What is the Cisco ASA and How Does It Work?

Quick Definition: An Adaptive Security Appliances, or ASA, is a piece of cybersecurity hardware sold by Cisco. ASAs are multi-purpose security devices. They boast firewall, antivirus, intrusion protection and VPN capabilities.
A Quick Overview of Cisco ASA [VIDEO]
In this video, Keith Barker explains what an ASA is, its most important features, and how they operate. Learn firewall essentials — whether that's stateful inspection, creating dynamic exceptions, keeping user traffic secure and fast-moving, or what NATs or PATs do in translating IPs.
How Does an ASA Secure a Network?
A Cisco Adaptive Security Appliance's (ASA) default behavior is to prevent all external traffic from entering a network. Rogue actors can't perform mischief if they never get in from the outside in the first place. But Cisco has also built ASAs to have highly intelligent and robust capabilities that can recognize permissible traffic of many different types.
In the world of cybersecurity, there are many types of protection. Different hardware and software solutions offer unique protections. A Cisco Adaptive Security Appliance, or ASA, is especially powerful because it bundles many features and capabilities into one network security device.
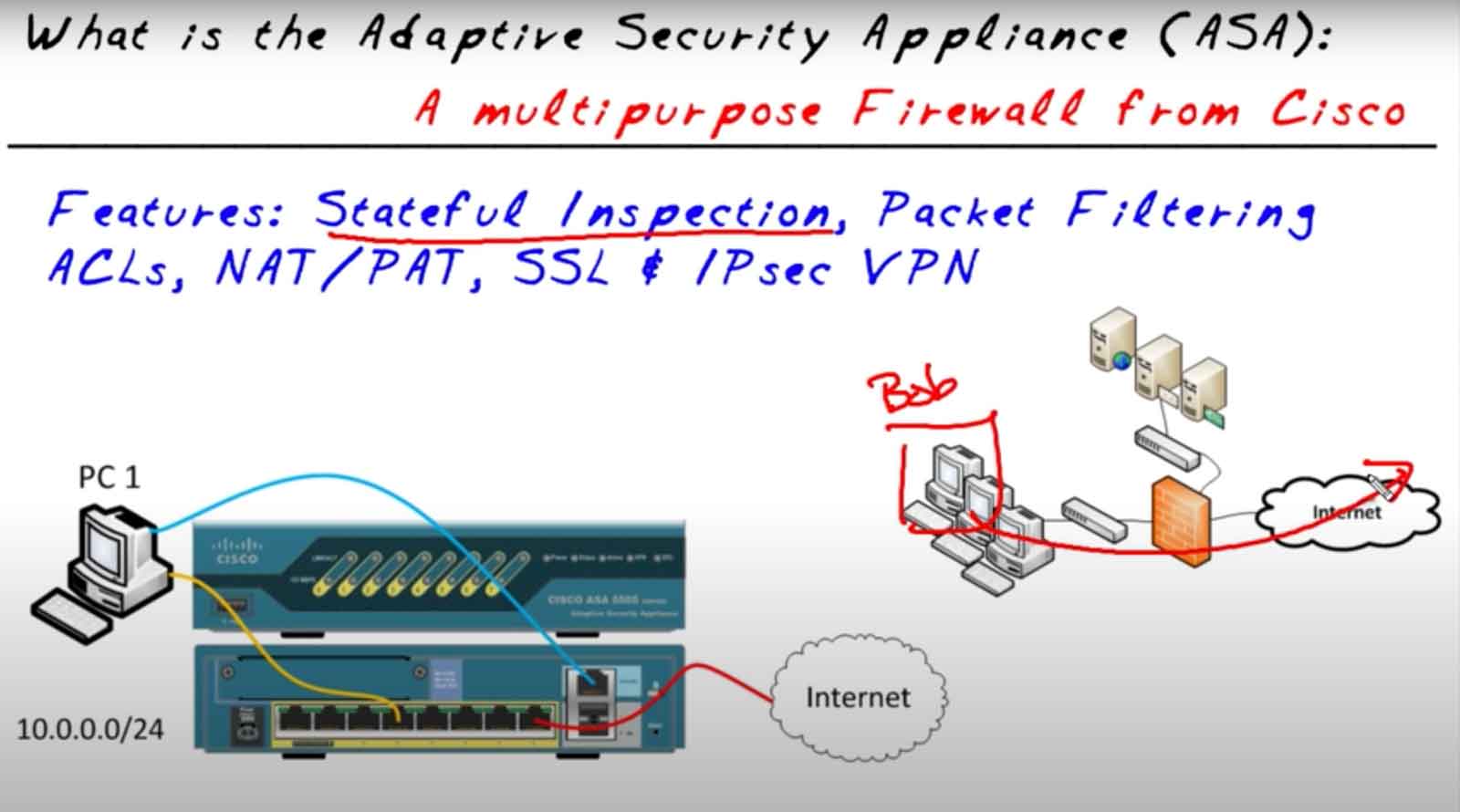
To understand what an ASA does on a network, let's picture one. Imagine a network and give it an "inside" zone and a "de-militarized zone" (DMZ) of several servers that touch the internet, then put an ASA in-between the network and the Internet – protecting the entire network.
