business or technical infrastructure need. This could be a new or upgraded application or technology. The first step is to scope out the potential project – outlining the proposed project and preliminary business case, setting out planning assumptions, identifying key risks and constraints, as well as any alternative approaches.
Typically, a feasibility study is performed to validate whether the proposed solution can be built and whether it can deliver the expected results. Existing processes and systems are reviewed, and stakeholders are interviewed to determine the impact of the proposed project.
Output from the Planning Phase is a proposed project plan with high-level user requirements, a project scope, risk/benefit analysis, projected timelines, and budget and resource requirements.
Executive and stakeholder management then makes the necessary Go/No Go decision.
Phase 2: Development
Next, the project team begins working on a detailed architecture and design for the project. The high-level user requirements from the Planning Phase become more detailed. If business processes are being reengineered, detailed data flows, and process model inputs and outputs are defined.
The overall system architecture is designed including individual components, user interfaces, transaction layouts, and database structures. If the new system is replacing an existing one, a migration plan is developed. The testing process and acceptance criteria for expected operation must be developed for stakeholder approval.
Test databases are set up by database administrators, while systems and network administrators set up the development and test environment systems and networks. Actual development starts with programmers writing the code to deliver the required functionality. They test the individual modules and then the complete system to ensure it performs according to specifications.
The final part of the Development Phase comes with user acceptance testing, as stakeholders perform quality assurance on the completed system or upgrade, validating that it performs as expected.
Phase 3: Implementation
Once the project has been fully tested – and accepted by user stakeholders – the Implementation Phase begins. The project manager must select the appropriate deployment strategy. There are a number of strategies, each with their own benefits and risks.
The simplest approach – but perhaps riskiest – is to simply switch off the old system and flash-cut the new one. In the “Ramped” or rolling-update approach, the new version is slowly introduced to replace the old version. A third approach – called “Blue/Green” – is where the new system is introduced in parallel with the old version and traffic is gradually switched over to the new version.
A more conservative approach is “Canary” rollout, where the new version is validated by a subset of users, prior to full roll-out. A similar approach is “A/B Testing” which is a controlled release of the new functionality to specific users for validation prior to full release.
A final and most conservative deployment strategy is “Shadow” roll-out. Here, the new version operates in parallel with the old – receiving all the live traffic. The new system is then fully validated before the old one is switched off.
Regardless of the strategy selected, data migration and user training must also be addressed. There are a number of types of data migration – storage location, new database, new application, migration to the cloud, business process change, and data center migration. A data migration team should be established, all data securely backed up, and the Extract/Transform/Load (ETL) process fully tested before the final cut date,
Phase 4: Maintenance
The Maintenance Phase begins once the system is in production. As systems and network administrators manage day-to-day operation, trouble-shoot problems, and tune the system, programmers will be fixing bugs, as well as developing enhancements. During the Maintenance Phase, fixes and enhancements are developed, tested, and applied as patches and updates.
As the business changes, the system also changes – for functionality, for scalability and performance, for security and resilience, or perhaps for regulatory compliance. Over time, systems may be updated and patched many times.
And remember that the underlying vendor systems software, hardware, and cloud platforms will also go through their own changes as technology ages and evolves. Eventually, the whole combination may become unwieldy, outdated, and expensive to operate, and needs to be replaced.
Phase 5: Decommissioning
The final stage of System Life Cycle Management is Decommissioning, as the system reaches the end of its useful life. Typically the Decommissioning Phase follows the Implementation Phase of the system replacing the original.
Decommissioning entails the shutting down and disposal of physical equipment. Following that, systems and network administrators must remove it from all relevant systems and network configuration, routing and security tables.
There may be regulatory requirements related to the equipment and data it contains. Data must be removed and transferred to the new system as appropriate and/or archived as necessary for compliance. Once the data has been moved out, the original storage areas should be purged and sanitized according to industry practices. The decommissioning may need to be audited for the purposes of compliance.
As a final step in the Decommissioning Phase, a “lessons learned” review should be performed and findings documented for subsequent decommissioning teams.
Conclusion
Systems and network admins are involved from the earliest system life cycle management planning phase, then during the development and deployment phases, throughout production operations, and all the way to decommissioning.
Learn more about System Life Cycle Management by taking our CBTNuggets CompTIA Network+ online training course.
Don’t have a CBT Nuggets’ subscription? Try us out with a free 7-day trial.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.