How to Troubleshoot a Failed Ping Request

Network connectivity is one of the foundational requirements for any network deployment. Configuration and responding to ping requests ensures the availability of the network. The ping is useful for testing, such as ensuring that routing is working and so forth.
ICMP and ping messages, on the other hand, might be utilized against us in a network discovery and system assault. In this post, we’ll look at how to troubleshoot a failed ping request in Palo Alto firewalls.
The structure of your network will have a big impact on the troubleshooting procedure. Keeping track of the whole network and determining the cause of problems might feel hard if you have a complicated hybrid network structure. To narrow in on what’s causing the problem, use a deliberate approach to troubleshooting and use the correct tools.
How to Troubleshoot Network Issues
For every organization, a network is one of the pillars of IT infrastructure. When a network is built, there may be network connectivity issues that need to be resolved as soon as possible.
When it comes to troubleshooting network issues, there are two fundamental processes to follow:
Check the Network Hardware. Ensure sure your network is free of physical issues, such as a wire that hasn't been disconnected or a switch switched off. After you’ve double-checked the physical connections, rebooting your network devices sometimes works.
Be sure to check that all servers and associated hardware are working correctly by turning routers on and off.
Use Command Prompt. If everything is in working order with the hardware, use the Windows Command Prompt to manually troubleshoot network difficulties.
Ping and tracert: In many situations, minor issues may be solved with programs like ping and tracert. The ping program can check for basic connection and measure latency between the requesting and destination hosts. It may be used to see whether there’s an issue with your company’s network, or between your network and the internet. Tracert may then be used to examine how rapidly a packet flows between each node on the network by looking at the precise hops it takes as it travels from the requesting host to the destination host. Combining these techniques can assist you in determining where the problem is occurring on the network.
ipconfig and nslookup. The IP address of each host on the network is determined using ipconfig, which is useful for diagnosing network issues such as IP address conflicts. Problems with the Domain Name Mechanism (DNS), the system that maps domain names to IP addresses, might potentially cause network troubles. If the DNS configuration is incorrect, the domain name and the accompanying IP address cannot be reconciled, and you are unable to access the website or service. If the nslookup utility fails to find the IP address(es) connected with a domain name, you know there’s a problem with the DNS.
netstat. The netstat utility displays a host’s active network connections as well as their status. It can reveal port issues and assist in determining how much traffic is flowing over the network.
How to Troubleshoot a Ping Request
One of the most fundamental tasks that every network engineer or network technician must perform is the troubleshooting of ping requests in Palo Alto firewalls. ICMP and ping messages might be used against us for network discovery or to attack our systems, hence they are disabled by default.
So on its data plane interfaces, the Palo Alto firewall’s default attitude is that if someone sends a ping, it won’t react. Let's walk through where we’d go in the Palo Alto firewall to set or adjust that behavior.
The data plane interfaces ethernet1/1 and 1/3 in the following configuration are both not receiving ping requests. They also refuse to accept or enable others to communicate with them in order to manage the box.
For the time being, the only way to administer this Palo Alto firewall is through the management interface, which does accept pings. By default, it only allows HTTPS and SSH sessions on the administration interface.
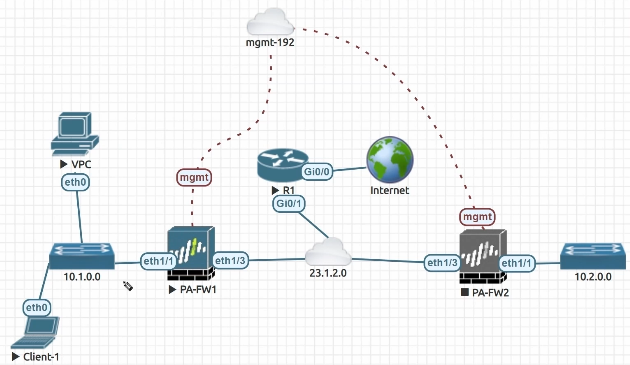
Figure: A Network Topology for Troubleshooting Ping
How to Troubleshoot a Ping Request in Palo Alto Firewall
Only firewalls running PAN-OS 9.0 or later versions may execute the ping troubleshooting test. So if we wanted to modify the behavior of pings or management access on data plane interfaces, we need to use the procedure listed below:
Step 1: Navigate to the Network tab.
