4 Factors to Consider When Deploying Palo Alto Virtual Firewalls

The VM-Series virtual firewalls from Palo Alto Networks may be used in both private and public cloud environments. They run the same version of PAN-OS as physical firewall appliances and provide the same basic functionality.
Depending on the capabilities of the hosting environment, some functionalities may not be available or implemented in different ways. Most public cloud suppliers, for example, only support Layer 3 interfaces for connecting to their virtual networks. The various levels of HA support in public cloud deployments are another example.
Some support-native offer HA connections utilizing two VM-Series firewalls, while others support scaling of parallel VM-Series firewall implementations with no HA settings. In this post, we’ll go over 4 considerations while deploying Palo Alto virtual firewalls in a cloud environment, which are covered in Section 1.2 of the PCNSE Blueprint.
Palo Alto Virtual Firewalls
The Palo Alto Networks Next-Generation Firewall VM-Series is a virtualized version of the next-generation firewall that may be used in both public and private cloud architectures. The same PAN-OS software runs on VM-Series firewalls as it does on appliances, with the same features and capabilities. Depending on the cloud technology used, each environment provides the complete functionality of PAN-OS software with slight changes.
VM-50 (Lite), VM-50, VM-100, VM-200, VM-300, VM-500, VM-700, and VM-1000-HV are the versions of the VM-Series firewalls that can be deployed in cloud environments.
The following virtualization environments are supported by Palo Alto VM-Series firewalls:
Amazon Web Services
Cisco ACI
Citrix NetScaler SDX
Google CloudPlatform
KVM
Microsoft Azure
Microsoft Hyper-V
OpenStack, and
VMware products include VMware ESXi, VMware NSX, and VMware vCloud Air.
The following cloud-native infrastructures are also supported by the VM-Series firewalls:
Alibaba Cloud
Amazon Web Services
Docker EE
Google CloudPlatform
IBM Cloud
Kubernetes
Microsoft Azure
Rancher
Red Hat OpenShift, and
VMware Tanzu
License Requirements
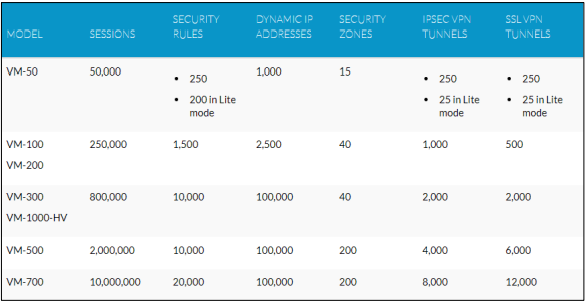
To enable full firewall capability, all Palo Alto VM-Series firewalls require a capacity license. The model number and related capacities are applied on the VM-Series firewall once you apply for the capacity license.
The number of sessions, rules, security zones, address objects, IPSec VPN tunnels, and SSL VPN tunnels that the VM-Series firewall can manage is measured in capacity.
You can use the table below to understand the maximum capacity for each model as well as the capacity differences across models to ensure that you acquire the suitable model for your network requirements:
What to Consider When Deploying Palo Alto Firewalls
The following are the four factors to consider in regard to Palo Alto virtual firewall installations:
1. Private Cloud Deployment
The virtual firewall of the VM-Series is based on private cloud technology where an appropriate virtual appliance or OVA can be downloaded from the Palo Alto Networks Support Portal, uploaded to the cloud, and then deployed and configured to meet the requirements of each private cloud architecture. These virtual firewalls are unlicensed, and therefore need a capacity code as well as the application of feature licenses after installation.
2. Public Cloud Deployment
Virtual firewalls are available through public cloud markets. Most public cloud markets provide three virtual firewall options, each with its own set of license requirements.
Bring Your Own License (BYOL): A Bring Your Own License (BYOL) version is an unlicensed VM-Series firewall that requires the client to deliver capacity code and feature licenses that were obtained separately after provisioning.
