SSL Encryption vs Authentication: What’s the Difference?

As of February 2021, 91% of the top 1,000 domains were using Hypertext Transfer Protocol Secure protocol, more commonly known as HTTPS. The protocol abbreviation before main domain addresses indicates that the website is secured by Secure Socket Layer (SSL). When you compare HTTPS websites to those without "S", HTTPS websites are more performant, secure, and advantageous for SEO.
Thanks to these benefits, more domains are adopting HTTPS. Understanding SSL and its underlying technologies will help organizations to properly operate or apply it. This post, among other SSL aspects, focuses on encryption and authentication.
What is SSL Encryption?
SSL is a protocol that defines how the data sent from a server is encrypted and decrypted on the client-side. This encryption method has been replaced by the more modern and secure Transport Layer Security (TLS), however, the term SSL is still used for the encryption protocol.
SSL is designed to protect data traveling over the internet by encrypting the contents. This prevents hackers and ill-intended entities from viewing the intercepted traffic. Because of its secure characteristics, SSL has become essential, especially for exchanging sensitive data such as passwords, payment details, and other personal information.
How does SSL Encryption Work?
SSL uses two encryption methods, asymmetric and symmetric, to protect the data in transit. Asymmetric method is used to make a secure connection between a client and a server. Symmetric encryption is then utilized to securely exchange data between the two.
For a website to use SSL encryption, it must have an SSL certificate. When a server has the certificate, the server can initiate encryption before sending data and the client can run decryption to interpret the transferred message. When the client leaves the website, the keys used to encrypt and decrypt are deleted. When a client visits the website again, new keys are generated, and the encryption and decryption processes are started.
Why is Decryption Important?
Encryption is a crucial process. It helps prevent sensitive messages from falling into wrong hands. However, decryption is also equally important. People may think that it is a process that allows a client-server to understand the message. It is way more than that.
As security measures become smarter, so do the ways hackers attempt to steal information. When they send harmful traffic, they do not surface malicious data so that the receiving ends simply can see them. They also use encryption to cover up their traffic. This makes decryption important since we can audit encrypted messages and accept only normal traffic.
What is Authentication in SSL?
SSL exists for secure data exchange between a server and a client. Before both sides actually start sending and receiving data, authentication processes begin. It is when authentication is normally finished that the client-side starts receiving data from the server.
Because it is the enabler of SSL protocol, implementing good authentication and understanding its processes can help organizations to enhance their security and protect their information. The server needs to verify that the visitor is a real and normal person who does not pose any harm to the website. Likewise, the client also needs to know if the website it is visiting is legitimate and secure, and will not illegally collect sensitive personal data.
Authentication processes
The SSL authentication processes follow the steps that require actions from both a server and a client.
A client (a person) visits an SSL website on a browser. The browser introduces the client to the website. The server sends its information and the browser collects it and verifies the information to ensure the legitimacy of the website.
When the browser considers it as a bad site, it will warn you saying that when you access the website, "attackers might be trying to steal your information".
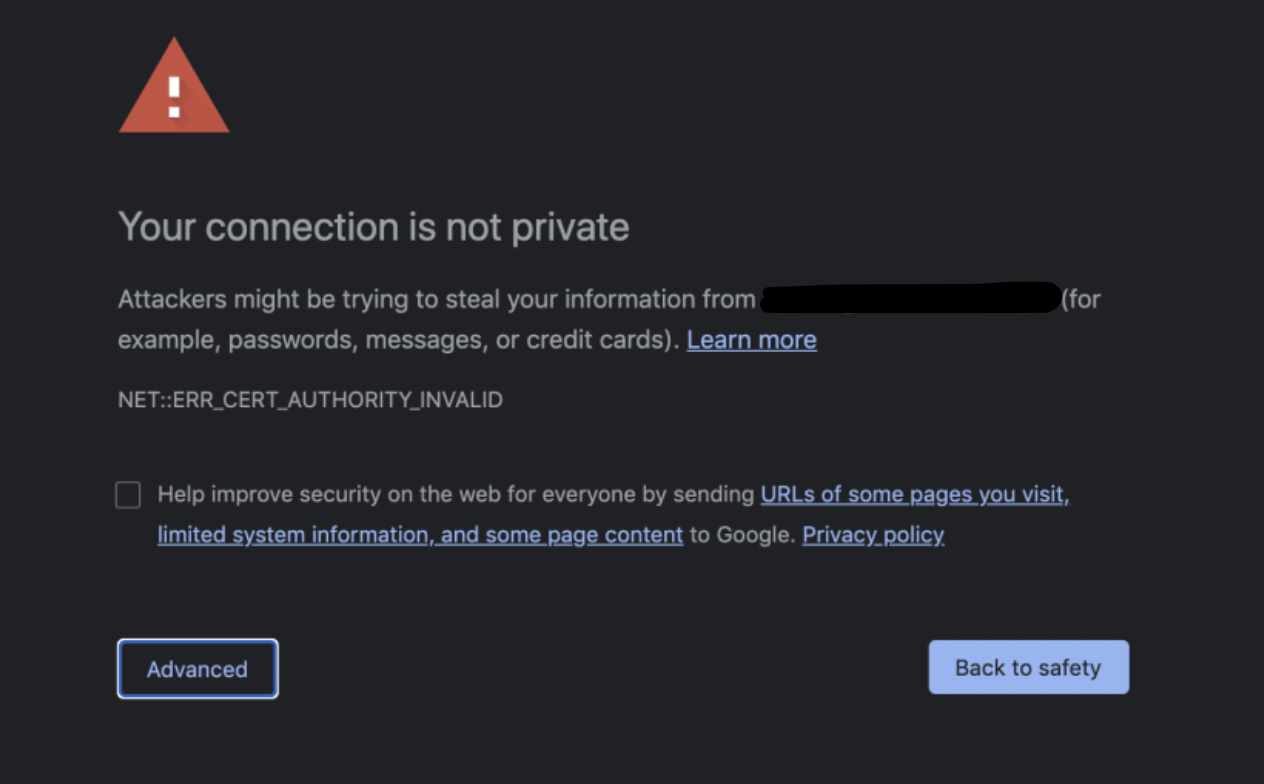
If your browser finds that the website is secure, the site shares its SSL certificate. If its SSL certificate is valid, it shares its public key and then starts encryption and data transfer.
Types of authentication