We all know that the outside world is a dangerous place. And so the ASA, by default, says that any traffic trying to come in from the outside, whether that's a user, a server or a system, is going to be denied at the connection to the ASA. When a network has an ASA protecting it, outside traffic gets stopped before it can even make its way to any device on the network.
The only way to keep a network absolutely safe is to allow absolutely no connection to the internet. But you can imagine why that's usually not very useful. Using the internet isn't optional for most companies — and that means users being able to leave the internal networks for the outside world and receiving replies. It also means allowing valid requests from the internet to reach web servers.
An ASA's default behavior may be to allow no packets through to either the inside zone or the DMZ, but it has a host of bells and whistles that make safe, valid interaction with the internet possible.
How Do ASAs Use Stateful Inspection?
When internal users make requests to the internet, an ASA saves session information so that when a valid response comes back, it can recognize and permit that traffic through. Stateful inspection is the mechanism that allows the ASA to do so.
Imagine a user on our internal network named Bob. Bob wants to go out to the internet, so he makes his request.
The traffic from that request goes out to the internet. Clearly, if Bob's ASA stopped all traffic from making it back into the network, it wouldn't be much more useful than never being plugged into the internet in the first place.
Because when Bob goes out to the internet, he's not just sending requests with no expectation of a response. For his internet connection to be useful, he'll need a reply. Bob is expecting a response back from an external server.
Remember, the default operation of an ASA is to deny traffic before it reaches the network. So if the firewall didn't allow the reply to Bob's request to come back in, no Internet. But when Bob's request leaves the network, the firewall does something amazing: in the background, it looks at Bob's session and remembers things.
It remembers the source IP address, destination IP address, Layer 4 information, and ports involved. And it puts all of that into a session table, a stateful session table. When the reply comes back, the firewall says, "Wait a minute, this reply is perfect! It exactly matches what Bob is expecting as a reply." And it dynamically makes an exception and lets that return traffic come back in.
With stateful inspection, you can have thousands of users all going out to the internet dynamically and allow all the return traffic while simultaneously stopping any traffic that's initiated on the outside from coming in.
How Does an ASA Make Use of Packet Filtering?
Packet filtering allows legitimate external users to make inbound requests to your web servers. An ASA protects internal networks by permitting valid packets into the DMZ — and only there.
Imagine a user out on the internet named Marie. Marie wants to come in and access one of your web servers. But the web server is behind your ASA in the DMZ. By default, that traffic won't be allowed to reach the web server. But maybe that's your company's store, or your sales catalog. You can't have it blocked off to the internet. Thankfully, there's packet filtering.
When packet filtering functionality is engaged, access lists get applied to an ASA's internet-facing interface. An access list instructs the ASA which traffic is permissible. When one gets applied, you're in effect telling the ASA, "Please allow traffic through if it's web traffic that's destined to a specific IP address associated with one of your web servers, but only let it go to that address, and only let those packets through."