VM-Series Bundle 1: The VM-Series Bundle 1 contains pre-licensed VM-300s. Only Threat Prevention is pre-licensed in Bundle 1.
VM-Series Bundle 2: Threat Prevention, WildFire, URL Filtering, and Global Protect are all pre-licensed in the VM-Series Bundle 2.
The cloud vendor charges a use fee per hour of operation for the VM-300 Bundle 1 and Bundle 2 editions. There are no premium rates in the BYOL setup above the expenses of the component cloud resources.
The cloud vendor application stores’ preconfigured VM-Series firewalls typically include three interfaces: one for administration and one for trusted and untrusted network traffic connections. Most cloud deployments allow you to change the configuration by adding interface connections that are subject to the cloud vendor’s techniques and capacities.
3. Hybrid Cloud Deployment
Hybrid cloud is a cloud computing infrastructure that combines private and public cloud services with orchestration between them. For cloud installations in both models, the VM-Series firewall delivers a fully-featured next-generation firewall solution.
Each public and private cloud deployment has its own set of design and deployment concerns that must be taken into account. Regardless of the type of deployed environment, centralized monitoring, reporting, and administration must be addressed. If the requisite communication channels are created, the Panorama management system can be installed in either type of cloud and can manage across cloud borders.
Connectivity in Hybrid Cloud Deployment
Panorama and firewalls both require the public network (internet) to access external services such as WildFire and to consume updates such as dynamic updates. When Panorama is used to control firewalls, the devices must communicate through a compliant channel.
Hybrid deployments don’t come with their own set of communication needs. Each environment must be designed to offer sufficient connection through its virtual networking environments as needed. The usage of the firewall to link cloud environments with any needed routing responsibilities might be part of engineering.
Cloud-based virtual networks frequently utilize site-to-site VPNs to connect them. Palo Alto Networks firewalls can be used as endpoints for these VPN connections, and they must adhere to VPN design and configuration guidelines.
4. Container Deployment
When compared to older programs, container architecture has various security problems and needs. Your main issue with virtual machines is securing a host OS, a guest OS, and a guest application environment. There are just a few layers of software in virtual machines.
Containerized environments have a lot more abstraction levels, which necessitates the use of specific tools to understand, monitor, and defend these new programs. As a result, you’ll need to secure several levels. Your program includes an orchestrator, a container registry, images, and, in most instances, many microservices in addition to the host OS and container runtime.
Finally, containerized apps complicate matters by altering the concept of protecting a single “perimeter”. This complexity necessitates novel methods to network layer security.
Images, containers, hosts, container runtime, registries, and orchestrators are all part of a container environment. You must be aware of the potential dangers and how to protect your environment from them. While working with containers, you should:
Compliance concerns and image vulnerability
Keeping the registry safe
Concerns about orchestration
Protecting Containers at runtime, and
Keeping the Host OS safe
Configuring VM-Series Firewalls
The virtual firewalls of the VM-Series may be used with a variety of public and private cloud technologies. Each deployment environment has its own set of features and needs. Some need the virtual appliance of the firewall to be uploaded. Others give it in a provided and configured Application Store.
Every VM-Series firewall uses the same PAN-OS software, regardless of the installed environment. There are special constraints and needs in some.
Final Thoughts
Palo Alto’s VM-Series virtual firewall may be used in a variety of cloud scenarios, including private, public, hybrid, and containers. To install any of these firewalls in your environment, you’ll need to buy a capacity license, which comes as part of a package and can be:
Perpetual License: A license with no expiration date that allows you to use the VM-Series firewall at the licensed capacity eternally. Perpetual licenses are only available for the VM-Series capacity license.
Term-Based License: You can utilize the VM-Series firewall for a certain amount of time with a term-based license. It has an expiration date, and you’ll be asked to renew it before it runs out. For capacity licenses, support entitlements, and subscriptions, term-based licenses are provided.
Before you launch and configure the VM-Series firewall to secure your cloud resources, consult the VM-Series Deployment Guide to learn about where you may install the firewall.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.