The high-level flow of authentication is explained above. When we want to take a deeper look, there are two types: one-way and two-way SSL authentication.
One-way server certificate authentication: The one-way authentication is also called server certificate authentication. It is the client that validates the server and the server does not attempt to verify the client. In the one-way SSL authentication, the server shares its public key with the client.
Two-way client authentication: In two-way authentication, both sides participate in verification. The client verifies and identifies the server and, then, the server does the same toward the client. Both ends share public certificates and carry out validation. The two-way SSL authentication exchange the certificates to handshake each other.
What is an SSL Certificate?
When we learned SSL authentication, one term that frequently appeared was SSL certificate. The certificate plays a key role in authentication so let's have a look at it.
An SSL certificate exists in the form of a digital file that contains a server's (or website's) identity, domain address, server name, and more. Since an SSL certificate contains such detailed information about a server, it is used to authenticate and start encrypting messages. Websites that are secured by an SSL certificate have the domain address with HTTPS. By checking that part, we can know that the website is protected by an SSL certificate and is considered a secure domain. Acquiring an SSL certificate is the condition to get the HTTPS address. Besides security reasons, there are more factors that drive companies to adopt a certificate.
In 2014, Google announced that its ranking algorithm will give more scores to the websites that have an SSL certificate over those that do not. It largely impacted the SEO domain since a failure to implement SSL can lead to a lower ranking in Google search results. To avoid the consequences, the majority of the websites searched through Google are reported to have an SSL certificate.
Public Keys vs. Private Keys
Other terminology that appears frequently when discussing SSL encryption and authentication are public and private keys. In SSL protocol, in addition to an SSL certificate, we use a pair of private and public keys to authenticate and establish a secure connection.
When you obtain an SSL certificate, you also create your CSR or Certificate Signing Request, which allows you to generate a pair. In SSL, the public key is open to the public while the private key is kept secret and only accessible by the owner. The private key can be used to access your server. When a person can enter a server, the person can gain the freedom to manipulate what is inside the server, not to mention being able to view any data.
Because of the potential risk, it is a good practice to limit the users that can use a private key and it also has to be safely managed. In contrast, the public key can be shared with the public. An SSL certificate public key information. A pair of private and public keys work together to enable data encryption and verification. By this process, we can guarantee that our data is transferred safely.
SSL Encryption vs. Authentication
We now understand that SSL encryption and authentication are two separate concepts. SSL encryption is an activity to prevent unauthorized parties from reading and comprehending the message in transit. Authentication is a set of processes to identify and validate a client or/and a server before making a secure connection. Once authenticated, we then start encryption and exchanging data. This is the gist of the differences between the two.
Final Thoughts
The post discussed SSL encryption and authentication. We learned the concept of the two important elements in SSL and how they work. Two key components in SSL were frequently mentioned: SSL certificate and public and private key.
Amid the growing trend of adopting SSL, understanding these concepts and processes will help you to raise awareness of security and further enhance security literacy. Moreover, acquiring this knowledge will assist you in properly planning SSL implementation — and sharing the importance of SSL and security in general within your organization. Learn more by signing up with CBT Nuggets!
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.