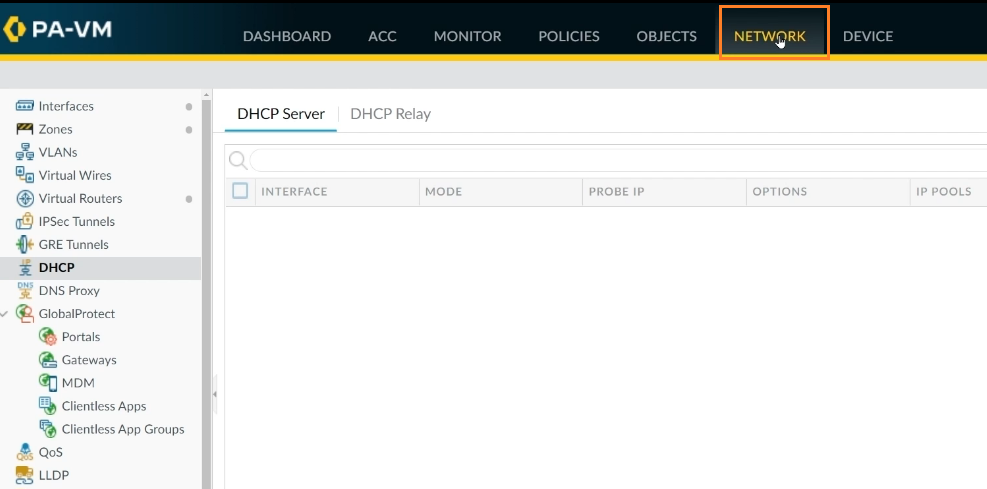
Step 2: From the left pane, choose Interfaces. In terms of interfaces, we have ethernet1/1 for the internal network and ethernet1/3 for the outside network.
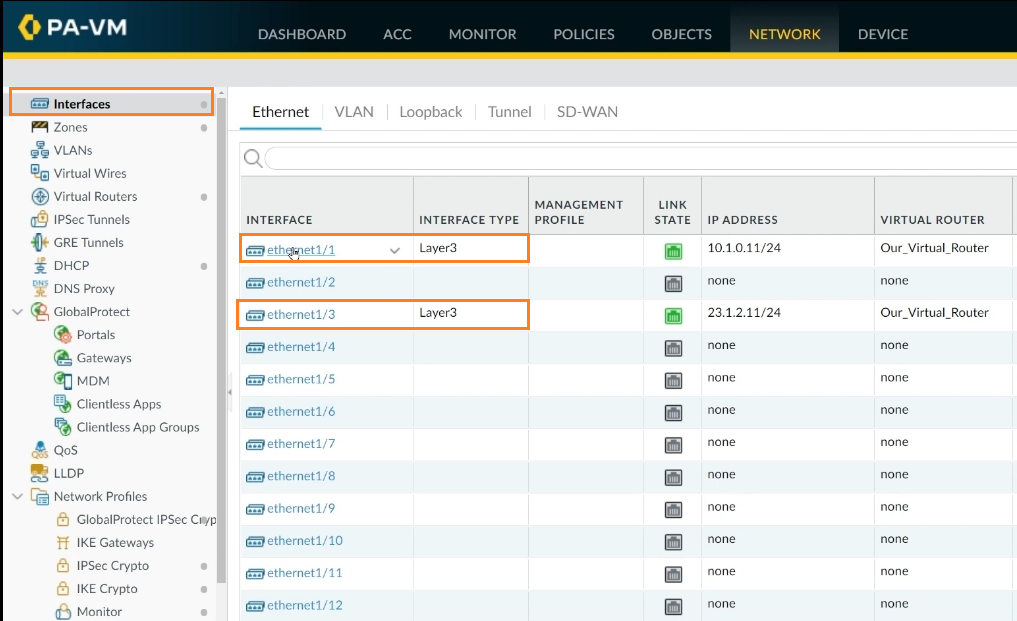
If you go to interface 1/1, which is now the interface that won’t allow a ping response, we can alter it.
Step 3: Select Interface 1/1 -> Advanced -> Management Profile from the menu.