With packet filtering set up on an ASA, internet users making valid requests can access public web servers. At the same time, we're never allowing external users from the outside into our inside zone. That's because everything we know about zone perspectives is maintained when dealing with packet filtering.
Do ASAs Have Network or Port Address Translation Capabilities?
An ASA can provide network address translation or port address translation so that all the devices sitting behind it appear to themselves to be on the 10.0.0.0 network. But requests to the internet get global routing addresses, and they're swapped out when they come back into the network.
If you were to look at your IP address right now on your computer, try "ipconfig" on Windows or "ifconfig" on Linux or Mac, it's very likely your device is on a 10 address or a 192.168-something. That's because those addresses are in the RFC 1918 address base. They're private and not allowed on the internet.
Service providers block those private addresses. Nevertheless, your devices believe that's where they can find themselves on your network. And that's thanks to another feature that ASAs also provide: NAT/PAT.
Network Address Translation (NAT) and Port Address Translation (PAT) is basically lying — lying about source IP addresses. The firewall itself will have a globally routable address like 23.1.2.3, but devices behind the ASA don't have one. But as traffic passes through the ASA, it uses NAT or PAT to translate the source addresses into the address the ASA has – and lie about where the request is coming from.
NAT and PAT make it so that those packets traverse the internet with the ASA's return address. And then, once a reply comes back, the ASA swaps out the destination with the internal address of the device that made the request in the first place.
Can You Build VPNs With an ASA?
Yes, Cisco Adaptive Security Appliances offer VPN support for SSL, IPsec, or both. VPN tunnels are much easier to establish and maintain with ASAs.
Say one of your employees, James, is out getting coffee and wants to connect to corporate headquarters. He has high speed connectivity through DSL or cable, but he wants to send confidential or sensitive information.
You wouldn't want James transmitting confidential information in plain text over the internet. That data could easily be leaked out and seen by someone who shouldn't see it. The solution is to build a VPN tunnel from James' machine with a remote access VPN to the ASA so that the leg of the journey from the café to the ASA is protected with either SSL or IPsec; they both do a terrific job.
Once the tunnel is built between his device and the ASA, he'll have full access to the same internal resources just as if he was on the local area network.
What Do ASAs Look Like?
Most ASAs are rack-mountable devices that resemble switches. In fact, many have physical switches built directly into them. The ASA 5505 is smaller than its sibling ASAs, but still comes equipped with an 8-port switch built into it. Two of the eight ports support power over ethernet, so if you had a camera or access point that needed to be powered, your ASA could support it.
The 5505 model is additionally powerful in that it supports virtual interfaces. You can create logical interfaces: one for the inside, one for the outside, one for the DMZ, and each of those interfaces correspond to a VLAN. So the ports can be assigned to the various VLANs based on which interface we want them to be associated with and it makes it very customizable and easy to work with.
Which is Better: The ASA GUI or CLI?
The ASA's Command Line Interface and Graphical User Interface are both very different ways to approach managing the device, but their differences also allow for different efficiencies and strengths. Some people love the GUI, while others prefer the CLI. But both have their place.
From the GUI perspective, there are some amazing time-saving tools available. Of course, all the device's individual details are configurable from either place, but imagine you were looking to roll out something like AnyConnect, the SSL VPN support for remote access.
To configure that manually at the CLI is very doable. However, if you wanted to do the same config but quicker, there's a wizard for it in the GUI. Under the Wizards menu, hover over VPN Wizards and click AnyConnect VPN Wizard.
The AnyConnect VPN Wizard asks several questions. You put in the answers and it writes out the needed configuration for you. The great thing about working in the GUI is that you can put all the information in, get right to the very end, then rather than press "Okay", you can copy and paste the config data into Notepad, edit it, and tweak it before entering it manually into the CLI. This crash course in ASA functionality is only meant to whet your appetite for the security device. Managing and configuring Cisco's all-in-one firewall security appliance is a necessary tool in any netadmin's toolbelt, and there's a lot to know about customizing and tweaking an ASA's many strengths and capabilities.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.