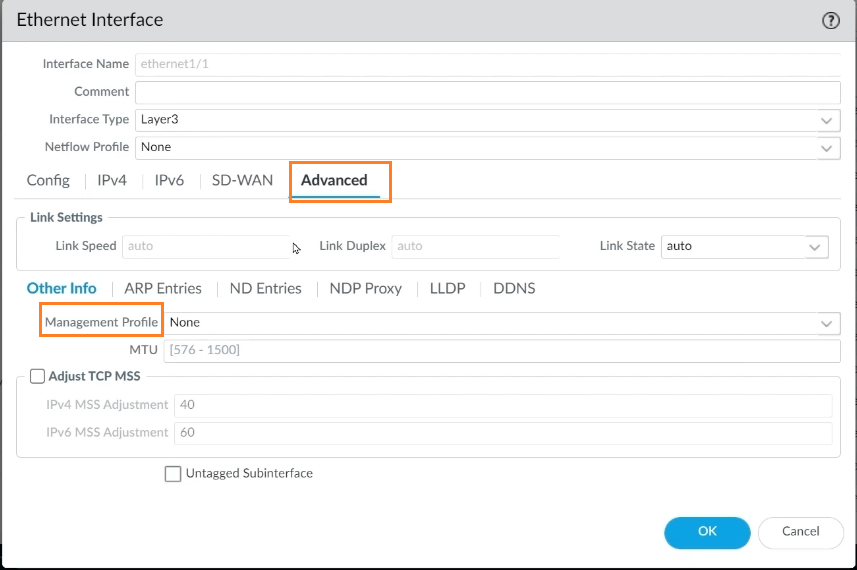
It cannot be allowed to ping any interface without a Management Profile linked with this interface (ethernet1/1).
We’ll need to create a Management Profile to tackle this problem.
Step 4: Click on the drop-down menu of Management Profile, and select New Management Profile to create a new one.
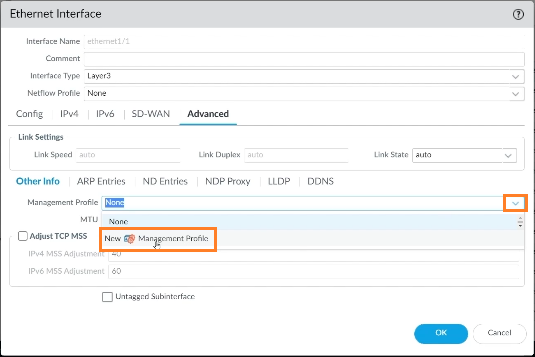
A new Management Profile can also be created from Interface Mgmt for this:
Step 5: Select Network -> Interface Mgmt -> +Add from the menu..
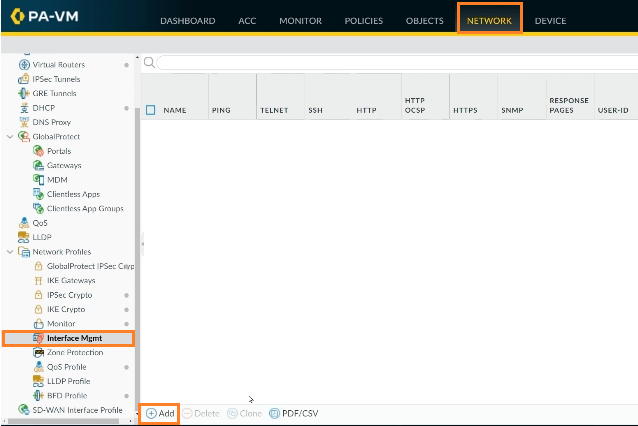
Step 6: For the Management Profile, give it a suitable name. Select Ping from the Network services menu then click on OK.
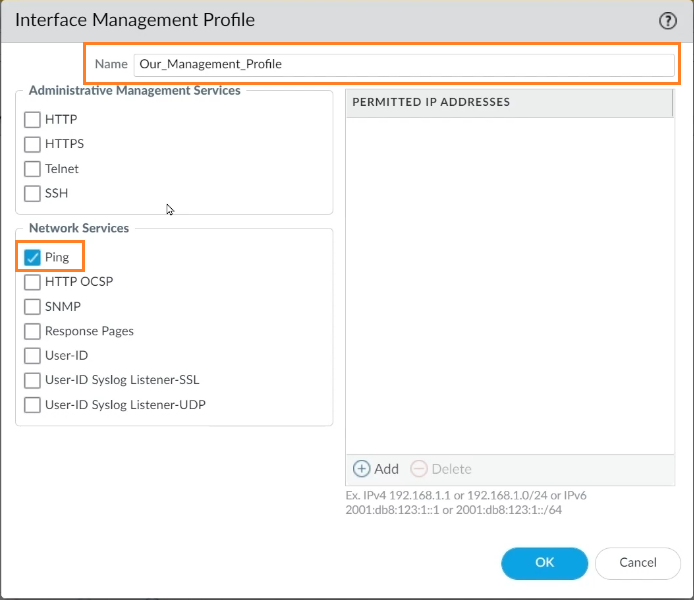
Once it is confirmed, any interfaces connected with this management profile will respond to ping requests. We could also use HTTPS and SSH to enable the ability to control, and connect to a data plane interface for management reasons, to administer this Palo Alto firewall. As a result, HTTPS would be used for a browser and SSH for a command line.
The other two options, HTTP and Telnet in Administrative Management Services, are likewise GUI and command-line possibilities, but we don’t want to utilize them because they aren’t secure protocols. While traffic is flowing back and forth, they do not encrypt anything.
For this management profile, we’re only going to accept ping queries on any interfaces that are related to this management profile.
Then we’ll return to our Interfaces and choose the Management Profile that we just created. To do so, go to step 4 choose the newly established management profile, and click OK to continue.
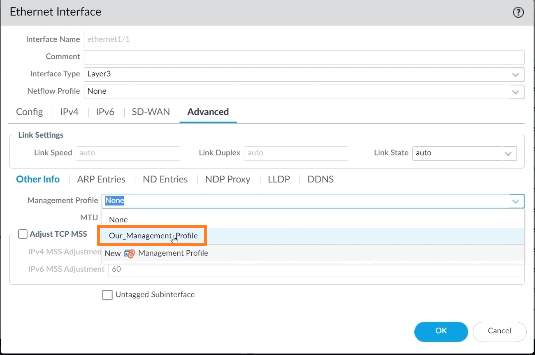
Then, if we want it to be in the running configuration, we must commit it, which means it will be moved from the candidate to the running configuration.
Step 7: To confirm, click Commit and then Commit again.
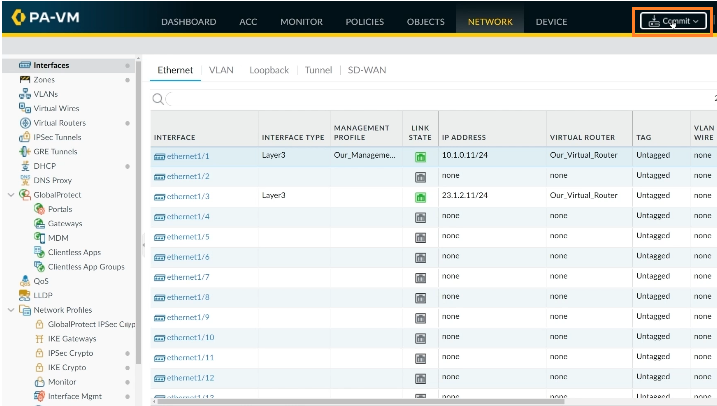
That will be completed in just a few seconds. Let’s close that window and bring in a new client. Ping the client’s IP 10.1.0.11 to see whether it responds.
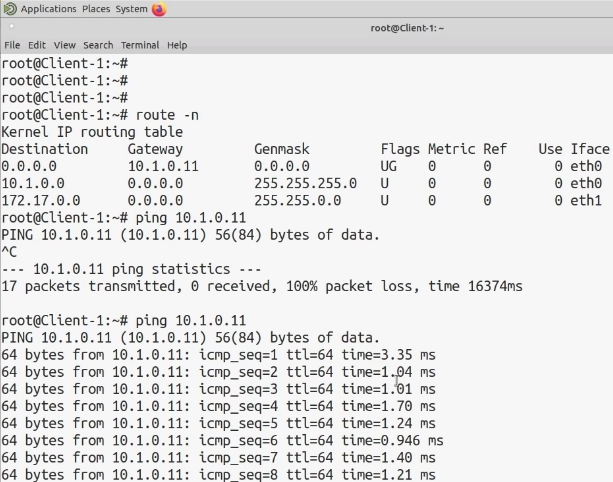
The ping request has now been completed successfully. We can now properly connect from the client to the Palo Alto firewall’s administration interface.
Wrapping Up
Even if you’ve previously troubleshooted networks, issues might creep up unexpectedly as those networks evolve. For example, a new device is introduced or devices interact in unexpected ways. Even experienced network administrators may find it difficult to pinpoint the specific location of the problem and how to resolve it.
Only Palo Alto firewalls running PAN-OS 9.0 or later versions support the ping troubleshooting test. To enable ping testing, you’ll need to create a Manage Profile in which you may enable several network services for testing network connections, such as HTTPS, SSH, OCSP, SNMP, User-ID, ping, and so on.
After you’ve created a Management Profile on the network interface you wish to ping from your preferred location, you can test the network connection by sending a ping request to that interface.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.